-
Notifications
You must be signed in to change notification settings - Fork 521
SSH
Please note! This wiki is no longer maintained. Our documentation has moved to https://securityonion.net/docs/. Please update your bookmarks. You can find the latest version of this page at: https://securityonion.net/docs/SSH.
By default secure shell (ssh) listens on tcp port 22. If you want to obfuscate it by changing the listening port from port 22 to port 31337, you can do so in the sshd_config file.
note: you can use your favorite text editor (e.g., vi, gedit, nano, emacs) to edit the sshd_conf file, but for the purpose of this example vi will be used.
sudo vi /etc/ssh/sshd_conf
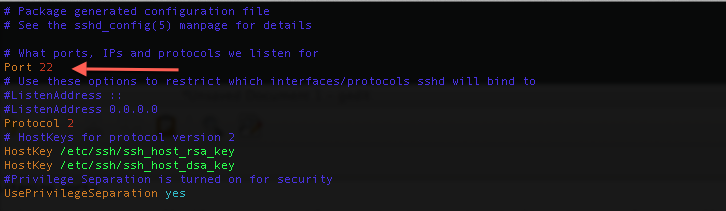
Change the port to 31337
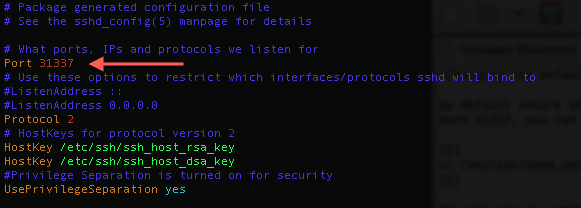
Perform a graceful restart on the ssh daemon so that it will now start listening on port 31337.
sudo killall -HUP sshd
Verify that ssh is listening on the new port.
netstat -nltp | grep sshd

note: make sure you allow the new ssh port in the ufw if you're using the firewall.
sudo ufw allow 31337/tcp

- Introduction
- Use Cases
- Hardware Requirements
- Release Notes
- Download/Install
- Booting Issues
- After Installation
- UTC and Time Zones
- Services
- VirtualBox Walkthrough
- VMWare Walkthrough
- Videos
- Architecture
- Cheat Sheet
- Conference
- Elastic Stack
- Elastic Architecture
- Elasticsearch
- Logstash
- Kibana
- ElastAlert
- Curator
- FreqServer
- DomainStats
- Docker
- Redis
- Data Fields
- Beats
- Pre-Releases
- ELSA to Elastic
- Network Configuration
- Proxy Configuration
- Firewall/Hardening
- Email Configuration
- Integrating with other systems
- Changing IP Addresses
- NTP
- Managing Alerts
- Managing Rules
- Adding Local Rules
- Disabling Processes
- Filtering with BPF
- Adjusting PF_RING for traffic
- MySQL Tuning
- Adding a new disk
- High Performance Tuning
- Trimming PCAPs