-
|
-
+
{{.Code}}
-
+
{{.Title}}
-
+
{{.Instruction}}
-- If the page does not redirect, the magic link may have expired. -
+
+ Please request another magic link.
+
+ This magic link is invalid for one of the below reasons:
+
-
+
- The magic link has expired. +
- The magic link never existed. +
- The magic link has already been used. +
- Your web browser failed an automated check. +
 -
-  +
+  +
+  +
+ +
+ 
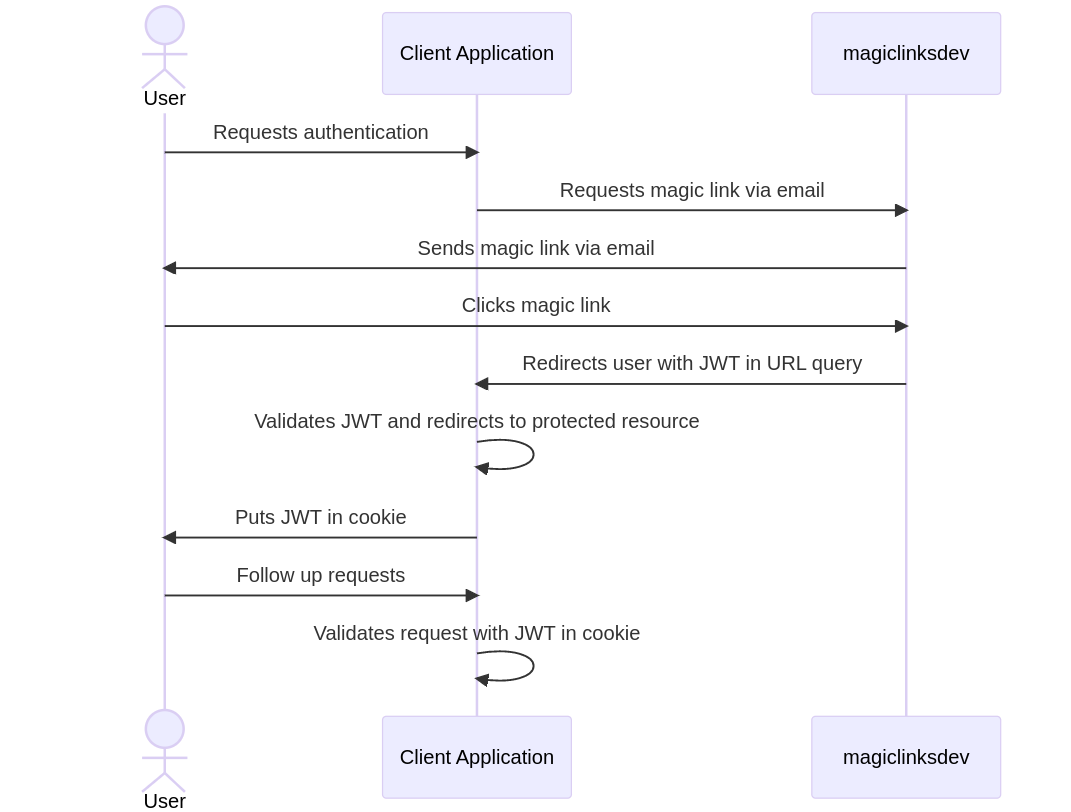 -
-## Implementing a client application
+## Suggested Magic Link Workflow
+
-
-## Implementing a client application
+## Suggested Magic Link Workflow
+ -Client applications are programs that use the **magiclinksdev** project to authenticate their users. Check out the
-[**SDKs**](https://docs.magiclinks.dev/sdks) page to get started with an existing SDK. If you can't find an SDK for your
-language, you can use the [**Specification**](https://docs.magiclinks.dev/specification) to implement your own client by
-hand or code generation. To learn more about the client workflow, check out the
-[**Workflow**](https://docs.magiclinks.dev/workflow) page.
