NclVault is an open source project written by the !//Lab completely in .Net Core. It runs on Windows, Mac and Linux.
The NclVault is under development, you could lost your data, use it and pay attention!
We use every day more credential to access to infinite online services. Someone uses online password manager like Lastpass, someone uses offline password manager but every type of Password Manager has its weak point.
- Online Password Manager: there are a lot of free services that permit to store our passwords on its servers. Free... Does the online Password Manager sell my information to third part? It's secure? What happens if someone hacks the service provider server?
- Offline Password Manger: like Keepass, every time I need to see a credential I must turn on my PC... Ok, we can copy the database on all of our devices, but when we need to update a credential? We need to deploy the new database manually.
NclVault is completely written in ASP.Net core API and allows you to store your credentials in secure mode.
This repository contains two projects:
- NclVaultAPIServer: this is the core. Written in ASP.Net Core API, it exposes the REST API that the clients connect to.
- NclVaultCLIClient: a simple .net core console application used to demonstrate how the API core server works.
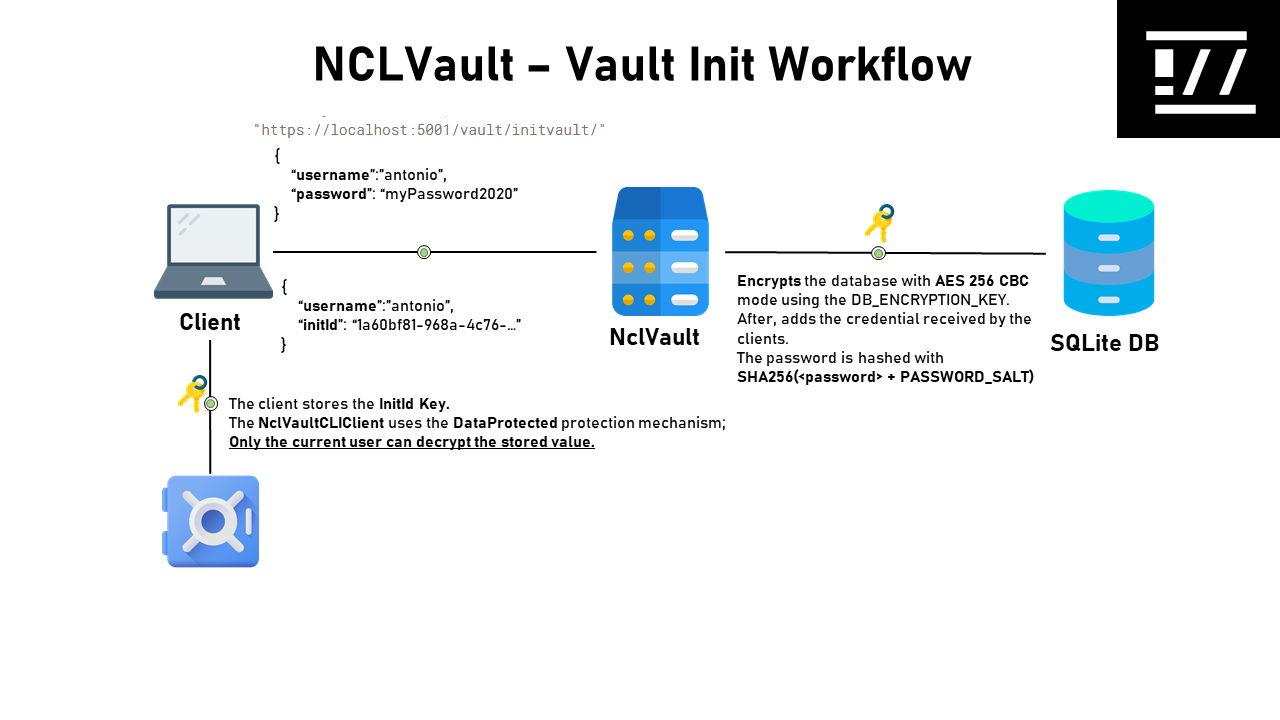
The below workflow shows how NCLVault initializes the database that will be used to store the credentials.
