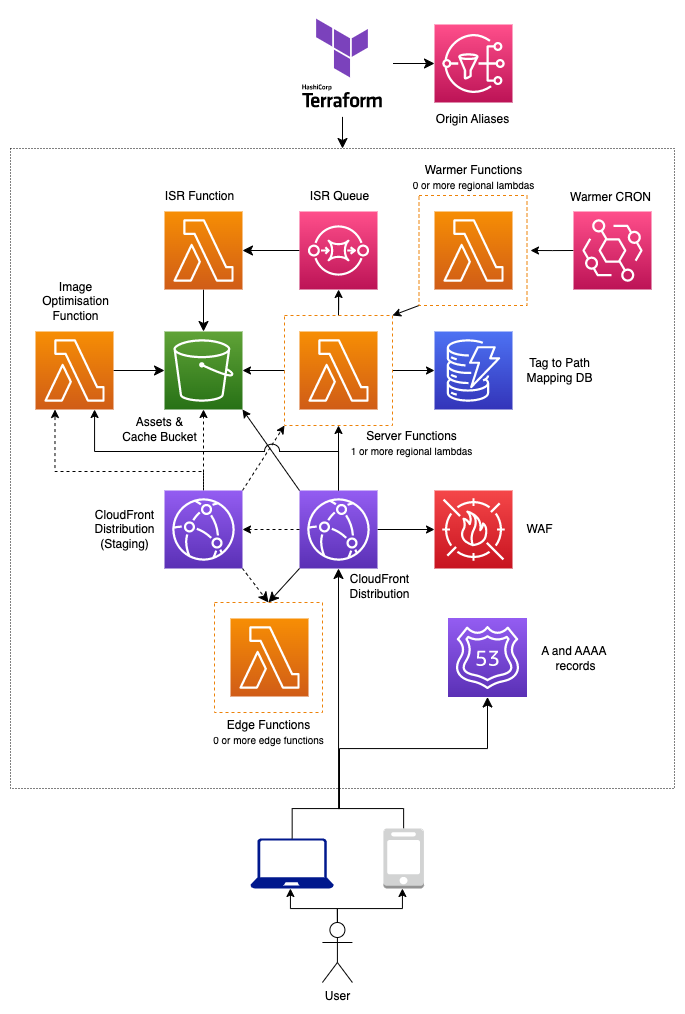
This module allows you to deploy a next.js website using Open Next to AWS utilizing lambda, S3 and CloudFront. Using this module will enable you to configure a single zone. If you want to manage multiple zones, please use the tf-aws-open-next-multi-zone module instead.
The module will allow you to configure the following resources.
The following are optional:
- Route 53 (A and AAAA records)
- WAF
- Staging Distribution
- Warmer function
- Image Optimization function
- Tag to Path Mapping DB
See the module documentation section below for more info.
Note: This module uses multiple bash scripts to delete data, upload data and mutate resources outside of Terraform. This prevents Terraform from removing resources when they have changed and allows the staging distribution functionality to work correctly.
You must have bash and the AWS CLI available, the CLI must be configured to use the same credentials or environment variables as the default AWS provider for this functionality to work correctly.
If you need to destroy the Terraform resources, it is recommended that you enable force_destroy on the website bucket to delete the assets in the bucket when running a Terraform destory.
This module supports CloudFront continuous deployment. See the continuous deployment docs for instructions on how to leverage this capability.
See the backend server deployment docs for instructions to see the options.
For infomation on managing custom domains see the domain-config documentation
Below is the documentation for the Terraform module, outlining the providers, modules and resources required to deploy the website. The documentation includes the inputs that can be supplied (including any defaults) and what is outputted from the module.
By default, the module will zip all the necessary open-next artefacts as part of a Terraform deployment. To facilitate this, the .open-next folders need to be stored locally.
You can also choose to upload the artefacts to S3 and pass the reference in.
Note: the logic to automatically inject environment variables for lambda@edge functions will not run if you choose this option
Alternatively you can create the zip using your own tooling and supply the path to the zip file and the hash (SHA256 hash of the file encoded using Base64).
You must configure the AWS providers five times because some organizations use different accounts or roles for IAM, DNS, etc. The module has been designed to cater for these requirements. The server function is a separate provider to allow your backend resources to be deployed to a region, i.e. eu-west-1, and deploy the server function to another region, i.e. us-east-1, for lambda@edge. The global provider region should be set to us-east-1 to allow the auth-function, WAF, etc. to be configured correctly.
