I was developing jsleak during most of my free time for my own need.It is easy-to-use command-line tool designed to uncover secrets and links in JavaScript files or source code. The jsleak was inspired by Linkfinder and regexes are collected from multiple sources.
- Discover secrets in JS files such as API keys, tokens, and passwords.
- Identify links in the source code.
- Complete Url Function
- Concurrent processing for scanning of multiple Urls
- Check status code if the url is alive or not
Jsleak now supports regex patterns from secrets-patterns-db https://github.com/mazen160/secrets-patterns-db.
If you want to use your own custom regex patterns, you can place them in a YAML file following the template below.
patterns:
- pattern:
name: Amazon MWS Auth Token
regex: "amzn\\.mws\\.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}"
confidence: low
If you are using old version of golang (go 1.15, 1.16) , use the following command to install jsleak.
go get github.com/channyein1337/jsleak
If you are using latest version of go (1.17+) , use the following command to install.
go install github.com/channyein1337/jsleak@latest
Choose a YAML file from the secrets-patterns-db. If you’re not sure which one to pick, consider using: https://raw.githubusercontent.com/mazen160/secrets-patterns-db/refs/heads/master/datasets/trufflehog-v3.yaml
Run jsleak with Your Selected Regex File
echo "http://testphp.vulnweb.com/" | jsleak -t trufflehog-v3.yaml -s
To display help message
jsleak -h
Secret Finder
echo http://testphp.vulnweb.com/ | jsleak -t secret.yaml -s
Link Finder
echo http://testphp.vulnweb.com/ | jsleak -l
Complete Url
echo http://testphp.vulnweb.com/ | jsleak -e
Check Status
echo http://testphp.vulnweb.com/ | jsleak -c 20 -k
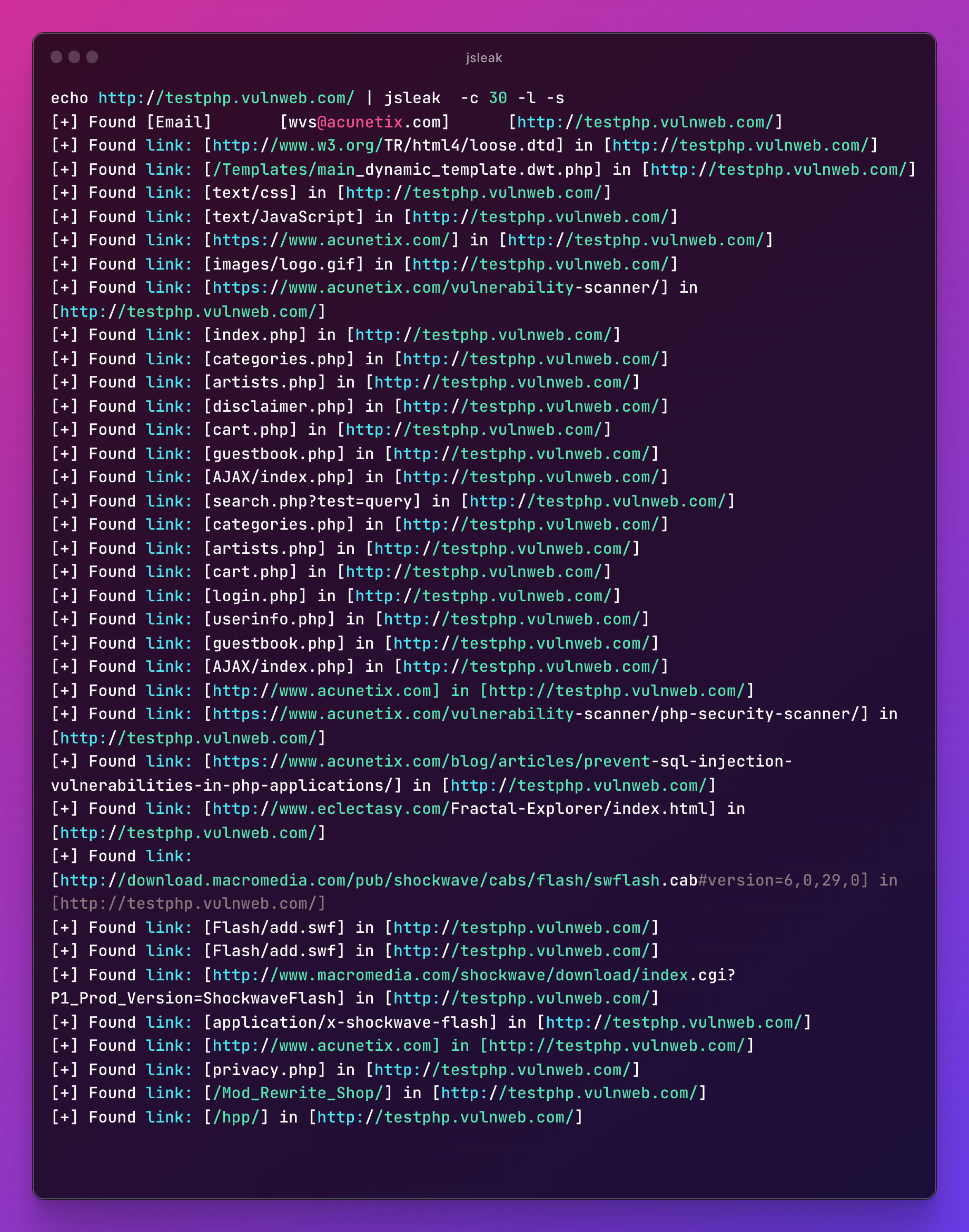
You can also use multiple flags
echo http://testphp.vulnweb.com/ | jsleak -c 20 -l -s
Running with Urls
cat urls.txt | jsleak -l -s -c 30
- Scan secret on completeURL with 200 response.
- Add Version flag.
- Support scanning local files.
- Support scanning apk files.
- Update Regex.
- Support mulitple user agents.
- Support color output