- Contents
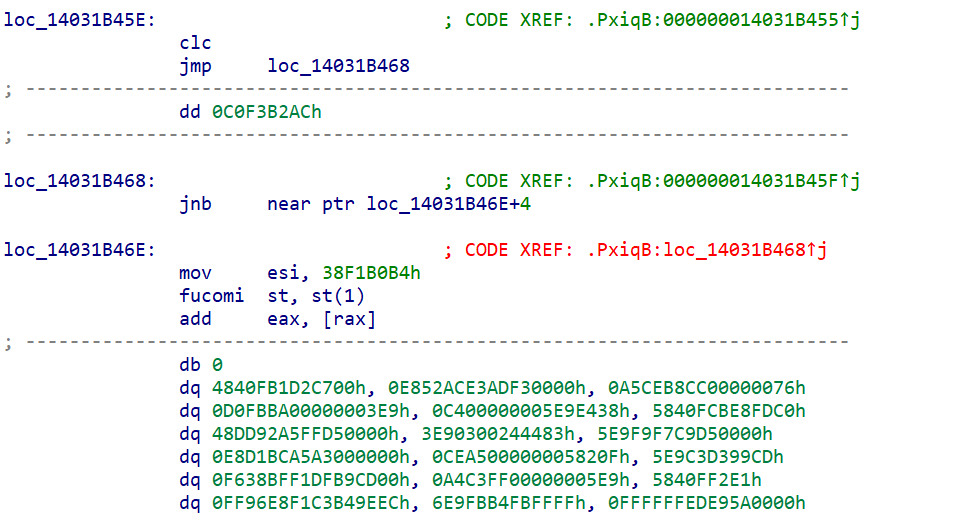
VxLang is a project designed to prevent reverse-engineering behaviors such as static or dynamic analysis, file tampering, and unauthorized access to memory by attackers.
The VxLang project currently targets x86-64 system and .NET binaries, native binary files for the Microsoft Windows operating system, including executables with the ".exe" extension, dynamic link library files with the ".dll" extension, and kernel driver files with the ".sys" extension. (The types of target binaries supported by vxlang will be expanded in future updates).
- Added beta code for the
ELFfile format.- The beta version only supports general
code-flattening. - Beta features require users to specify target code.
- VxLang recommends using the
-fno-picoption in ELF 32bit binary builds.
- The beta version only supports general
| Windows EXE/DLL | Windows Kernel Drive | ||
| Obfuscator |  |
Obfuscator |  |
| Virtualizer |  |
Virtualizer |  |
| Protector |  |
Protector |  |
| Windows UEFI Modules | Windows .NET | ||
| Obfuscator |  |
Obfuscator |  |
| Virtualizer |  |
Virtualizer |  |
| Protector |  |
Protector |  |
| Linux ELF | |
| Obfuscator |  |
| Virtualizer |  |
| Protector |  |
; x86-64 asm
cmp qword ptr [rsp + 0x20], rax
jae 0x140001bf5
mov rax, qword ptr [rsp + 0x20]
movzx eax, byte ptr [rsp + rax + 0x50]
; to v-asm
movi exr_0, ${RANDOM}
movi r7, ${RANDOM}
xorr r7, exr_0
movi exr_0, ${RANDOM}
movi exr_1, ${RANDOM}
xorr exr_0, exr_1
mulr r7, exr_0
addr r6, r7
movi exr_0, ${RANDOM}
movi r7, ${RANDOM}
xorr r7, exr_0
addr r6, r7
movr r0, r6
movr r1, rax
ldrr r2, r0
cmpr r2, r1
be 0x2c59
movr r0, rax
movr r6, rsp
movi exr_0, ${RANDOM}
movi r7, ${RANDOM}
xorr r7, exr_0
movi exr_0, ${RANDOM}
movi exr_1, ${RANDOM}
xorr exr_0, exr_1
mulr r7, exr_0
addr r6, r7
movi exr_0, ${RANDOM}
movi r7, ${RANDOM}
xorr r7, exr_0
addr r6, r7
movr r1, r6
ldrr r2, r1
movr rax, r2
; compile
e7 f8 f1 e5 01 e1 a2 9a 22 87 c3 93 61 e5 06 e1
