-
Notifications
You must be signed in to change notification settings - Fork 4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
feat(cloudfront-origins): allow custom originPath for apigateway.RestApi constructs #24023
Conversation
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
The pull request linter has failed. See the aws-cdk-automation comment below for failure reasons. If you believe this pull request should receive an exemption, please comment and provide a justification.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Thank you for your contribution! Overall this looks good. I just have a question inline. Additionally, please add an integ test to cover this change. I'm concerned about the potential testing gap given that your change wasn't picked up by a test. Not your fault, but I like to take every opportunity to improve our test coverage.
If, for any reason, running tests isn't feasible for you, please let me know and I can assist after you write the test case.
| @@ -6,7 +6,7 @@ import { validateSecondsInRangeOrUndefined } from './private/utils'; | |||
| /** | |||
| * Properties for an Origin for an API Gateway REST API. | |||
| */ | |||
| export interface RestApiOriginProps extends cloudfront.OriginOptions { | |||
| export interface RestApiOriginProps extends cloudfront.OriginProps { | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
What is in OriginProps that isn't in OriginOptions and vice versa? I'm concerned this might break other languages even if it's fine in TypeScript.
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
OriginPropsextendsOriginOptionsand declares theoriginPath.
export interface OriginOptions {
readonly connectionTimeout?: Duration;
readonly connectionAttempts?: number;
readonly customHeaders?: Record<string, string>;
readonly originShieldRegion?: string;
readonly originShieldEnabled?: boolean;
readonly originId?: string;
}
export interface OriginProps extends OriginOptions {
readonly originPath?: string;