Below is an example setup.
provider "aws" {}
provider "aws" {
alias = "server_function"
}
provider "aws" {
alias = "iam"
}
provider "aws" {
alias = "dns"
}
provider "aws" {
alias = "global"
region = "us-east-1"
}| Name | Version |
|---|---|
| terraform | >= 1.4.0 |
| archive | >= 2.3.0 |
| aws | >= 5.46.0 |
| local | >= 2.4.0 |
| Name | Version |
|---|---|
| archive | 2.4.2 |
| aws | 5.46.0 |
| local | 2.5.1 |
| terraform | n/a |
| Name | Source | Version |
|---|---|---|
| additional_server_function | ../tf-aws-lambda | n/a |
| edge_function | ../tf-aws-lambda | n/a |
| image_optimisation_function | ../tf-aws-lambda | n/a |
| open_next_aliases | ../tf-aws-open-next-aliases | n/a |
| public_resources | ../tf-aws-open-next-public-resources | n/a |
| revalidation_function | ../tf-aws-lambda | n/a |
| s3_assets | ../tf-aws-open-next-s3-assets | n/a |
| server_function | ../tf-aws-lambda | n/a |
| warmer_function | ../tf-aws-lambda | n/a |
| Name | Type |
|---|---|
| aws_cloudwatch_log_group.log_group | resource |
| aws_dynamodb_table.isr_table | resource |
| aws_lambda_event_source_mapping.revalidation_queue_source | resource |
| aws_lambda_permission.additional_server_function_url_permission | resource |
| aws_lambda_permission.image_optimisation_function_url_permission | resource |
| aws_lambda_permission.server_function_url_permission | resource |
| aws_s3_bucket.bucket | resource |
| aws_s3_bucket_policy.bucket_policy | resource |
| aws_sqs_queue.revalidation_queue | resource |
| local_file.edge_functions_modifications | resource |
| local_file.lambda_at_edge_modifications | resource |
| terraform_data.isr_table_item | resource |
| terraform_data.update_aliases | resource |
| archive_file.additional_server_function | data source |
| archive_file.edge_function | data source |
| archive_file.image_optimisation_function | data source |
| archive_file.revalidation_function | data source |
| archive_file.server_function | data source |
| archive_file.warmer_function | data source |
| aws_region.current | data source |
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| additional_server_functions | Default configutation for all additional server functions with the ability to override the configuration per function. This feature requires open next v3. By default, the module will create a new zip from the server function code on disk. However, you can override this by supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. Possible values for backend_deployment_type: - REGIONAL_LAMBDA_WITH_AUTH_LAMBDA - REGIONAL_LAMBDA_WITH_OAC - REGIONAL_LAMBDA_WITH_OAC_AND_ANY_PRINCIPAL - REGIONAL_LAMBDA See https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/docs/backend-server-deployments.md for a complete breakdown of the different backend options. |
object({ |
{} |
no |
| aliases | The production and staging aliases to use | object({ |
null |
no |
| behaviours | Override the default behaviour config | object({ |
{} |
no |
| cache_control_immutable_assets_regex | Regex to set public,max-age=31536000,immutable on immutable resources | string |
"^.*(\\.next)$" |
no |
| cloudwatch_log | The default cloudwatch log group configuration. This can be overridden for each function." Possible values for deployment: - PER_FUNCTION (default) - SHARED_PER_ZONE - USE_EXISTING When deployment is set to SHARED_PER_ZONE or USE_EXISTING, name is mandatory.For SHARED_PER_ZONE, the name will include the aws/lambda namespace and the supplied prefix and suffixFor USE_EXISTING, the name will represent the log group name (including prefix) |
object({ |
{} |
no |
| content_types | The MIME type mapping and default for artefacts generated by Open Next | object({ |
{} |
no |
| continuous_deployment | Configuration for continuous deployment config for CloudFront See https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/docs/continuous-deployments.md for a complete breakdown of how to use continuous deployment. |
object({ |
{} |
no |
| custom_error_responses | Allow custom error responses to be set on the distributions NOTE: These custom error pages only apply to response codes from the origins. To configure custom error responses for status codes returned by WAF, please configure the custom error responses in WAF. |
list(object({ |
[] |
no |
| distribution | Configuration for the CloudFront distribution. Possible values for deployment are: - NONE - CREATE The module has a local copy of the x-forwarded host CloudFront function code by default. The code can be seen at https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/modules/tf-aws-open-next-public-resources/code/xForwardedHost.js (open next v2) and https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/modules/tf-aws-open-next-public-resources/code/cloudfrontFunctionOpenNextV3.js (open next v3). This code can be overridden by passing in the javascript function as a string to the code argument under the x_forwarded_host_function object. An example can be seen below.x_forwarded_host_function = {The auth function is deployed if the server function backend_deployment_type is set to EDGE_LAMBDA.The module has a local copy of the auth function code, which will be deployed by default. The code can be seen at https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/modules/tf-aws-open-next-public-resources/code/auth/index.js. You can override this to supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. Possible values for the auth_function deployment are: - NONE - USE_EXISTING - CREATE - DETACH The auth function arn is mandatory when deployment is set to USE_EXISTING.When migrating from using the auth function to either public cloud functions or to