a2 9a 22 87 c3 93 61 eb 06 01 e6 01 e0 a2 9a 22
e6 0a e1 a2 9a 22 ec 01 0a d6 06 01 da 07 06 e5
01 e1 a2 9a 22 87 c3 93 61 e5 06 c1 a2 9a 22 87
c3 93 61 eb 06 01 da 07 06 e7 f7 f8 e7 fc e5 c6
00 08 a9 00 03 bb c6 01 00 00 e7 f7 e5 e7 f8 f1
e5 01 6d 86 d3 6d 7f 86 9d a2 e5 06 6d 86 d3 6d
7f 86 9d a2 eb 06 01 e6 01 6c 86 d3 6d e6 0a 6d
86 d3 6d ec 01 0a d6 06 01 da 07 06 e5 01 6d 86
d3 6d 7f 86 9d a2 e5 06 4d 86 d3 6d 7f 86 9d a2
- Docs
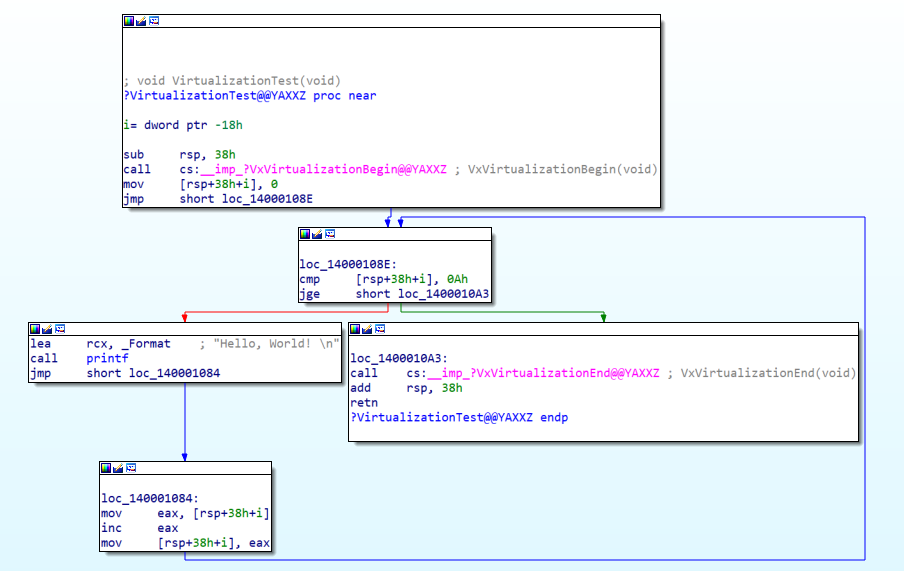
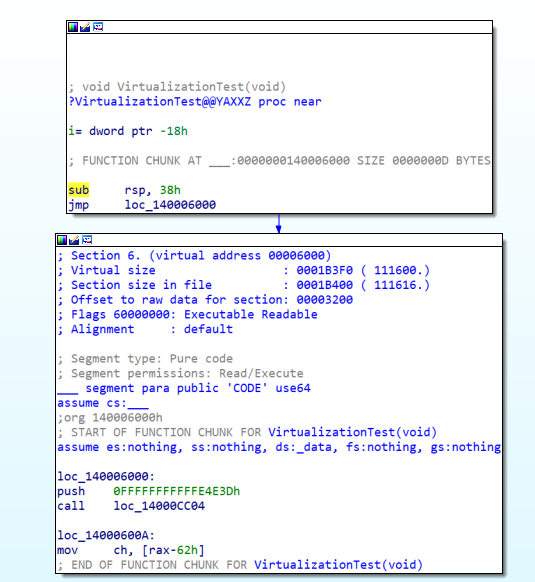
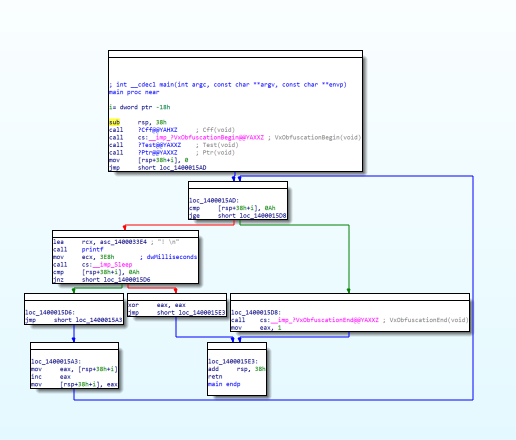
Optimization: Verify that VxVirtualizationBegin and VxVirtualizationEnd are in the same block.
If procedures are merged due to code optimization, problems may arise.switch-case: In the switch-case, when the branch movement is not an IMM value, it may be moved to the original position.Exception handling: Currently, the virtual CPU does not support exception handling.
The full version of VxLang is developed and operated under donation through Patreon.
The exact usage of VxLang and sharing of extension module code, new features of VxLang, etc. will be shared.
If you have any questions, please send your request to the email below.
- E-Mail: 0x999h@gmail.com
- Full Version
- You can control all features of the VxLang protector.
- Support for virtual CPUs with specialized CPU contexts.
- You can use the demo version to see if it's applicable to your program before you commit to the donation and full versions.
- Patreon
- Documentation
- 01: SDK Tutorial
- 02: Functional Unit Obfuscation with Map Files
- 03: DLL loading checks
- 04: Rust samples
- 05: Review behavior speed
- 06: Process Anti-Dumping Test
- Download
- Demo: ver.1.9.1.0
- Full: Latest version
- Update & News
Task-List- [DONE] Add
dual mode: Allows you to apply both code obfuscation and code virtualization. - Add Windows Static-Librarys.
- Once the above steps are complete, add the ARM system for the ELF file format.
- [DONE] Add