}OriginPropsis used in other packages. WhereOriginOptionsis internal? (not sure)
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
since the only new property is optional, this should be non-breaking
97fed5b to
1b5eedc
Compare
|
@TheRealAmazonKendra is the integ test case correct? I followed the instructions at |
✅ Updated pull request passes all PRLinter validations. Dissmissing previous PRLinter review.
58e9396 to
dea87bf
Compare
Pull request has been modified.
|
🔄 |
a7e4593 to
0101b88
Compare
|
@Naumel 🟢 |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
lgtm, leaving dnm so @TheRealAmazonKendra can take a look
| @@ -6,7 +6,7 @@ import { validateSecondsInRangeOrUndefined } from './private/utils'; | |||
| /** | |||
| * Properties for an Origin for an API Gateway REST API. | |||
| */ | |||
| export interface RestApiOriginProps extends cloudfront.OriginOptions { | |||
| export interface RestApiOriginProps extends cloudfront.OriginProps { | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
since the only new property is optional, this should be non-breaking
|
This PR has been in the CHANGES REQUESTED state for 3 weeks, and looks abandoned. To keep this PR from being closed, please continue work on it. If not, it will automatically be closed in a week. |
…igin path when using origins.RestApiOrigin
|
PR not abandoned |
👍 |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
AWS CodeBuild CI Report
Powered by github-codebuild-logs, available on the AWS Serverless Application Repository |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
…Api constructs (aws#24023) ### Current behavior - the `apigateway.RestApi` splits the `restApi.url` and uses the stage name as `originPath` / "Origin path - optional" option in the CloudFront Origin by default ### Issue / Limitation - when using multiple Behaviors in my CloudFront Distribution: - S3 as the default behavior - Regional API Gateway as additional behavior and CloudFront Origin My API Gateway receives an extra `/<api-gateway-stage>/` in its event path and doesn't trigger the correct lambda integration. The below CDK example reproduces the behavior mentioned above: ```typescript import * as cdk from "aws-cdk-lib"; const meLambda = new cdk.aws_lambda_nodejs.NodejsFunction( this, "meLambda", { entry: "handlers/me.ts", } ); const s3_bucket = new cdk.aws_s3.Bucket(this, "somebucket"); const api = new cdk.aws_apigateway.RestApi(this, "somerestapi", { endpointConfiguration: { types: [apigw.EndpointType.REGIONAL], }, defaultCorsPreflightOptions: { allowOrigins: ["*"], }, }); api.root .addResource("me") .addMethod("GET", new apigw.LambdaIntegration(meLambda)); const apiOrigin = new cdk.aws_cloudfront_origins.RestApiOrigin(api); const cdn = new cdk.aws_cloudfront.Distribution(this, "websitecdn", { defaultBehavior: { origin: new cdk.aws_cloudfront_origins.S3Origin(s3_bucket), allowedMethods: cdk.aws_cloudfront.AllowedMethods.ALLOW_GET_HEAD_OPTIONS, viewerProtocolPolicy: cdk.aws_cloudfront.ViewerProtocolPolicy.REDIRECT_TO_HTTPS, }, additionalBehaviors: { "prod/*": { // <<<---- The "prod/" is added in the CloudFront Origin Path, NOT DESIRED IS THIS CASE origin: apiOrigin, allowedMethods: cdk.aws_cloudfront.AllowedMethods.ALLOW_ALL, cachePolicy: cdk.aws_cloudfront.CachePolicy.CACHING_DISABLED, viewerProtocolPolicy: cdk.aws_cloudfront.ViewerProtocolPolicy.HTTPS_ONLY, }, }, }); ``` The above will have the following URLs: - `https://<api-gateway-url>/<api-gateway-stage>` - `https://<cloudfront-distribution-url>/some-image.png` => Default Behavior, S3 Bucket - `https://<cloudfront-distribution-url>/<api-gateway-stage>` => API Gateway forward request Because the CloudFront Origin created by `RestApiOrigin` appends the `<api-gateway-stage>` in its CloudFront Origin "Origin Path - optional" option, when using `https://<cloudfront-distribution-url>/<api-gateway-stage>/me` the API Gateway receives `/<api-gateway-stage>/<api-gateway-stage>/me` instead of `/<api-gateway-stage>/me` Removing the "Origin Path - optional" value, fixes the problem. 