- The client sends to the server a POST HTTP request to
vault/initvault/API Endopoint with the below body:
{
"username": "antonio",
"password": "myPassword2020"
}
-
NCLVault Server reponses to the client with a JSON object that contains the
InitIdproperty. This property is random generated every each init command.STORE THE INITID VALUE SOMEWHERE!! WITHOUT IT YOU CAN'T RECOVER YOUR STORED PASSWORD -
The Client stores the
InitIdinside a sicure element. The NCLVaultCLIClient uses the DataProtected protection mechanism to store it. -
The NCLVault Server encrypts the database with AES256 CBC and stores the user password with
SHA256(password+salt)hash.
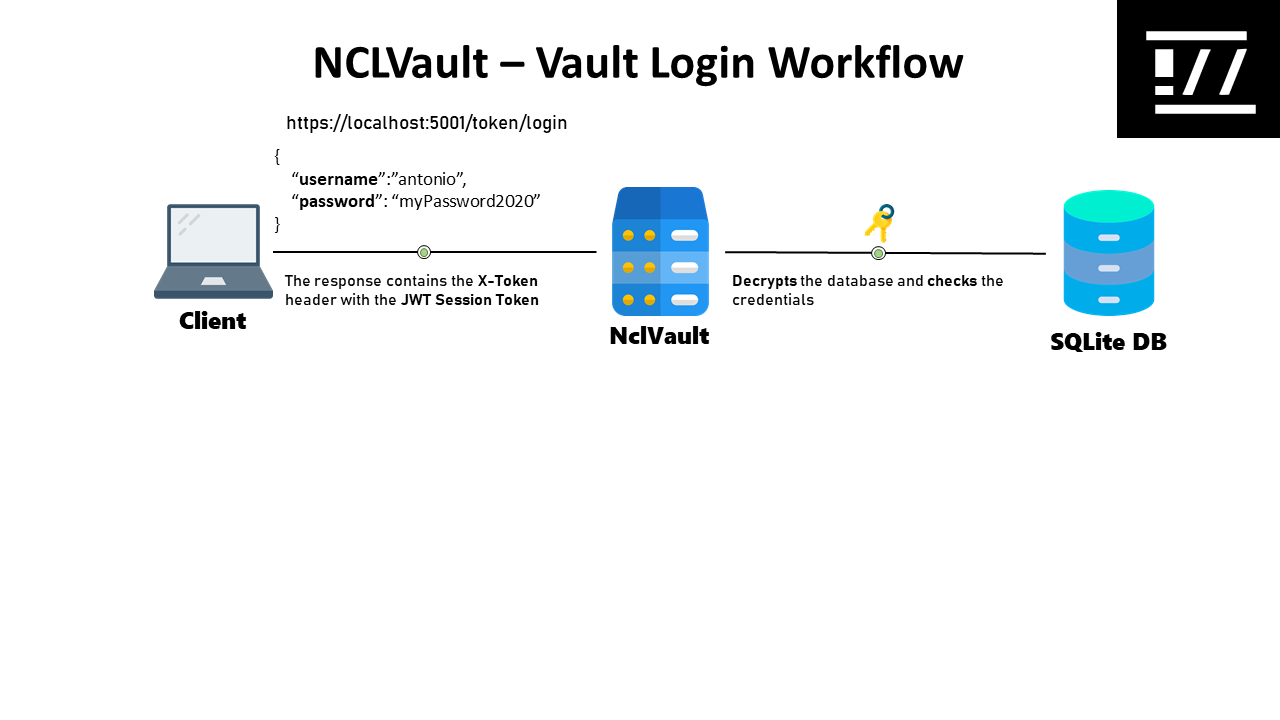
The below workflow shows how NCLVault permits the login to user that has initilizes the database.
