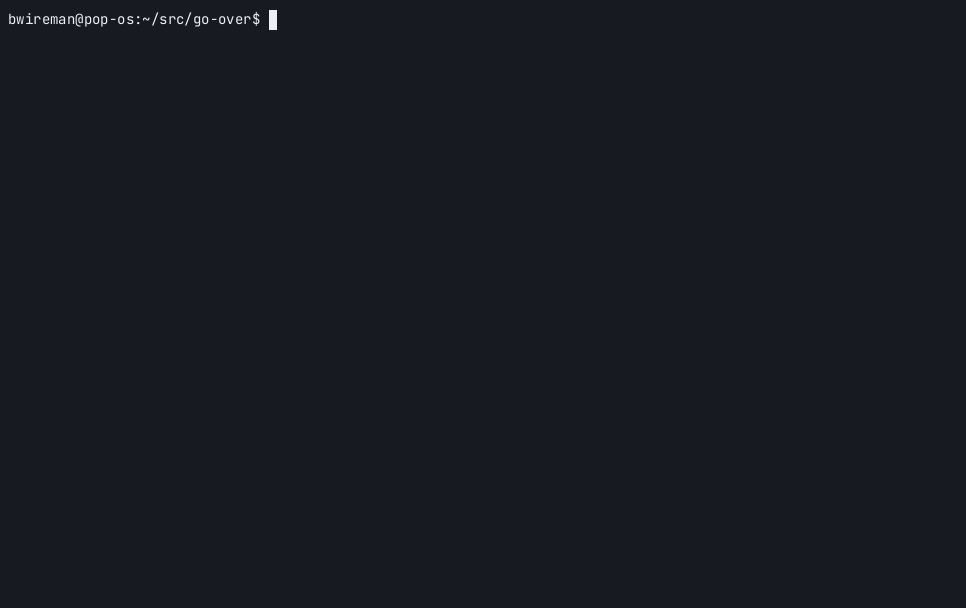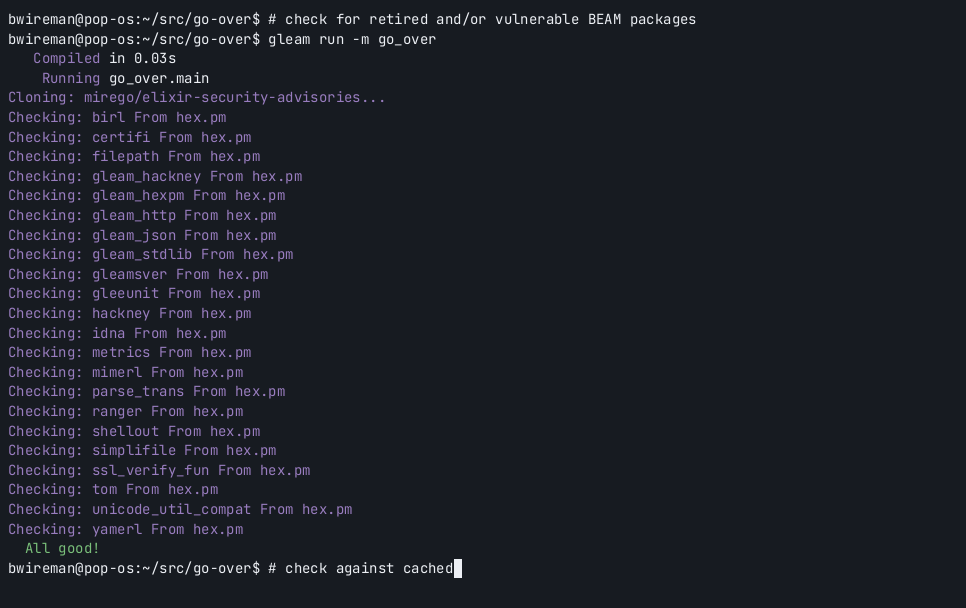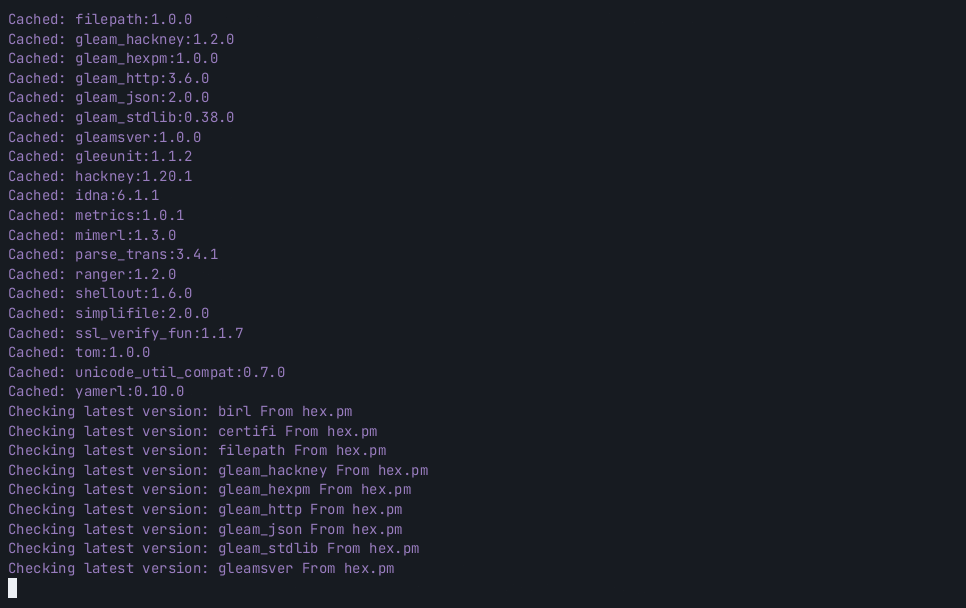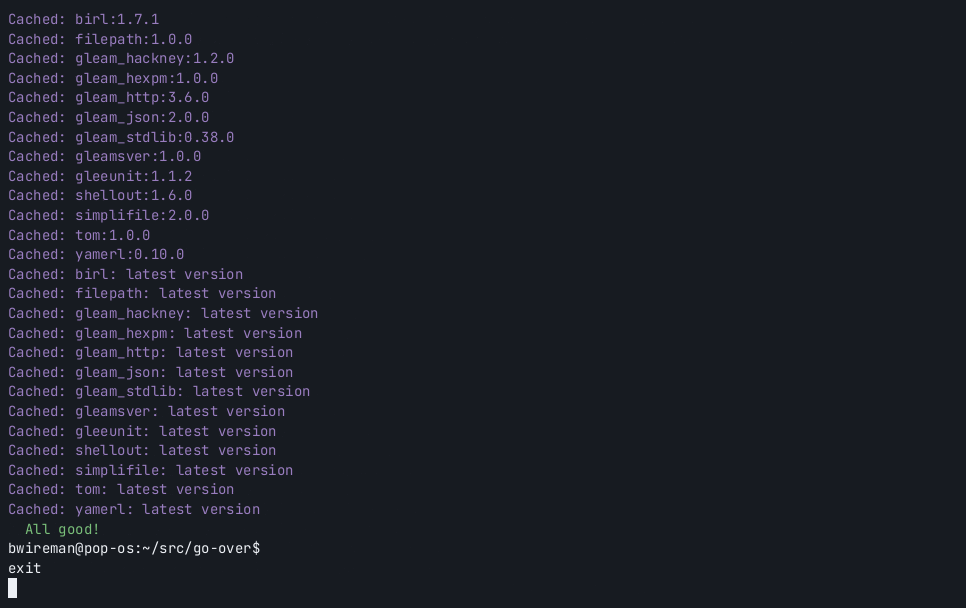
A tool to audit Erlang & Elixir dependencies, to make sure your ✨ gleam projects really sparkle!
🚨 NOTE: security advisories are NOT currently monitored for gleam dependencies. The language, while excellent, is far too new and niche
gleam add --dev go_over- add
.go-over/to your.gitignore - make sure
git&curlare installed
If running with Javascript install
{
"devDependencies": {
"yaml": "^2.4.3"
}
}Bun, Deno & Nodejs are all supported!
gleam run -m go_overOverride config values if set
--force: will force pulling new data even if the cached data is still valid--format=<format>: specify the output format of any warnings.["minimal", "detailed", "json"]--outdated: will additionally check if newer versions of dependencies exist--ignore-indirect: will ignore all warnings for indirect dependencies
Optional settings that can be added to your project's gleam.toml
[go-over]
# disables caching if false
# default: true
cache = true
# sets output format for warnings ["minimal", "detailed", "json"]
# default: "minimal"
format = "minimal"
# will additionally check if newer versions of dependencies exist
# default: false
outdated = false
# will ignore all warnings for indirect dependencies
# default: false
ignore_indirect = false
[go-over.ignore]
# list of package names to skip when auditing dependencies
# default: []
packages = ["example_package"]
# list of warning severities to skip when auditing dependencies
# default: []
# (case insensitive)
severity = ["example_moderate"]
# list of advisory IDs to skip when auditing dependencies
# default: []
ids = ["GHSA-xxxx-yyyy-zzzz"]- Security advisory data is cached for six hours
- hex.pm retired package data is cached for one hour
You can add go_over to you're pre-commit hooks by installing 🌵cactus & then adding this to your gleam.toml
[cactus.pre-commit]
actions = [
{ command = "go_over", kind = "module", args=["--outdated"] ,
]You can also schedule daily runs to keep your deps up to date and open issues when necessary! Example
- As I'm sure is no surprise this tool is inspired by (and all around worse than) mirego/mix_audit. Please check it out!
- It also draws inspiration from mix hex.audit
-
This tool uses mirego/elixir-security-advisories which is it self licensed with
BSD-3-Clause licenseCC-BY 4.0 open source license.- See their #license section
-
Code original to this repo is Licensed under
MIT