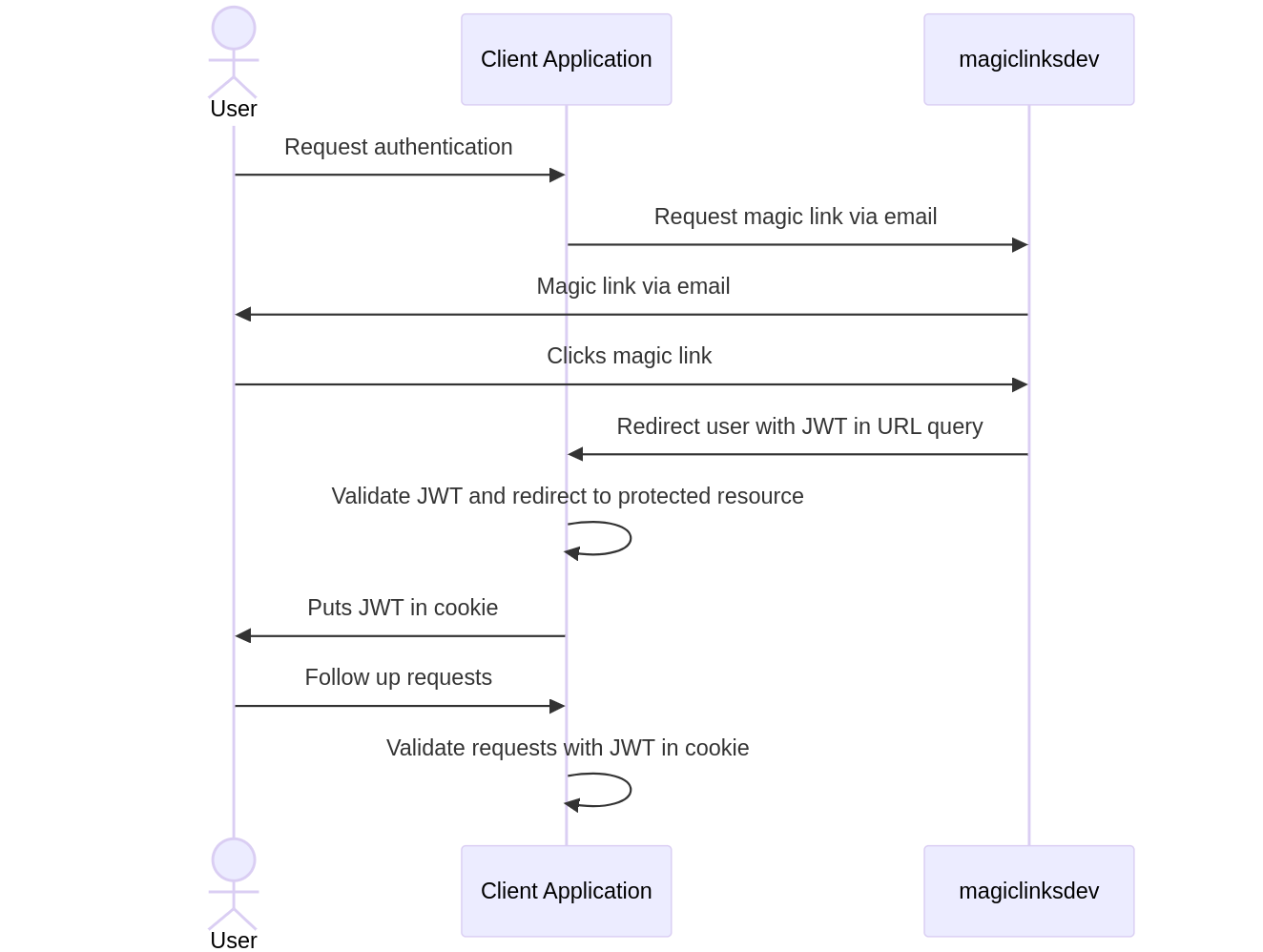
+## Suggested OTP Workflow
+
-Client applications are programs that use the **magiclinksdev** project to authenticate their users. Check out the
-[**SDKs**](https://docs.magiclinks.dev/sdks) page to get started with an existing SDK. If you can't find an SDK for your
-language, you can use the [**Specification**](https://docs.magiclinks.dev/specification) to implement your own client by
-hand or code generation. To learn more about the client workflow, check out the
-[**Workflow**](https://docs.magiclinks.dev/workflow) page.
