-
Notifications
You must be signed in to change notification settings - Fork 8.3k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Security Solution] Persistent Rules table state #140263
Comments
|
Pinging @elastic/security-solution (Team: SecuritySolution) |
|
Pinging @elastic/security-detections-response (Team:Detections and Resp) |
|
The task has been discussed with @banderror, @xcrzx and the other team members and based on the discussion the following decisions have been made
|
|
Thanks for the summary @maximpn After the call yesterday I sketched up what we agreed (it's a bit scrappy) but aligns with what you've said here I think. |
**Addresses:** #140263 ## Summary It implements rules table state persistence. Reopening or reloading of the page loads the same state as well as navigation from another page inside or outside the security plugin. https://user-images.githubusercontent.com/3775283/201983621-e57e8c64-d5fb-4111-92df-ebe912dada38.mov ## Details The changes persist the rules table state in the url and the session storage to be able to recover after navigation from another page. The following parameters are persisted - search term, tags and elastic vs custom filters - sorting field and sorting direction - page number **(only in the url)** and page size Page number is only persisted in the url. Avoiding persistence a page number in the session storage make the UX more predictable that users upon returning to the page expect the first page to be selected. Selection state is not persisted since it can lead to URL overflow problem. According to the different resources for example [this one](https://www.geeksforgeeks.org/maximum-length-of-a-url-in-different-browsers/) the maximum length should not exceed 2KB though Chrome supports URLs up to 2MB. Besides that this PR adds - unit tests which coved edge cases - basic Cypress tests What is not done and will be addressed in the next PRs - persistence of the selected tab as a path segment in the url - comprehensive Cypress tests covering edge cases - getting rid of the back button `< Rules` on the rule details page ## Edge cases Since parameters in the URL and the session storage can be modified by users it can lead to unexpected results or security risks. What have been tested and covered so far: - arbitrary modification of the serialized state which leads to deserialization error (default parameters are used in this case and the state is rewritten with the default parameters) - filter parameters modification (doesn't cause errors) - page number modification (isn't not handled in a special way, `EuiBasicTable` display either first of the last page if the value exceeds the limits) - page size (`EuiBasicTable` loads more records which isn't limited and can cause a performance issue, it **has been addressed** through validation) - sorting parameters modification (`EuiBasicTable` ignores wrong values) The observation result is that `EuiBasicTable` gracefully handles the wrong values . ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios
Addresses: #140263 ## Summary It persists rules table selected tab in a path segment. ## Details It extends rules path segment to persist the selected rules table tab. So this way - `rules/management` represents `Rules` tab - `rules/monitoring` represents `Rule monitoring` tab Global navigation link and security manage page link leading to the rules table weren't updated. Instead a redirect from `rules` to `rules/management` was added. It allows to avoid significant refactoring since rules page is also a parent page in the routing mechanism which is also used for building breadcrumbs for the rule creation and rule details pages. It looks wise to address