Demonstration of typical security flaws in a web application and how to fix them:
- Exception Handling/Information Leakage
- Logging
- HTTPS - HTTP vulnerability shown using Wireshark inspecting packet, fixed using HTTPS .jks file and RSA private key with a default signature algorithm of MD5.
- SSL/TLS - enabled SSL connection on MySQL with OpenSSL
- Database Sensitive Storage - storage of passwords with hash and salt
- User Input Validation - prevent SQL injections or XSS
- Custom Error Handling
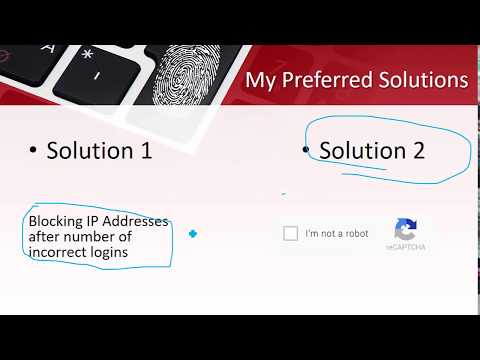
- Brute Force Attacks - repeated login attempts, vulnerability shown using Hydra - fixed using IP blocking function and Google Captcha
Brute Force attack can be shown by running the web app on a host machine and setting up a virtual machine Ubuntu 32bit using Hydra.
5 part walkthrough series hosted on YouTube:
Brute Force Attacks with Hydra - YouTube
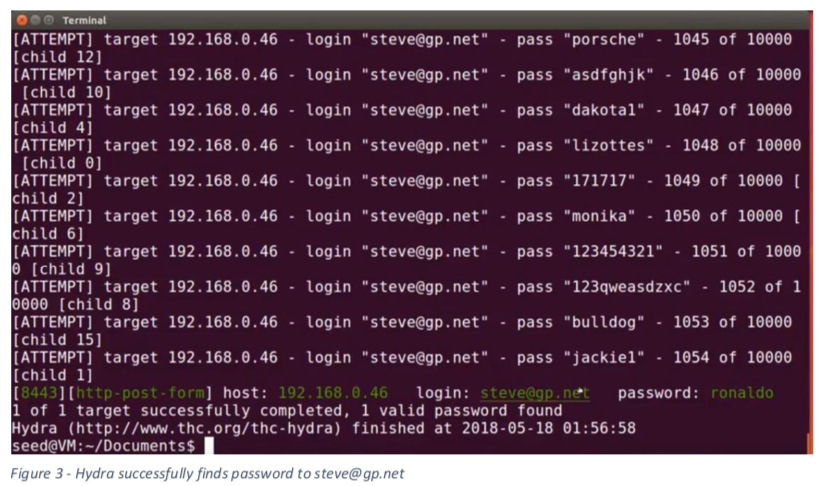
Hydra on VM successfully identifying username and password - based on a given username and a list of 10,000 random passwords
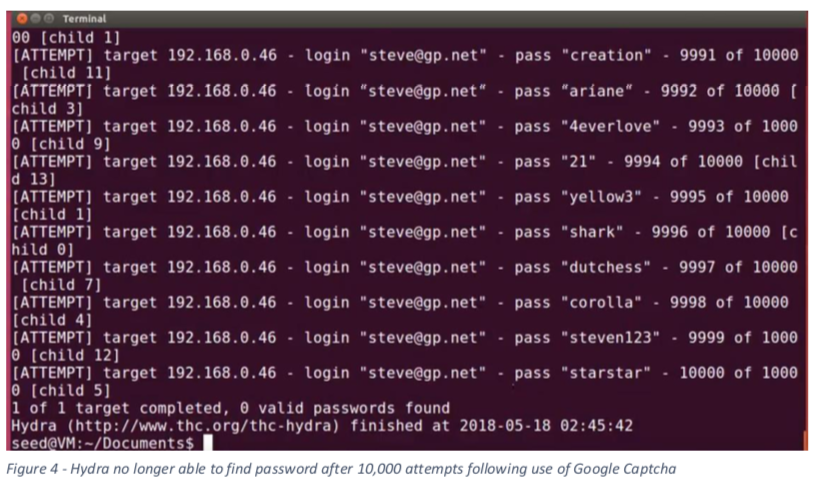
Hydra no longer able to identify username and password after implentation of IP blocking and Google Chrome
Open project in IntelliJ
Please ensure that Lombok annotation is installed and annotations are enabled.
If running of project via RunSpringBootApp does not work, please follow these steps:
$ git clone https://github.com/barclayd/Spring-Boot-Cyber-Security.git
Run Gradle Build
Gradle Boot Run
Please run the MayDatabaseSchema.sql script found within the SQL folder. (/SQL/MayDatabaseSchema) This is version is specially designed to populate the database with sample data for testing to demonstrate security fixes. Please ensure that any login details that differ to: username: root password: comsc
are appropriately edited and replaced within application.properties.
Please navigate to https://localhost:8443/login
Please note, if you access the page on Chrome or Firefox, due to the HTTPS certificate being self-signed, you will see this warning message "Your connection is not private"
To view the web page, please follow the following steps:
- Click "Advanced"
- Click "Proceed to locahost:8443 (unsafe)"
You will now be able to view the webpage
Logging into the application:
Please user dummy accounts:
GP Login: Email: steve@gp.net Password: ronaldo
Create Ubuntu 32bit VM in image of SecVM-April Download a list of passwords and store in cd/Documents from Install Hydra using relevant commands supplied in report or Youtube tutorial