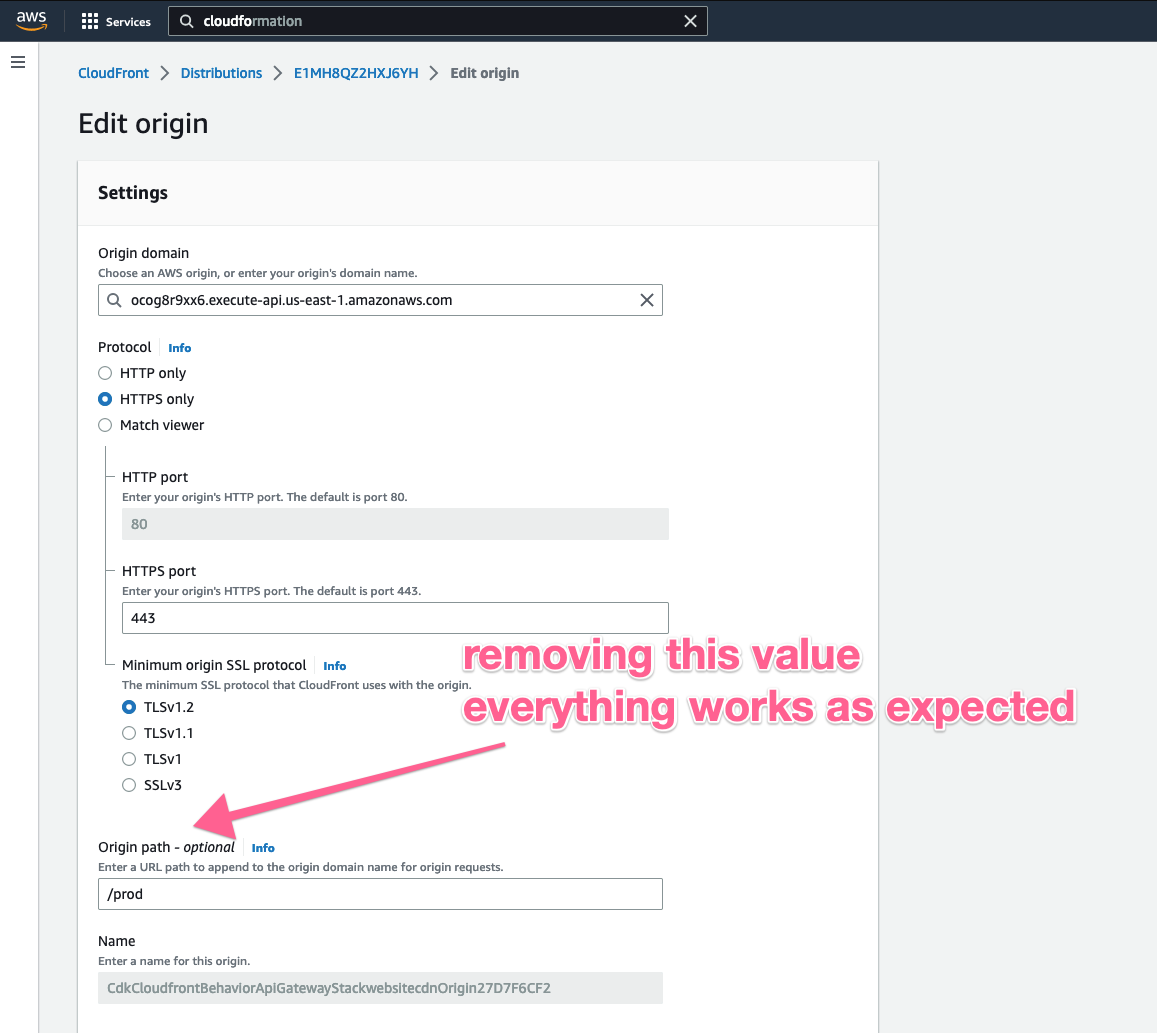 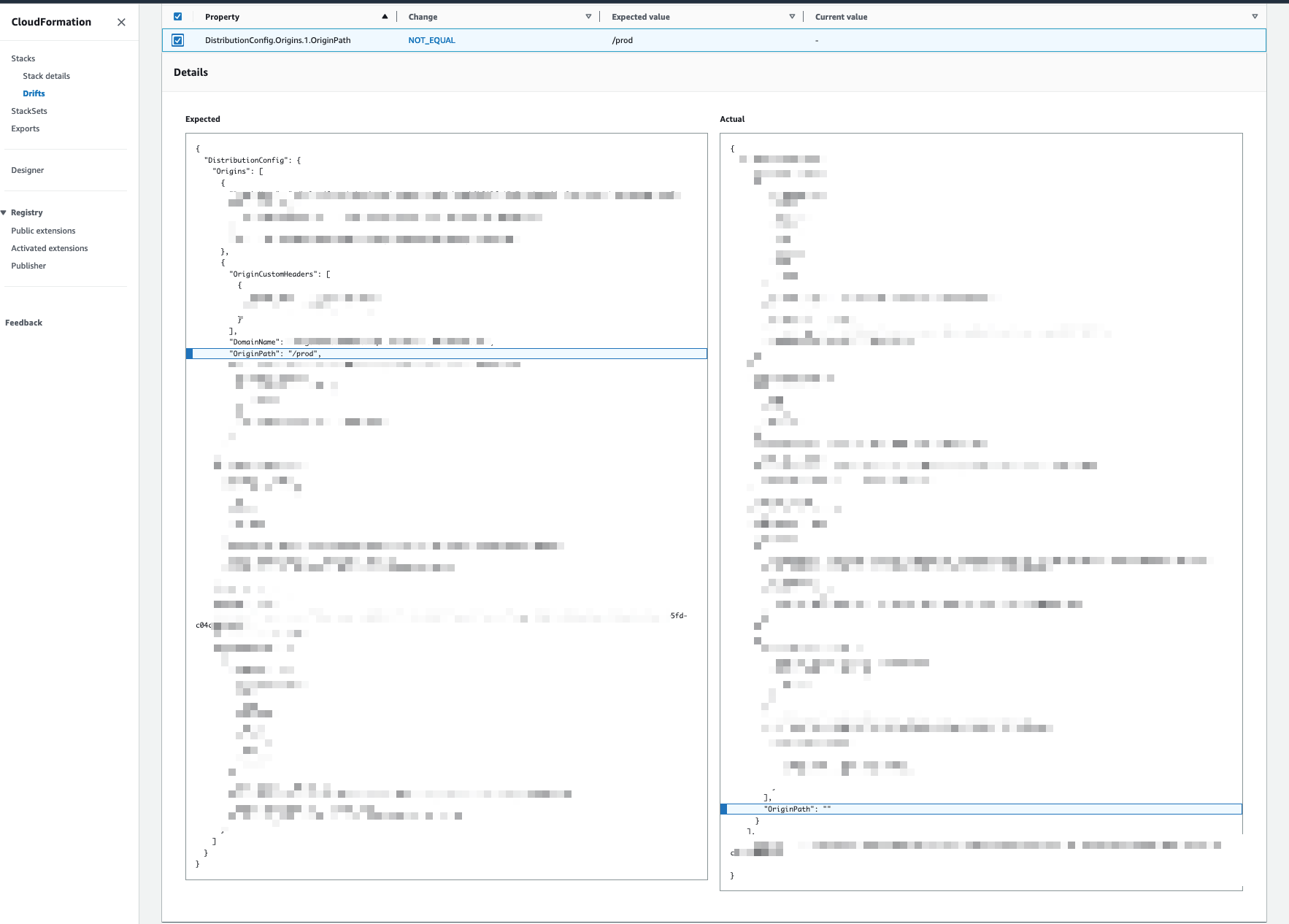 ### Workaround - To fix the problem described above, I need to use a custom `cdk.aws_cloudfront_origins.HttpOrigin` construct Replace the `apiOrigin` construct in the example above by: ```typescript const apiOrigin = new origins.HttpOrigin( `${api.restApiId}.execute-api.${cdk.Aws.REGION}.${cdk.Aws.URL_SUFFIX}`, { originSslProtocols: [cloudfront.OriginSslPolicy.TLS_V1_2], protocolPolicy: cloudfront.OriginProtocolPolicy.HTTPS_ONLY, } ); ``` ### Solution - This PR allows the customization of `apigateway.RestApi` by extending its props from `cloudfront.OriginProps` - Allowing the consumer to pass a `props.originPath` to the `RestApiOrigin` class



Current behavior
apigateway.RestApisplits therestApi.urland uses the stage name asoriginPath/ "Origin path - optional" option in the CloudFront Origin by defaultIssue / Limitation
My API Gateway receives an extra
/<api-gateway-stage>/in its event path and doesn't trigger the correct lambda integration.The below CDK example reproduces the behavior mentioned above:
The above will have the following URLs:
https://<api-gateway-url>/<api-gateway-stage>https://<cloudfront-distribution-url>/some-image.png=> Default Behavior, S3 Buckethttps://<cloudfront-distribution-url>/<api-gateway-stage>=> API Gateway forward requestBecause the CloudFront Origin created by
RestApiOriginappends the<api-gateway-stage>in its CloudFront Origin "Origin Path - optional" option, when usinghttps://<cloudfront-distribution-url>/<api-gateway-stage>/methe API Gateway receives/<api-gateway-stage>/<api-gateway-stage>/meinstead of/<api-gateway-stage>/meRemoving the "Origin Path - optional" value, fixes the problem.
Workaround
cdk.aws_cloudfront_origins.HttpOriginconstructReplace the
apiOriginconstruct in the example above by:Solution
apigateway.RestApiby extending its props fromcloudfront.OriginPropsprops.originPathto theRestApiOriginclass