refactoring for rules page routing in a separate PR since it mostly makes sense if breadcrumbs extension for the rules page is needed. ### Video https://user-images.githubusercontent.com/3775283/209558995-1b9f82a3-aa56-4f27-916e-f0ebcd8c52c6.mov ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios - [x] Any UI touched in this PR is usable by keyboard only (learn more about [keyboard accessibility](https://webaim.org/techniques/keyboard/)) - [x] Any UI touched in this PR does not create any new axe failures (run axe in browser: [FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/), [Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US))
**Addresses:** #140263 ## Summary It removes navigation back to the rules table page link as it was [discussed](#140263 (comment)). To return back to the rules table page users intend to use either breadcrumbs or web browser navigation back button. Before:  After: 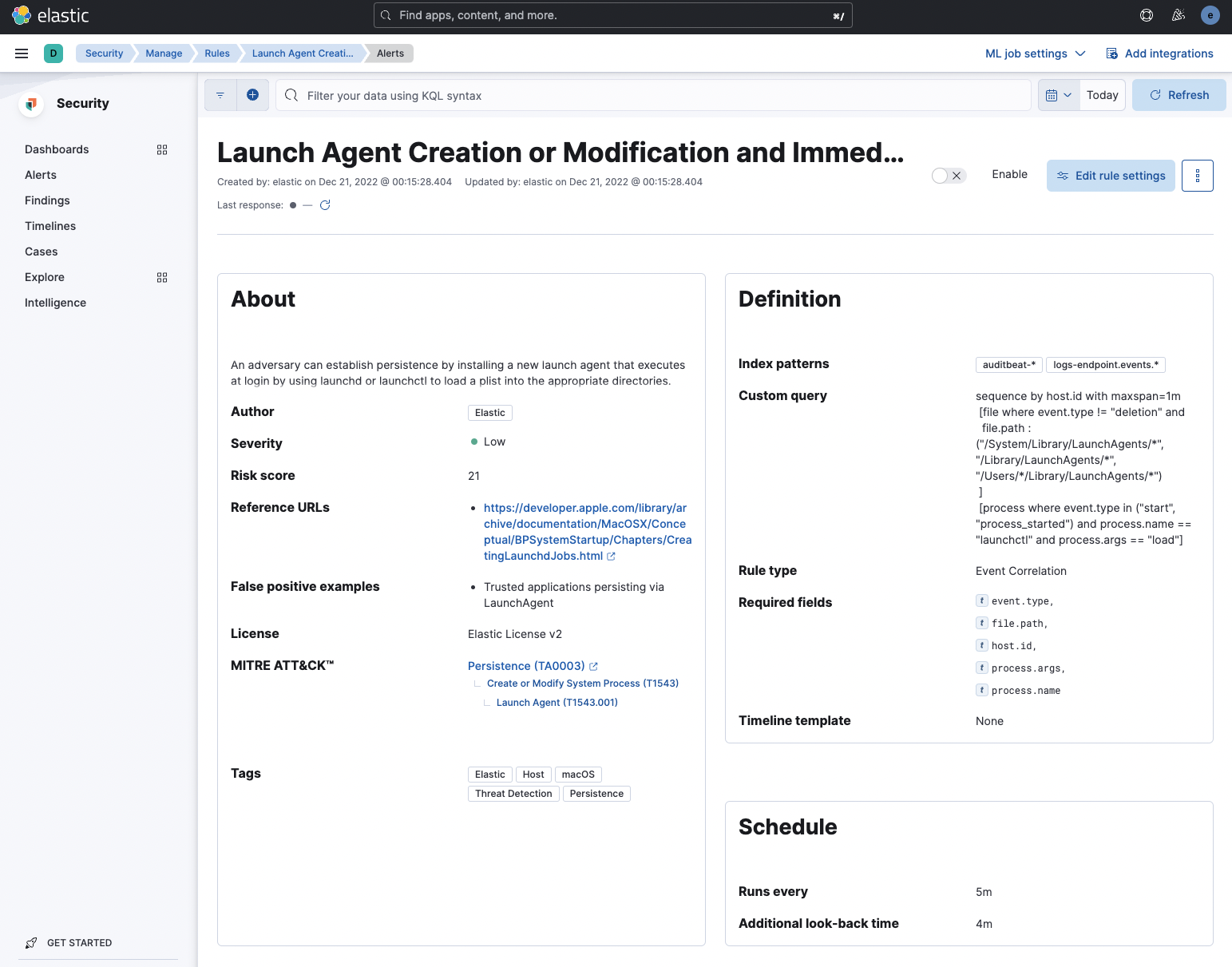 ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios
…147218) Addresses: #140263 This PR was inspired by #146649 and while working on persistent rules table state #145111. ## Summary It includes improvements for url search parameters manipulation functionality. In particular `useGetInitialUrlParamValue` and `useReplaceUrlParams` hooks. The main idea is to isolate the encoding layer ([rison](https://github.com/Nanonid/rison)) as an implementation detail so `useGetInitialUrlParamValue` and `useReplaceUrlParams` consumers can just provide types they wish and the hooks serialize/desirealize the data into appropriate format under the hood. On top of that after `@kbn/rison` was added in #146649 it's possible to use this package directly to encode and decode parameters whenever necessary. The improvements include - store unserialized url parameters state in the redux store - encode and decode data by using functions from `@kbn/rison` directly - let `useReplaceUrlParams` accept an updater object ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios
…149508) **Relates to**: #140263 ## Summary This PR migrates custom tags selector implementation on the rules page which mimics EuiSelectable to **EuiSelectable**. Besides simplification it brings keyboard and accessibility support as well as simplifies accessing the component in e2e tests. *Before:* https://user-images.githubusercontent.com/3775283/214831542-737aa9cf-8f76-4777-a23f-cbbfe0a01825.mov *After:* https://user-images.githubusercontent.com/3775283/214831568-e0809fd7-3c17-4789-8d3a-9ecbe379fb56.mov ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios - [x] Any UI touched in this PR is usable by keyboard only (learn more about [keyboard accessibility](https://webaim.org/techniques/keyboard/)) - [x] Any UI touched in this PR does not create any new axe failures (run axe in browser: [FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/), [Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US)) - [x] This renders correctly on smaller devices using a responsive layout. (You can test this [in your browser](https://www.browserstack.com/guide/responsive-testing-on-local-server)) - [x] This was checked for [cross-browser compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