- The client sends to the server a POST HTTP request to
token/loginAPI Endopoint with the below body:
{
"username": "antonio",
"password": "myPassword2020"
}
-
NCLVault Server decrypts the database and checks the credential sent from the client
-
NCLVault server sents, if the credential is correct, the JWT token inside the X-Token HTTP Header like this:
{
alg: "HS256",
typ: "JWT"
}.
{
username: "antonio",
exp: 1599042782,
iss: "NCLVault"
}.
[signature]
The claim username identifies the user that has correct logged on.
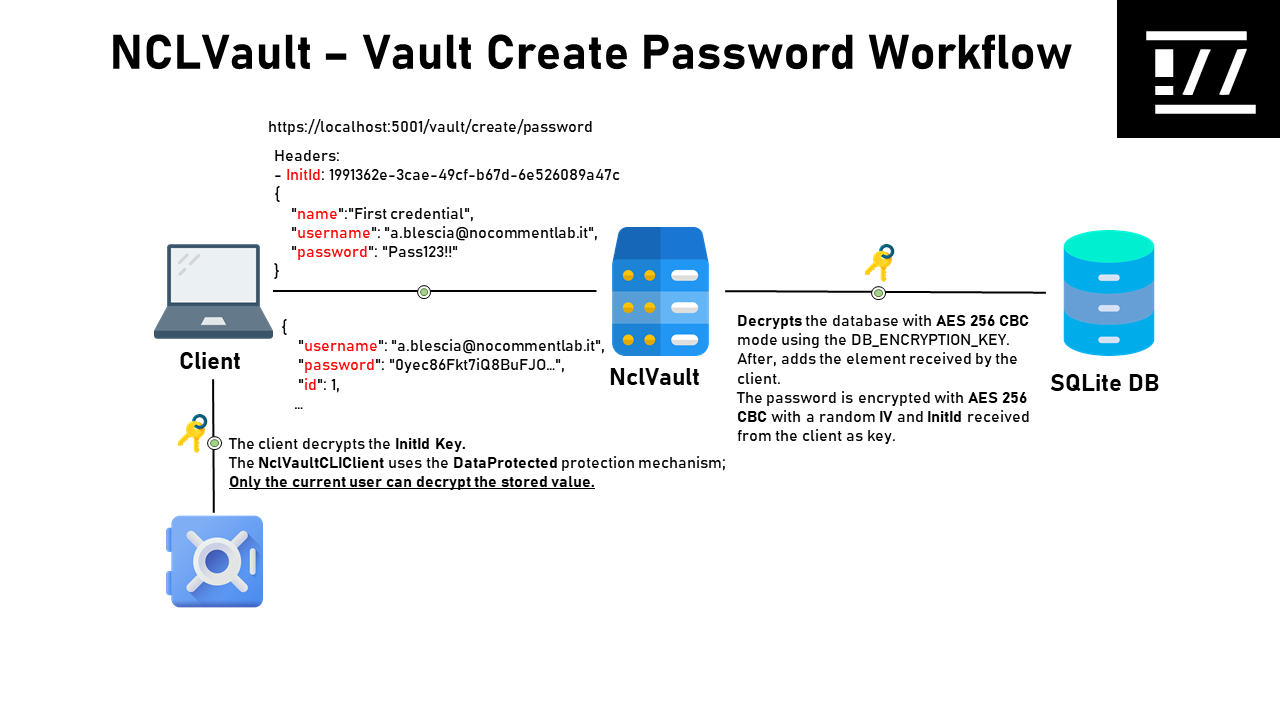
The below workflow shows how NCLVault permits the creation of a new entry inside its database.
-
The client decrypts the protected
InitIdkey stored locally -
The client sends to the server a POST HTTP request to
vault/create/passwordAPI Endopoint with the below body:{ "name":"First credential", "username": "a.blescia@nocommentlab", "password": "Pass123!!" }In this request, the client adds the HTTP Header
InitIdpreviously extracted. -
NCLVault Server decrypts the database and encrypt the received password il clear-text using the
Initidreceived by the client. The password encryption is made withAES 256withCBC modeand randomIV. -
NCLVault Server response to the client with the created entry. The password in not in clear-text in the response.
