In December 2020, ryotkak reported as part of the Bug Bounty program how he exfiltrated the GITHUB_TOKEN from a GitHub Actions workflow. The token was used to push code to a release branch. You can read the details here and here.
Learn how to set minimum permissions for the GITHUB_TOKEN.
-
Create a fork of the repo.
-
Go to the
Actionstab in the fork. Click theI understand my workflows, go ahead and enable thembutton.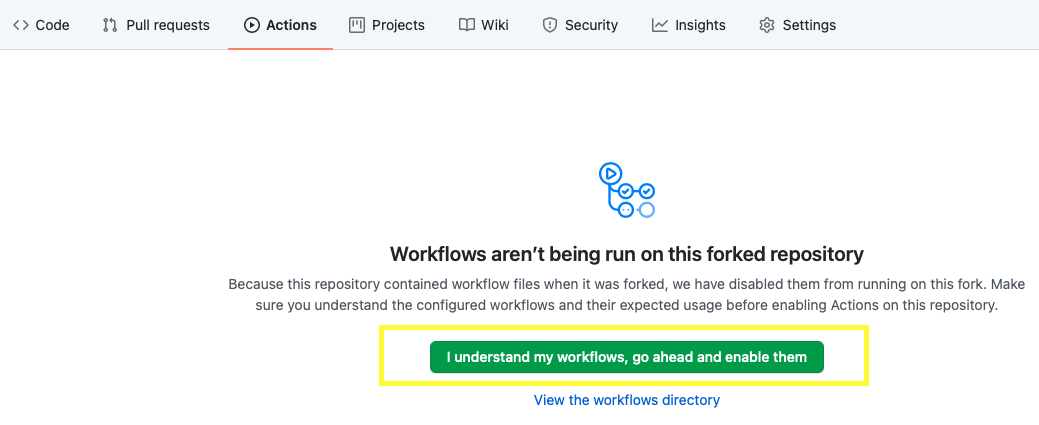
-
Click on the
Lintworkflow and then clickRun workflow. Once you do this, a GitHub workflow will get triggered.
-
Click on the Actions tab again, click on the workflow that just started, and in the job run logs, have a look at the permissions assigned to the
GITHUB_TOKEN.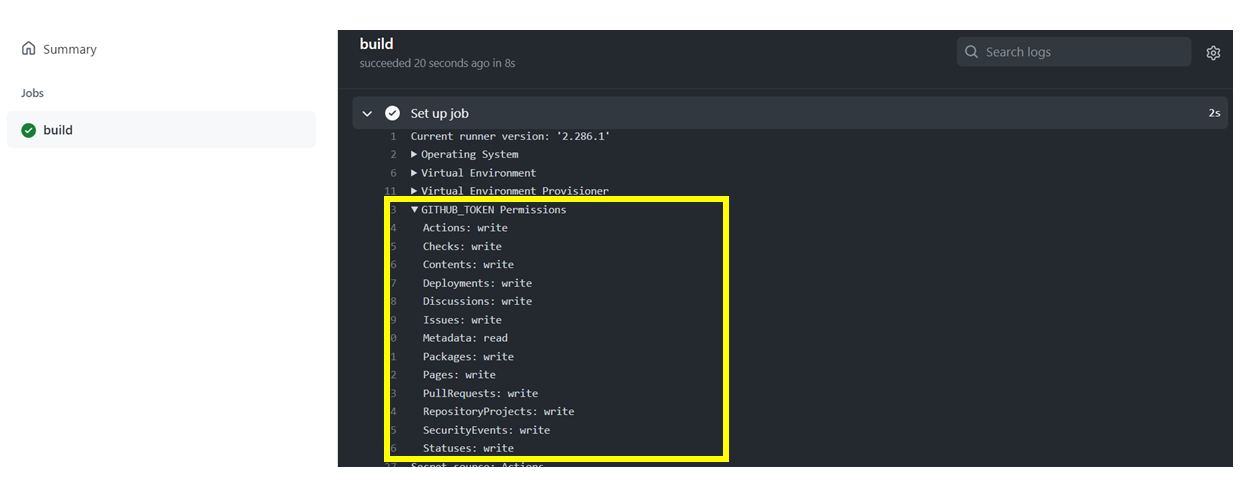
-
By default, the
GITHUB_TOKENhas a lot of permissions assigned. As a security best practice, theGITHUB_TOKENshould be assigned the minimum permissions. -