…lastic#149508) **Relates to**: elastic#140263 ## Summary This PR migrates custom tags selector implementation on the rules page which mimics EuiSelectable to **EuiSelectable**. Besides simplification it brings keyboard and accessibility support as well as simplifies accessing the component in e2e tests. *Before:* https://user-images.githubusercontent.com/3775283/214831542-737aa9cf-8f76-4777-a23f-cbbfe0a01825.mov *After:* https://user-images.githubusercontent.com/3775283/214831568-e0809fd7-3c17-4789-8d3a-9ecbe379fb56.mov ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios - [x] Any UI touched in this PR is usable by keyboard only (learn more about [keyboard accessibility](https://webaim.org/techniques/keyboard/)) - [x] Any UI touched in this PR does not create any new axe failures (run axe in browser: [FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/), [Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US)) - [x] This renders correctly on smaller devices using a responsive layout. (You can test this [in your browser](https://www.browserstack.com/guide/responsive-testing-on-local-server)) - [x] This was checked for [cross-browser compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
…0059) **Addresses:** #145968 ## Summary This PR adds functionality to clear persisted rules table state implemented in #140263. https://user-images.githubusercontent.com/3775283/216311325-e19e81e1-f232-4c16-b9df-a49fcc8c98d0.mov ### Checklist - [x] Any text added follows [EUI's writing guidelines](https://elastic.github.io/eui/#/guidelines/writing), uses sentence case text and includes [i18n support](https://github.com/elastic/kibana/blob/main/packages/kbn-i18n/README.md) - [ ] [Documentation](https://www.elastic.co/guide/en/kibana/master/development-documentation.html) was added for features that require explanation or tutorials - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios - [x] Any UI touched in this PR is usable by keyboard only (learn more about [keyboard accessibility](https://webaim.org/techniques/keyboard/)) - [x] Any UI touched in this PR does not create any new axe failures (run axe in browser: [FF](https://addons.mozilla.org/en-US/firefox/addon/axe-devtools/), [Chrome](https://chrome.google.com/webstore/detail/axe-web-accessibility-tes/lhdoppojpmngadmnindnejefpokejbdd?hl=en-US)) - [x] This renders correctly on smaller devices using a responsive layout. (You can test this [in your browser](https://www.browserstack.com/guide/responsive-testing-on-local-server)) - [x] This was checked for [cross-browser compatibility](https://www.elastic.co/support/matrix#matrix_browsers)
…149638) **Relates to:** #140263 ## Summary This PR adds Cypress e2e tests to cover persistent rules table state functionality. ## Details It implements a test plan for the persistent rules table state functionality and includes some improvements to the other e2e tests to facilitate writing tests - `visit()` helper function input parameters were changed to match `cy.visit()`. It allows to pass a query string via `qs` and use the other fields. - added a skip agent installation step in `installAwsCloudFrontWithPolicy ` used in `detection_rules/related_integrations.cy.ts`. The agent installation screen started appearing after changes to the `visit()` helper function. It looks like a bug since url `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront` was concatenated with `timeline=...` query string inside `visit()` and `cy.visit()` finally invoked with `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront?timeline=...`. Fixing that cause test to fail due to agent installation screen. - use default type delay for `NOTES_TEXT_AREA` in `timelines/creation.cy.ts`. It looks that zero typing delay caused test flakiness. - selectors and helper functions were reorganized to facilitate its usage. ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios
…lastic#149638) **Relates to:** elastic#140263 ## Summary This PR adds Cypress e2e tests to cover persistent rules table state functionality. ## Details It implements a test plan for the persistent rules table state functionality and includes some improvements to the other e2e tests to facilitate writing tests - `visit()` helper function input parameters were changed to match `cy.visit()`. It allows to pass a query string via `qs` and use the other fields. - added a skip agent installation step in `installAwsCloudFrontWithPolicy ` used in `detection_rules/related_integrations.cy.ts`. The agent installation screen started appearing after changes to the `visit()` helper function. It looks like a bug since url `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront` was concatenated with `timeline=...` query string inside `visit()` and `cy.visit()` finally invoked with `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront?timeline=...`. Fixing that cause test to fail due to agent installation screen. - use default type delay for `NOTES_TEXT_AREA` in `timelines/creation.cy.ts`. It looks that zero typing delay caused test flakiness. - selectors and helper functions were reorganized to facilitate its usage. ### Checklist - [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios (cherry picked from commit 513a1f0)
…ests (#149638) (#151875) # Backport This will backport the following commits from `main` to `8.7`: - [[Security Solution] Cover persistent rules table state by e2e tests (#149638)](#149638) <!--- Backport version: 8.9.7 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"Maxim Palenov","email":"maxim.palenov@elastic.co"},"sourceCommit":{"committedDate":"2023-02-22T13:46:50Z","message":"[Security Solution] Cover persistent rules table state by e2e tests (#149638)\n\n**Relates to:** https://github.com/elastic/kibana/issues/140263\r\n\r\n## Summary\r\n\r\nThis PR adds Cypress e2e tests to cover persistent rules table state functionality.\r\n\r\n## Details\r\n\r\nIt implements a test plan for the persistent rules table state functionality and includes some improvements to the other e2e tests to facilitate writing tests\r\n\r\n- `visit()` helper function input parameters were changed to match `cy.visit()`. It allows to pass a query string via `qs` and use the other fields.\r\n- added a skip agent installation step in `installAwsCloudFrontWithPolicy ` used in `detection_rules/related_integrations.cy.ts`. The agent installation screen started appearing after changes to the `visit()` helper function. It looks like a bug since url `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront` was concatenated with `timeline=...` query string inside `visit()` and `cy.visit()` finally invoked with `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront?timeline=...`. Fixing that cause test to fail due to agent installation screen.\r\n- use default type delay for `NOTES_TEXT_AREA` in `timelines/creation.cy.ts`. It looks that zero typing delay caused test flakiness.\r\n- selectors and helper functions were reorganized to facilitate its usage.\r\n\r\n### Checklist\r\n\r\n- [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios","sha":"513a1f0538b4c3641e87d6665790e8daaa3bb985","branchLabelMapping":{"^v8.8.0$":"main","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","backport:skip","Team:Fleet","Feature:Detection Rules","Team:Detections and Resp","Team: SecuritySolution","Team:Detection Rules","v8.8.0"],"number":149638,"url":"https://github.com/elastic/kibana/pull/149638","mergeCommit":{"message":"[Security Solution] Cover persistent rules table state by e2e tests (#149638)\n\n**Relates to:** https://github.com/elastic/kibana/issues/140263\r\n\r\n## Summary\r\n\r\nThis PR adds Cypress e2e tests to cover persistent rules table state functionality.