+## Suggested OTP Workflow
+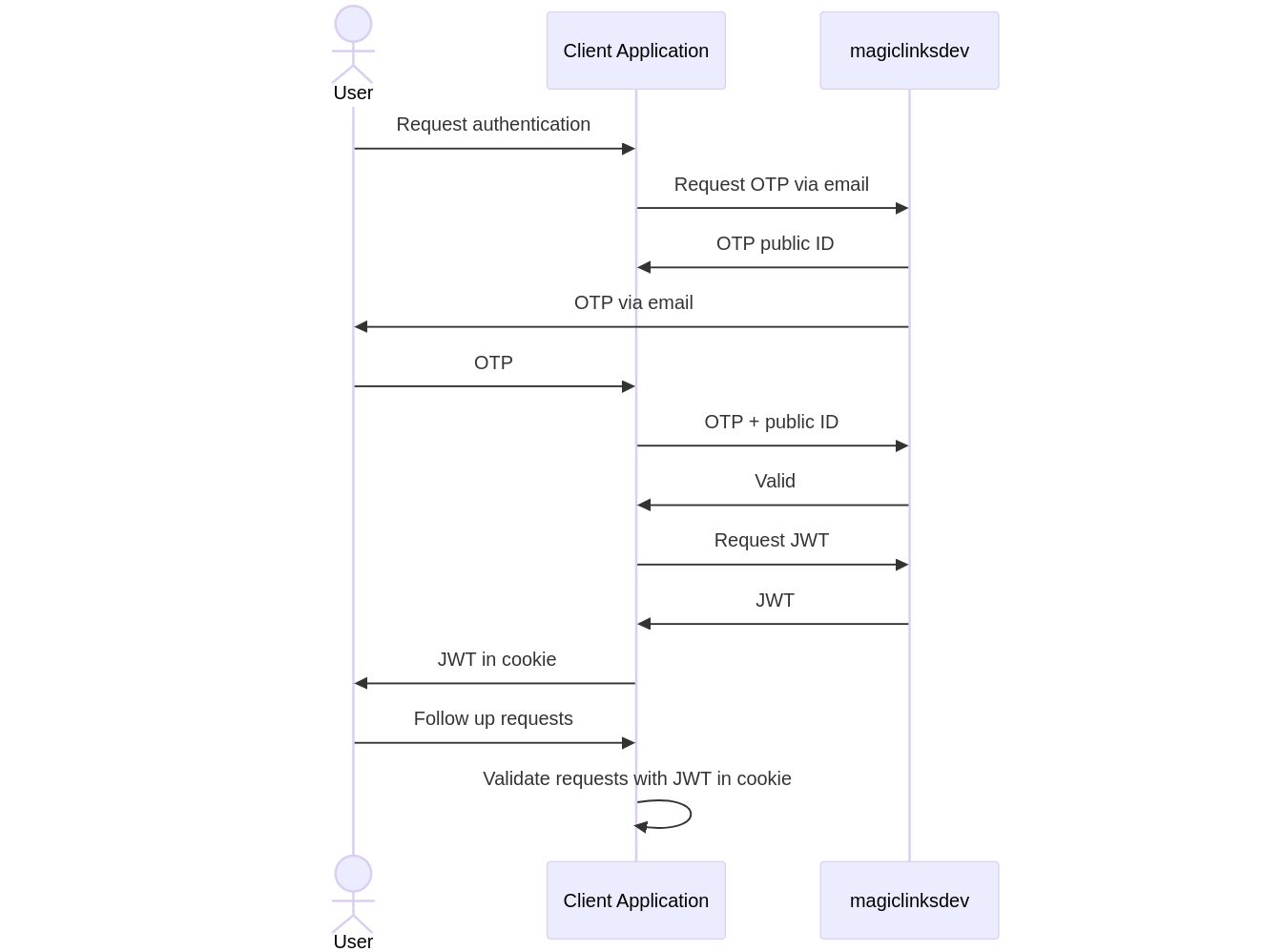 ## Self-hosting the service
-The **magiclinksdev** project can be self-hosted. Check out the [**Quickstart**](https://docs.magiclinks.dev/quickstart)
-page to get started in minutes. For reference on configuring your self-hosted instance, check out the
-[**Configuration**](https://docs.magiclinks.dev/configuration).
+The **magiclinksdev** project is open-source and can be self-hosted. Check out the [**Quickstart**](https://docs.magiclinks.dev/self-host-quickstart) page
+to get started in minutes. For reference on configuring your self-hosted instance, check out the
+[**Configuration**](https://docs.magiclinks.dev/self-host-configuration).
## Source code and license
The **magiclinksdev** project is [open source on GitHub](https://github.com/MicahParks/magiclinksdev) and licensed
-under [Apache License 2.0](https://github.com/MicahParks/magiclinksdev/blob/master/LICENSE).
+under [**Apache License 2.0**](https://github.com/MicahParks/magiclinksdev/blob/master/LICENSE).
## Optional SaaS platform
diff --git a/buildDocker.sh b/buildDocker.sh
index 18c498f..95a4769 100644
--- a/buildDocker.sh
+++ b/buildDocker.sh
@@ -7,16 +7,16 @@ if [ "$1" = "push" ]; then
then
exit 1
fi
- docker build --pull --push --file nop.Dockerfile --tag micahparks/magiclinksdevmulti .
+ docker build --pull --push --file multi.Dockerfile --tag micahparks/magiclinksdevmulti .
docker build --pull --push --file nop.Dockerfile --tag micahparks/magiclinksdevnop .
docker build --pull --push --file ses.Dockerfile --tag micahparks/magiclinksdevses .
docker build --pull --push --file sendgrid.Dockerfile --tag micahparks/magiclinksdevsendgrid .