Review the workflow file at
./github/workflows/lint.yml. You can now manually add thepermissionskey, but it is hard to know what the permissions should be. Different 3rd party Actions may use different permissions. In this tutorial, let us fix the permissions automatically. -
Visit https://app.stepsecurity.io. Copy the workflow file and paste it in the editor. For this tutorial, only check the
Restrict permissions for GITHUB_TOKENcheck box and click onSecure workflowbutton.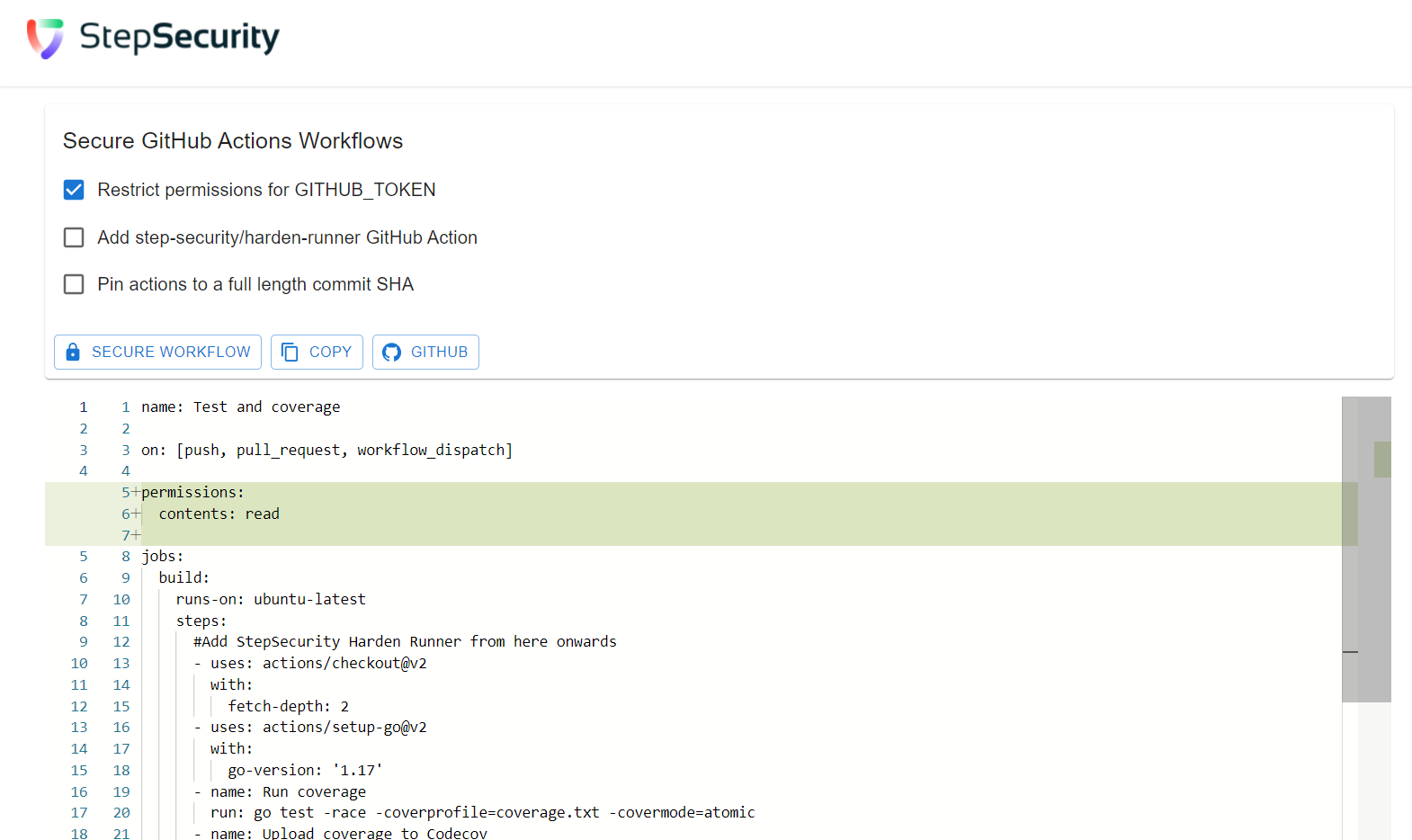
-
Observe that the workflow now has updated permissions. Copy the updated workflow and edit the workflow file at
./github/workflows/lint.yml. -
Run the workflow again.
-
Have a look at the permissions assigned to the
GITHUB_TOKEN. Now it has the minimum permissions assigned. Even if the token is compromised, the damage potential is reduced.
