-
Notifications
You must be signed in to change notification settings - Fork 41
Home
| Welcome to Brave Sync! |  |
|---|
NB: this wiki is currently undergoing a thorough review. please check back often to see when this notice disappears!
Brave Sync is a new way to automatically sync browsing data (bookmarks, preferences, history) between devices running the Brave browser. It uses client-side encryption such that no one's servers cannot read your data, since they do not have access to the encryption keys. (Not even Brave's servers can read your data!) Brave Sync is not designed for data backup; that is, if you delete Brave browser from all your devices and don't have a backup of your sync encryption key, you will not be able to decrypt old browsing data.
Brave Sync is disabled by default. Once you enable it on one device, you will be able to add more devices to Brave Sync by scanning a QR code or entering a seed phrase on the new device.
Although abitrary collections of data records may be synchronized, at present, Brave sync clients manage bookmarks only. In the future, we plan to add support for synchronizing Brave Rewards data.
-
A "Sync Chain" is configured using a seedphrase that is pseudo-randomly generated by the initial client. This seed phrase is used to derive an Ed25519 keypair and a NaCl secretbox key.
The seedphrase consists of 32 octets, encoded using a english-language word dictionary. The HKDF with a SHA-246 MAC is used to derive both the Ed25519 keypair and the NaCL secretbox key.
-
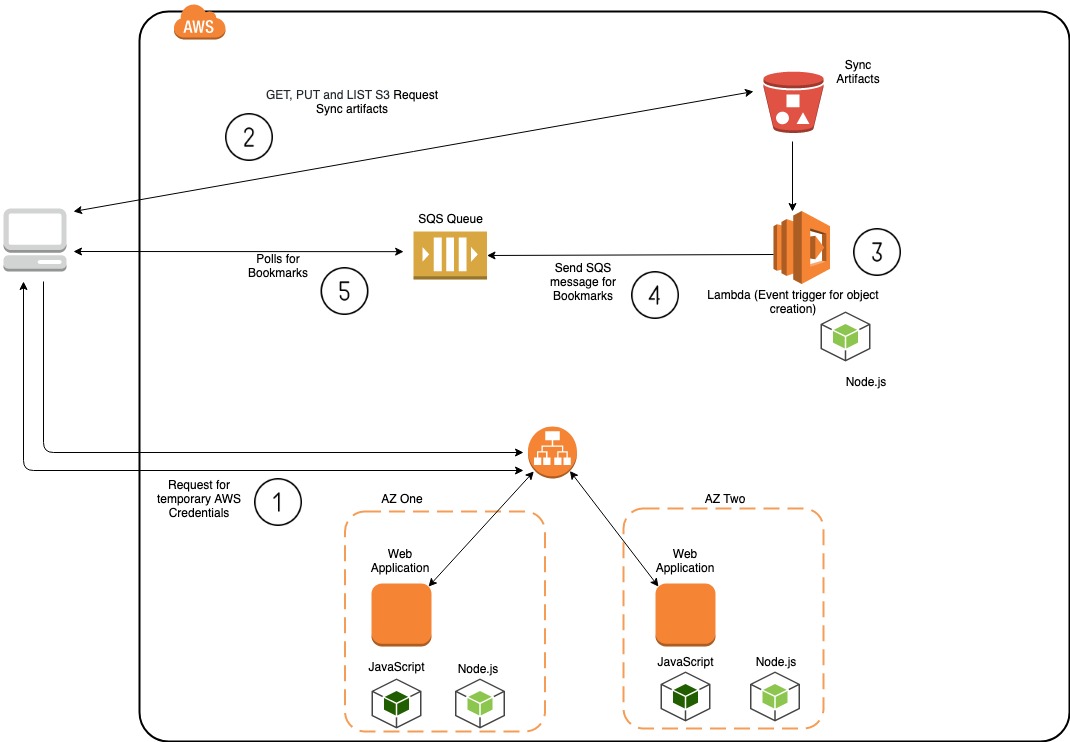
Access to the S3-based service is provided via a credential server, that verifies the client's Ed25519 signature over the request. If successful, credentials suitable for use with the AWS S3 service are returned.
Accordingly, add a new client to a "Sync Chain" is very easy, the user provides the client with the seed phrase.
-
As a client creates objects to be synchronized, it encrypts the record data (using NaCl) and sends it to the S3 service. The encrypted record data contains both the object along metadata such as the identifier of the client.
Accordingly, only the clients have access to plaintext objects or are able to determine how many clients are participating in the "Sync Chain".
-
All clients read objects from the AWS service, using either SQS (to retrieve only those objects uploaded within the last 24 hours), or S3 (to retrieve all objects uploaded for the "Sync Chain").
-
Clients are responsible for resolving conflicts, see Data Exchange.
A "Sync Chain" should have at least two participating devices.
When a device joins a "Sync Chain",
it has a set of initialization procedures.
This allows it to generate a unique deviceId within the "Sync Chain" and to fetch the initial synchronization state.
The Data Exchange document describes all of the protocol interactions
between clients.
Similarly,
see the Data Formats document for a description of the platform-independent
SyncRecords that are exchanged.
Briefly,
each SyncRecord contains a deviceId identifying the client generated the record,
an action indicating what action should be taken,
an objectId identifying the particular browser object,
and the object to be synchronized.
These are represented using protocol buffers and then encrypted prior to being uploaded.
Each platform makes use of a shared JavaScript library that implements the platform-independent aspects of Brave Sync. The library resides in an extension background page (laptop) or webview (mobile), and is accessed via asynchronous IPC.
There are two deployments within the AWS environment:
-
a Web application, written in node.js, that creates temporary AWS credentials to allow access to the "portion" of the S3 servie that contains the "Sync Chain" data; and,
-
an S3 application, using Lambda, that stores encrypted records and makes them available via either SQS (over the short-term) or S3 (since the epoch).
The Ed22519 public key associated with each "Sync chain" is encoded as a userId,
and all S3 buckets associated with that "Sync chain" are prefixed with /{userId}/.
Accordingly, the "Sync Chain" may be entirely removed by a client removing all S3 keys with that prefix.