This project is provided for educational and research purposes only. By accessing or using this repository, you agree to the following:
You will not use this code in any way that violates applicable laws or terms of service of any software or service.
The author is not responsible for any misuse of this project or any consequences resulting from its use.
This project showcases my programming skills, problem-solving abilities, and interest in reverse engineering. It is not an endorsement of any illegal or unethical activities.
Bypass hooks an imported function inside dxgkrnl.sys. This imported function resides in watchdog.sys, and is called when NtDxgkCreateTrackedWorkload gets called from win32u.dll
NtDxgkCreateTrackedWorkload syscall win32u.dll -> NtDxgkCreateTrackedWorkload dxgkrnl.sys -> (half way through function) WdLogEvent5_WdError watchdog.sys
This hook could be detcted if two things occur
- If EAC scans watchdog.sys for hooks (%99 doubt they do, its just some random windows non-pg protcted module why would they)
- If EAC scans and compares all loaded drivers (doubt too would cause to many false positives probaly?)
To pass the struct I used shared memory. I think the bypass is safe, although the renderering method is probaly not. Method I used to render: https://github.com/thesecretclub/window_hijack
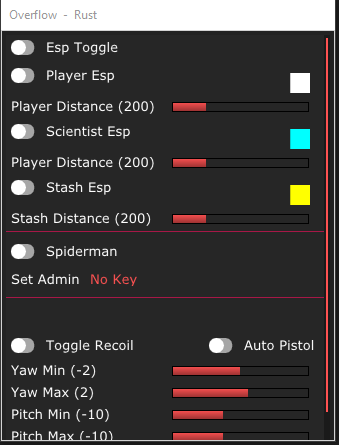
- Recoil Control
- Auto Pistol
- Spiderman
- Admin flags
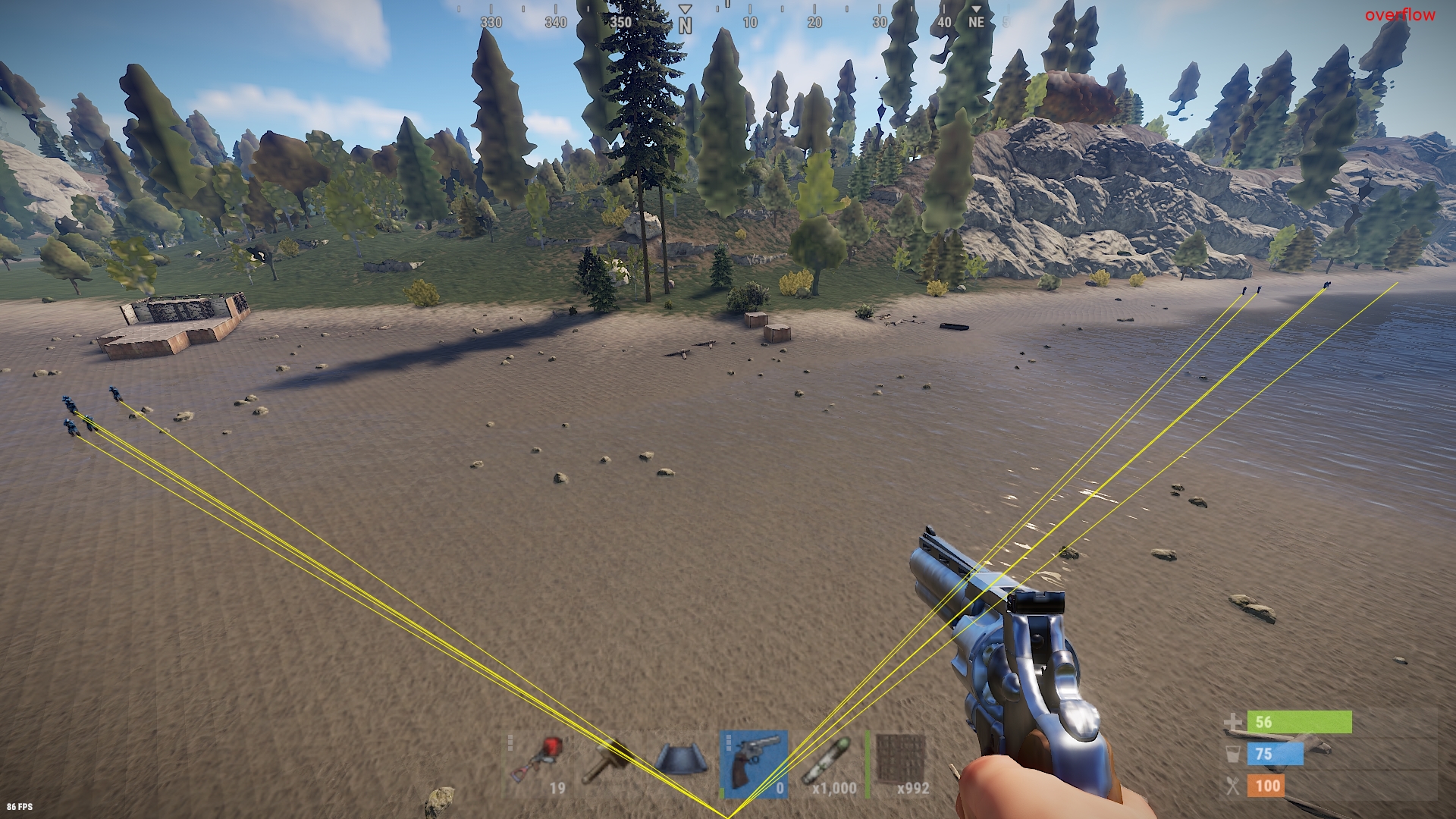
- ESP
- Player
- Scientist
- Stash
- Right click on "OverflowR6Rust.sln" in the first folder.
- Open it in a text editor such as notepad++
- Change the directories to where your files are located
- Me
- Window Hijacking https://github.com/thesecretclub/window_hijack
- Hooking class/library: https://github.com/adrianyy/kernelhook