\r\n\r\n## Details\r\n\r\nIt implements a test plan for the persistent rules table state functionality and includes some improvements to the other e2e tests to facilitate writing tests\r\n\r\n- `visit()` helper function input parameters were changed to match `cy.visit()`. It allows to pass a query string via `qs` and use the other fields.\r\n- added a skip agent installation step in `installAwsCloudFrontWithPolicy ` used in `detection_rules/related_integrations.cy.ts`. The agent installation screen started appearing after changes to the `visit()` helper function. It looks like a bug since url `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront` was concatenated with `timeline=...` query string inside `visit()` and `cy.visit()` finally invoked with `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront?timeline=...`. Fixing that cause test to fail due to agent installation screen.\r\n- use default type delay for `NOTES_TEXT_AREA` in `timelines/creation.cy.ts`. It looks that zero typing delay caused test flakiness.\r\n- selectors and helper functions were reorganized to facilitate its usage.\r\n\r\n### Checklist\r\n\r\n- [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios","sha":"513a1f0538b4c3641e87d6665790e8daaa3bb985"}},"sourceBranch":"main","suggestedTargetBranches":[],"targetPullRequestStates":[{"branch":"main","label":"v8.8.0","labelRegex":"^v8.8.0$","isSourceBranch":true,"state":"MERGED","url":"https://github.com/elastic/kibana/pull/149638","number":149638,"mergeCommit":{"message":"[Security Solution] Cover persistent rules table state by e2e tests (#149638)\n\n**Relates to:** https://github.com/elastic/kibana/issues/140263\r\n\r\n## Summary\r\n\r\nThis PR adds Cypress e2e tests to cover persistent rules table state functionality.\r\n\r\n## Details\r\n\r\nIt implements a test plan for the persistent rules table state functionality and includes some improvements to the other e2e tests to facilitate writing tests\r\n\r\n- `visit()` helper function input parameters were changed to match `cy.visit()`. It allows to pass a query string via `qs` and use the other fields.\r\n- added a skip agent installation step in `installAwsCloudFrontWithPolicy ` used in `detection_rules/related_integrations.cy.ts`. The agent installation screen started appearing after changes to the `visit()` helper function. It looks like a bug since url `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront` was concatenated with `timeline=...` query string inside `visit()` and `cy.visit()` finally invoked with `app/integrations/detail/aws-1.17.0/overview?integration=cloudfront?timeline=...`. Fixing that cause test to fail due to agent installation screen.\r\n- use default type delay for `NOTES_TEXT_AREA` in `timelines/creation.cy.ts`. It looks that zero typing delay caused test flakiness.\r\n- selectors and helper functions were reorganized to facilitate its usage.\r\n\r\n### Checklist\r\n\r\n- [x] [Unit or functional tests](https://www.elastic.co/guide/en/kibana/master/development-tests.html) were updated or added to match the most common scenarios","sha":"513a1f0538b4c3641e87d6665790e8daaa3bb985"}}]}] BACKPORT-->

Related to: #126085, #126086
Summary
Currently, when the user refreshes the Rule Management page or navigates to another page, the state of the Rules table gets lost. When the user returns to the Rule Management page, they need to recover their filters, sorting, pagination, etc from scratch.
We want to:
What do we mean by the Rules table state exactly:
RulesorRule MonitoringAcceptance Criteria
GIVEN the user is on the Rule Management page and has some initial Rules table state (according to the definition above):
Technical details
The suggestion is to make the table state persistent in two places:
Some thoughts:
Todo
The text was updated successfully, but these errors were encountered: