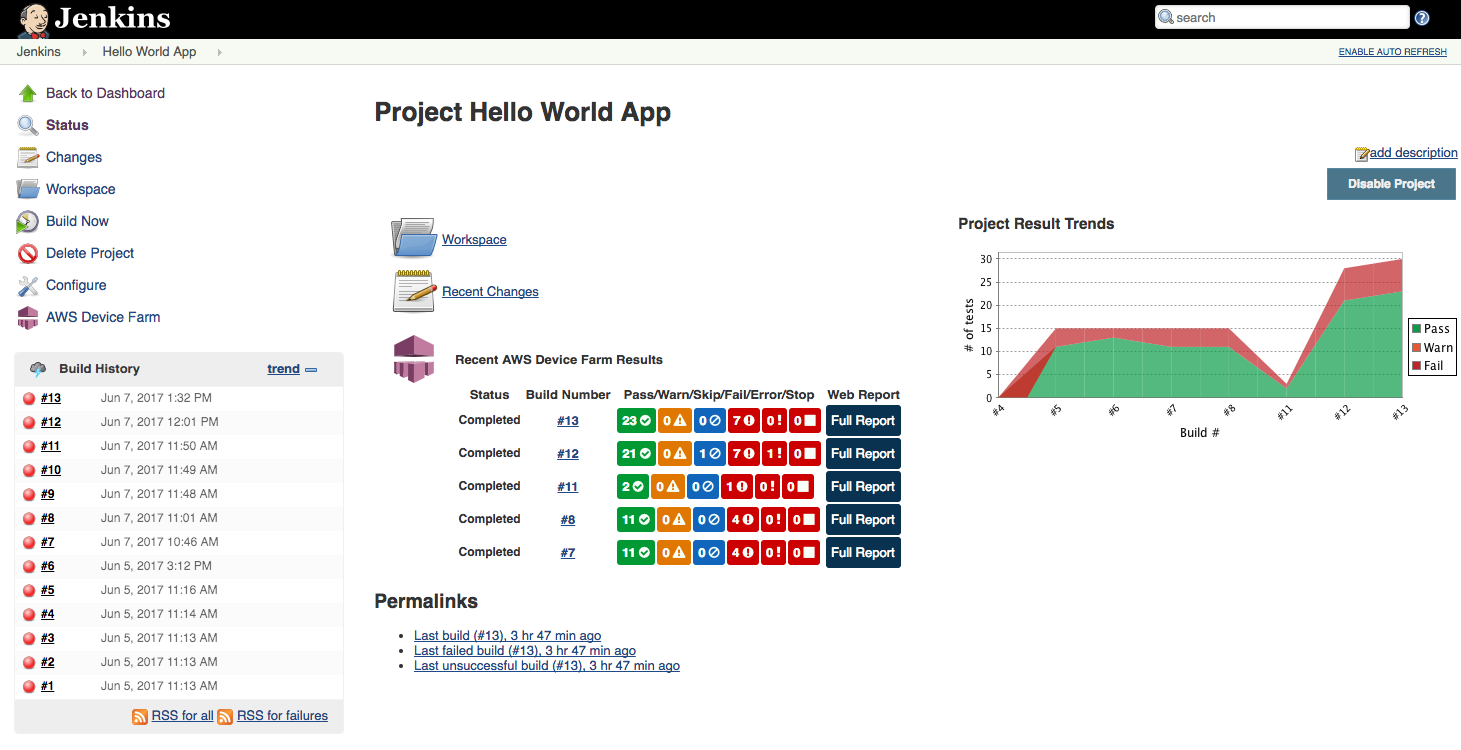
AWS Device Farm integration with Jenkins CI
This plugin provides AWS Device Farm functionality from your own Jenkins CI server:
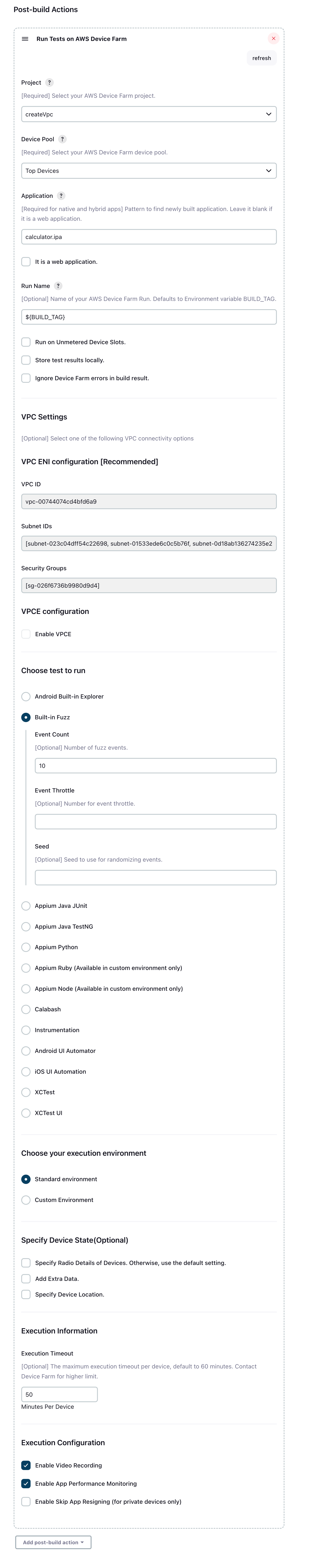
It also provides the device state details specification if the checkboxs are checked. Otherwise, the default settings will be used:
It also can pull down all of the test artifacts (logs, screenshots, etc.) locally:
- Clone the GitHub repository.
- Import the Maven project into your favorite IDE (Eclipse, IntelliJ, etc.).
- Build the plugin using the Makefile (
make clean compile). - The plugin is created at
target/aws-device-farm.hpi.
- Copy the
hpifile to your Jenkins build server and place it in the Jenkins plugin directory (usually/var/lib/jenkins/plugins). - Ensure that the plugin is owned by the
jenkinsuser. - Restart Jenkins.
- Log into your Jenkins web UI.
- On the left-hand side of the screen, click “Manage Jenkins”.
- Click “Manage Plugins”.
- Near the top of the screen, click on the “Advanced” tab.
- Under the “Upload Plugin”, click “Choose File” and select the AWS Device Farm Jenkins plugin that you previously downloaded.
- Click “Upload”.
- Check the “Restart Jenkins when installation is complete and no jobs are running” checkbox.
- Wait for Jenkins to restart.
Note : Follow these steps if you are using Secret and Access key to access Device Farm. If you want to access Device Farm using IAM Role, refer to "Generating a proper IAM role" section
- Log into your AWS web console UI.
- Click “Identity & Access Management”.
- On the left-hand side of the screen, click “Users”.
- Click “Create New Users”.
- Enter a user name of your choice.
- Leave the “Generate an access key for each user” checkbox checked.
- Click “Create”.
- View or optionally download the User security credentials that were created; you will them them later.
- Click “Close” to return to the IAM screen.
- Click your user name in the list.
- Under the Inline Policies header, click the “AWS IAM role ARN for your AWS Device Farm account” link to create a new inline policy.
- Select the “Custom Policy” radio button.
- Click “Select”.
- Give your policy a name under “Policy Name”.
- Copy/paste the following policy into “Policy Document”:
{
"Version": "2012-10-17",
"Statement": [{
"Effect": "Allow",
"Action": [
"devicefarm:*",
"ec2:DescribeVpcs",
"ec2:DescribeSubnets",
"ec2:DescribeSecurityGroups",
"ec2:CreateNetworkInterface"
],
"Resource": [
"*"
]
},
{
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "arn:aws:iam::*:role/aws-service-role/devicefarm.amazonaws.com/AWSServiceRoleForDeviceFarm",
"Condition": {
"StringLike": {
"iam:AWSServiceName": "devicefarm.amazonaws.com"
}
}
}
]
}
- Click “Apply Policy”.
Note : Only applies when you want to access Device Farm through an IAM Role.
You need to create one Device Farm access role to access the Device Farm Resource and one User or Role depending upon how you are running Jenkins.
- Creating Device Farm Role.
- Log into your AWS web console UI.
- Click “Identity & Access Management”.
- On the left-hand side of the screen, click “Roles”.
- Click “Create Role”.
- In the AWS service section select Ec2 and click on Next.
- Under the Inline Policies header, search and click the “AWSDeviceFarmFullAccess ” policy.This will give complete device farm access.
- Go the the summary page of the role and click on edit next to "Maximum CLI/API session duration" and select 8hrs. This sets the expiration of the session associated with the IAM role to 8 hrs.
- Now you want to give the access to the role/user to assume this role Open the new role you have created in console and then click on "Trust Relationships" tab. Click on "Edit Trust Relationship" and enter the following policy :
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "To be replaced by Arn of user/role running on the Jenkins machine",
"Service": "devicefarm.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
- Setting up Role/User running Jenkins
- We need to also give access
- Go to the user or role that you want to add policy to.
- In the permission tab click on Create Policy.
- Select STS in the service name, search for assume role in actions and select it.
- In the Resources section enter the arn for the device farm role.
- Click on review policy and then enter name and description and click on Create policy.
- Log into your Jenkins web UI.
- On the left-hand side of the screen, click “Manage Jenkins”
- Click “Configure System”.
- Scroll down to the “AWS Device Farm” header.
- If you are using IAM Role to configure the Jenkins Plugin, add the ARN for the role here.
- If not, Copy/paste your AKID and SKID you created previously into their respective boxes.
- Click “Save”.
- Log into your Jenkins web UI.
- Click on the job you wish to edit.
- On the left-hand side of the screen, click “Configure”.
- Scroll down to the “Post-build Actions” header.
- Click “Add post-build action” and select “Run Tests on AWS Device Farm”.
- Select the project you would like to use.
- Select the device pool you would like to use.
- Select if you'd like to have the test artifacts (such as the logs and screenshots) archived locally.
- In “Application”, fill in the path to your compiled application for testing native or hybrid app. Check "It is a web application." for testing web app.
- Optional: If you are using VPC, then confirm your VPC Settings are correct by a.) ensuring you have the desired VPC ENI configuration [read only] or b.) Enabling VPCE
- Choose the test framework, provide the path to your test package location and other relavent details.
- Configure device state parameters like radio details, extra data and device locations.
- Configure the maximum execution timeout. The default execution timeout is 60 minutes.
- Set the execution configuration parameters: video recording and app performance monitoring.
- Click “Save”.
- Go to Job > Pipeline Syntax > Snippet Generator
- Select "devicefarm" sample step or "step: General Build Step" > "Run Tests on AWS Device Farm"
- Input the Device Farm Run Configuration
- Click "Generate Pipeline Script"
We validate two things: 1) If the credentials are valid, 2) and if they have access to AWS Device Farm
- Log in to your Jenkins host.
- If using access and secret key, Run "aws devicefarm list-projects" on the host running Jenkins using the AWS CLI. If this fails, first check you credentials. If they are correct, refer to the "Generating a proper IAM user" section to ensure that you have given Device Farm necessary credentials.
- If you are using role ARN Run "aws sts assume-role --role-arn "EnterRoleArnHere --duration-seconds 28800" using the AWS CLI. If this fails, refer to the "Generating a proper IAM role" section to verify if the role has correct assume role permissions. Run "aws devicefarm list-projects" using the AWS CLI. If this fails, your role doesn't have access to device farm. Please re-verify the steps above.
- Verify that the Project you are looking for is visible by logging in to the Device Farm console.
- If yes, go to the Jenkins -> Manage Jenkins -> Configure System -> AWS Device Farm section and click on Validate.
- AWS SDK 1.11.126 or later.