using OAC, you should set the deployment on the auth_function to CREATE, then apply the changes. Then, you can set deployment to false in a subsequent change to clean up the function. If you run the server function as a lambda@edge, you should increase the deletion timeout to 2 hours 120m. As the lambda service needs to wait for the replicas to be removed, this often exceeds the default 10-minute deletion timeout. This extended timeout allows Terraform to poll for longer and should help mitigate Terraform failures; an example Terraform configuration can be seen below.auth_function = {As lambda@edge doesn't support environment variables, the environment variables are injected into the source code before the zip is generated. NOTE: If the lambda function code is supplied as a zip or via an S3 reference, this code modification will not occur Terraform does not manage cloudwatch log groups for the auth function; the lambda service creates the log group when the function runs in each region. CloudFront supports Origin Access Control (OAC) for lambda URLs. The possible values for the deployment options are: - NONE - CREATE NOTE: If the server function or image optimisation function backend deployment types use OAC, then the OAC will be created. As there is a limit on the number of cache policies associated with an AWS account, you can either configure the module to create the cache policy or use an existing one. The possible values for the cache policy deployment are: - USE_EXISTING - CREATE If cache policy deployment is set to USE_EXISTING, then ID, is a required field.WARNING: The distribution is fundamental to the architecture, and the module is optional to facilitate sharing a distribution for multi-zone deployments and to support edge cases not supported by the module. With that said, it is not recommended to supply a distribution. |
object({ |
{} |
no |
| domain_config | Configuration for CloudFront distribution domain See https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/docs/domain-config.md for a complete breakdown of the different domain configuration options. |
object({ |
null |
no |
| edge_functions | Default configutation for all edge functions with the ability to override the configuration per edge function By default, the module will create a new zip from the edge function code on disk. However, you can override this by supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. This feature requires open next v3. NOTE: Terraform does not manage cloudwatch log groups; instead, the lambda service creates the log group when the function runs in each region. The module OPEN_NEXT_ORIGIN environment variable for each edge function, as per the open next documentation for middleware. You have the ability to remove this environment variable by setting the include_open_next_origin_env_variable to false or override this value by setting an environment variable with the same name via the additional_environment_variables attribute.You should increase the deletion timeout to 2 hours 120m. As the lambda service needs to wait for the replicas to be removed, this often exceeds the default 10-minute deletion timeout. This extended timeout allows Terraform to poll for longer and should help mitigate Terraform failures; an example Terraform configuration can be seen below.timeouts = {As lambda@edge doesn't support environment variables, the environment variables are injected into the source code before the zip is generated.NOTE: If the lambda function code is supplied as a zip or via an S3 reference, this code modification will not occur |
object({ |
{} |
no |
| folder_path | The path to the open next artifacts | string |
n/a | yes |
| function_architecture | The default instruction set architecture for the lambda functions. This can be overridden for each function. | string |
"arm64" |
no |
| iam | The default IAM configuration. This can be overridden for each function. | object({ |
{} |
no |
| image_optimisation_function | Configuration for the image optimisation function. By default, the module will create a new zip from the image optimisation function code on disk. However, you can override this by supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. Possible values for backend_deployment_type: - REGIONAL_LAMBDA_WITH_AUTH_LAMBDA - REGIONAL_LAMBDA_WITH_OAC - REGIONAL_LAMBDA_WITH_OAC_AND_ANY_PRINCIPAL - REGIONAL_LAMBDA See https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/docs/backend-server-deployments.md for a complete breakdown of the different backend options. If you do not want to provision the image optimisation function, you can set create to false. |
object({ |
{} |
no |
| logging_config | The default function logging configuration. The log group is determined by the cloudwatch_log variable. This can be overridden for each function. | object({ |
null |
no |
| open_next_version | The version of open next that is used | string |
"v2.x.x" |
no |
| prefix | A prefix which will be attached to the resource name to ensure resources are random | string |
null |
no |
| revalidation_function | Configuration for the revalidation function. By default, the module will create a new zip from the revalidation function code on disk. However, you can override this by supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. This function is deployed to the region specified on the default AWS Terraform provider. |
object({ |
{} |
no |
| s3_exclusion_regex | A regex of files to exclude from the s3 copy | string |
null |
no |
| s3_folder_prefix | An optional folder to store uploaded assets and cached files under | string |
null |
no |
| scripts | Modify default script behaviours | object({ |
{} |
no |
| server_function | Configuration for the server function. By default, the module will create a new zip from the server function code on disk. However, you can override this by supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. Possible values for backend_deployment_type: - REGIONAL_LAMBDA_WITH_AUTH_LAMBDA - REGIONAL_LAMBDA_WITH_OAC - REGIONAL_LAMBDA_WITH_OAC_AND_ANY_PRINCIPAL - REGIONAL_LAMBDA - EDGE_LAMBDA (only supported with open next v2) See https://github.com/RJPearson94/terraform-aws-open-next/blob/v3.0.3/docs/backend-server-deployments.md for a complete breakdown of the different backend options. NOTE: When backend_deployment_type is set to EDGE_LAMBDA, Terraform does not manage cloudwatch log groups; instead, the lambda service creates the log group when the function runs in each region. If you run the server function as a lambda@edge, you should increase the deletion timeout to 2 hours 120m. As the lambda service needs to wait for the replicas to be removed, this often exceeds the default 10-minute deletion timeout. This extended timeout allows Terraform to poll for longer and should help mitigate Terraform failures; an example Terraform configuration can be seen below.timeouts = {As lambda@edge doesn't support environment variables, the environment variables are injected into the source code before the zip is generated.NOTE: If the lambda function code is supplied as a zip or via an S3 reference, this code modification will not occur |
object({ |
{} |
no |
| suffix | A suffix which will be attached to the resource name to ensure resources are random | string |
null |
no |
| tag_mapping_db | Configuration for the ISR tag mapping database By default, the module uploads the items in the dynamodb-cache JSON file stored locally. The cache alias is appended to each item in the DB. Possible values for deployment: - NONE - CREATE The read and write capacity for the Global Secondary Index (GSI) can be overridden; however, the table's read and write capacity will be used by default. |
object({ |
{} |
no |
| vpc | The default VPC configuration for the lambda resources. This can be overridden for each function. | object({ |
null |
no |
| waf | Configuration for the CloudFront distribution WAF. Possible values for the WAF deployment are: - NONE - USE_EXISTING - CREATE - DETACH The web_acl_id is mandatory when deployment is set to USE_EXISTING.When configuring basic authentication, the encoded username and password are marked as sensitive. This can be turned off by setting mark_as_sensitive to false; however, a bug in Terraform v1.6.0 prevented this from working. If this occurs, please upgrade to at least v1.6.1.Possible values for the WAF default action are: - ALLOW - BLOCK The module provides the ability to configure recommended WAF rules to guard against SQL Injection (sqli), account takeover protection and account creation fraud prevention. Multiple rate limits can be configured with each limit applied across all geographic regions or limited to a specific region. The possible values for the action are: - COUNT - BLOCK The possible values for the action of each additional rule are: - COUNT - BLOCK When IP address restrictions are used as part of additional rules or enforcing basic auth, the possible values for the action are: - BYPASS - BLOCK Examples of maintenance pages, basic auth, and more can be found at https://github.com/RJPearson94/terraform-aws-open-next-examples. |
object({ |
{} |
no |
| warmer_function | Configuration for the warmer function. By default, the module will create a new zip from the warmer function code on disk. However, you can override this by supplying a zip file containing the lambda code with either a local reference or a reference to the zip in an S3 bucket. If the warmer function is enabled, you can conditionally choose to warm the staging distribution. Enabling this will provision another lambda function. By default, the warmer for the staging distribution will use the same concurrency value as the production distribution. However, you can override this value by specifying a concurrency value for the warm_staging object.This function is deployed to the region specified on the default AWS Terraform provider. |
object({ |
{} |
no |
| website_bucket | Configuration for the website S3 bucket By default, the module will upload the assets and cache folders that are stored locally. Possible values for deployment: - NONE - CREATE This bucket is deployed to the region specified on the default AWS Terraform provider. If deployment is set to NONE, then arn, region, name & domain_name are required fields.WARNING: The bucket is fundamental to the architecture, and the module is optional to facilitate sharing a bucket for multi-zone deployments and to support edge cases not supported by the module. With that said, it is not recommended to supply a bucket. |
object({ |
{} |
no |
| zone_suffix | An optional zone suffix to add to the assets and cache folder to allow files to be loaded correctly | string |
null |
no |
| Name | Description |
|---|---|
| alias_details | The alias config |
| alternate_domain_names | Extra CNAMEs (alternate domain names) associated with the cloudfront distribution |
| behaviours | The behaviours for the zone |
| bucket_arn | The ARN of the s3 bucket |
| bucket_name | The name of the s3 bucket |
| cloudfront_distribution_id | The ID for the cloudfront distribution |
| cloudfront_staging_distribution_id | The ID for the cloudfront staging distribution |
| cloudfront_url | The URL for the cloudfront distribution |
| custom_error_responses | The custom error responses for the zone |
| zone_config | The zone config |