{
"username": "a.blescia@nocommentlab",
"password": "0yec86Fkt7iQ8BuFJOfFQLuHbNyj7RcLRC6N79hbkEk=",
"url": null,
"id": 1,
"group": null,
"name": "First credential",
"expired": "0001-01-01T00:00:00",
"notes": null
}
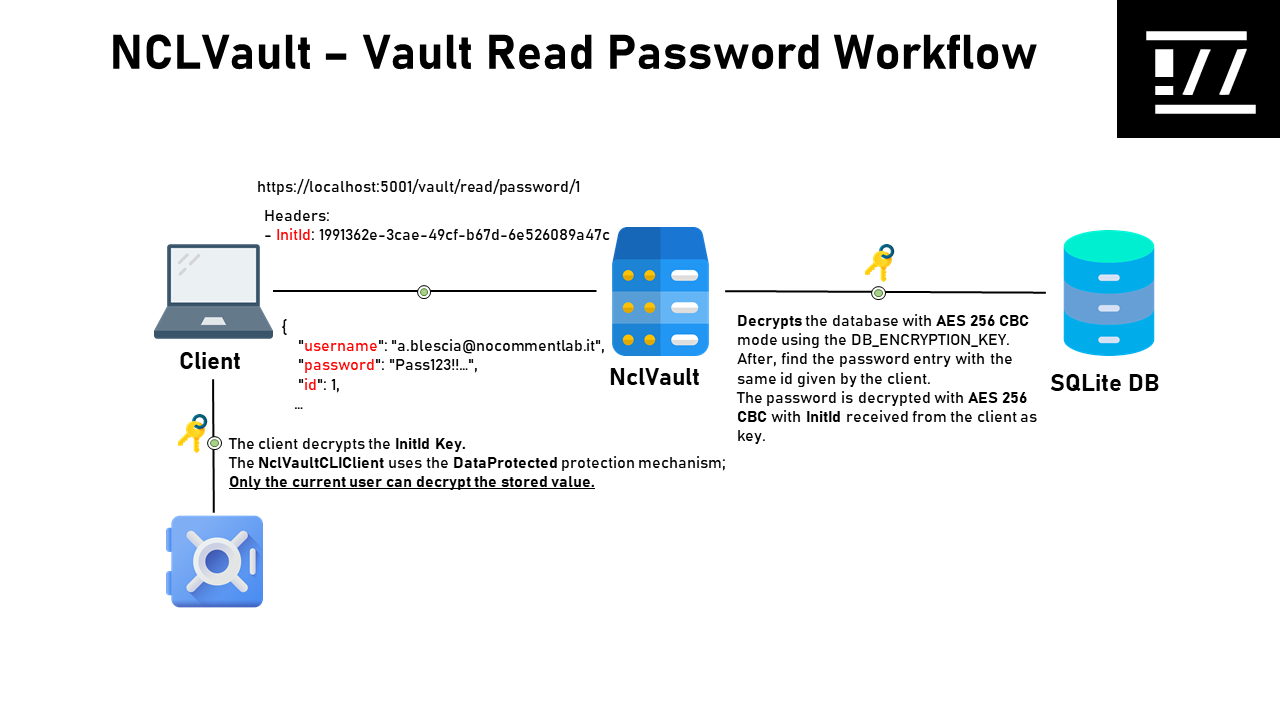
The below workflow shows how NCLVault permits the extraction of an entry from its database.
-
The client decrypts the protected
InitIdkey stored locally -
The client sends to the server a GET HTTP request to
vault/read/password/{id}API Endopoint. The{id}identify the password entryIn this request, the client adds the HTTP Header
InitIdpreviously extracted. -
NCLVault Server decrypts the database and decrypt the relative password entry ID with the
Initidreceived by the client. The password decryption is made withAES 256withCBC mode.
- Code Quality
- Random Password Generator Module
- Permit Multiple Users
- Write Recovery Strategy
- Keepass Import Module