- docker build --pull --push --file nop.Dockerfile --tag "micahparks/magiclinksdevmulti:$TAG" .
+ docker build --pull --push --file multi.Dockerfile --tag "micahparks/magiclinksdevmulti:$TAG" .
docker build --pull --push --file nop.Dockerfile --tag "micahparks/magiclinksdevnop:$TAG" .
docker build --pull --push --file ses.Dockerfile --tag "micahparks/magiclinksdevses:$TAG" .
docker build --pull --push --file sendgrid.Dockerfile --tag "micahparks/magiclinksdevsendgrid:$TAG" .
else
- docker build --pull --file nop.Dockerfile --tag micahparks/magiclinksdevmulti .
+ docker build --pull --file multi.Dockerfile --tag micahparks/magiclinksdevmulti .
docker build --pull --file nop.Dockerfile --tag micahparks/magiclinksdevnop .
docker build --pull --file ses.Dockerfile --tag micahparks/magiclinksdevses .
docker build --pull --file sendgrid.Dockerfile --tag micahparks/magiclinksdevsendgrid .
diff --git a/client/client.go b/client/client.go
index ec84d23..dc76e6c 100644
--- a/client/client.go
+++ b/client/client.go
@@ -22,8 +22,8 @@ import (
)
const (
- // SaaSBaseURL is the base URL for the SaaS offering. The SaaS offering is optional and the magiclinksdev project
- // can be self-hosted.
+ // SaaSBaseURL is the base URL for the SaaS platform. The SaaS platform is optional and the magiclinksdev project
+ // is open-source and can be self-hosted.
SaaSBaseURL = "https://magiclinks.dev"
// SaaSIss is the iss claim for JWTs in the SaaS offering.
SaaSIss = SaaSBaseURL
@@ -43,7 +43,7 @@ type Options struct {
HTTP *http.Client
}
-// Client is a client for the magiclinksdev project.
+// Client is the official Golang API client for the magiclinksdev project.
type Client struct {
apiKey uuid.UUID
aud uuid.UUID
@@ -54,9 +54,9 @@ type Client struct {
}
// New creates a new magiclinksdev client. The apiKey and aud are tied to the service account being used. The baseURL is
-// the HTTP(S) location of the magiclinksdev deployment. Only use HTTPS in production. For the SaaS offering, use the
+// the HTTP(S) location of the magiclinksdev deployment. Only use HTTPS in production. For the SaaS platform, use the
// SaaSBaseURL constant. The iss is the issuer of the JWTs, which is in the configuration of the magiclinksdev
-// deployment. For the SaaS offering, use the SaaSIss constant. Providing an empty string for the iss will disable
+// deployment. For the SaaS platform, use the SaaSIss constant. Providing an empty string for the iss will disable
// issuer validation.
func New(apiKey, aud uuid.UUID, baseURL, iss string, options Options) (Client, error) {
u, err := url.Parse(baseURL)
@@ -96,8 +96,8 @@ func New(apiKey, aud uuid.UUID, baseURL, iss string, options Options) (Client, e
}
// LocalJWTValidate validates a JWT locally. If the claims argument is not nil, its value will be passed directly to
-// jwt.ParseWithClaims. The claims should be unmarshalled into the provided non-nil pointer after the function call. See
-// the documentation for jwt.ParseWithClaims for more information. Registered JWT claims will be validated regardless if
+// jwt.ParseWithClaims. The claims should be unmarshalled into the claims argument if it is a non-nil pointer. See the
+// documentation for jwt.ParseWithClaims for more information. Registered JWT claims will be validated regardless if
// claims are specified or not.
func (c Client) LocalJWTValidate(token string, claims jwt.Claims) (*jwt.Token, error) {
if c.keyf == nil {
@@ -136,15 +136,6 @@ func (c Client) LocalJWTValidate(token string, claims jwt.Claims) (*jwt.Token, e
return t, nil
}
-// EmailLinkCreate calls the /email-link/create endpoint and returns the appropriate response.
-func (c Client) EmailLinkCreate(ctx context.Context, req model.EmailLinkCreateRequest) (model.EmailLinkCreateResponse, model.Error, error) {
- resp, errResp, err := request[model.EmailLinkCreateRequest, model.EmailLinkCreateResponse](ctx, c, http.StatusCreated, network.PathEmailLinkCreate, req)
- if err != nil {
- return model.EmailLinkCreateResponse{}, errResp, fmt.Errorf("failed to create email link: %w", err)
- }
- return resp, errResp, nil
-}
-
// JWTCreate calls the /jwt/create endpoint and returns the appropriate response.
func (c Client) JWTCreate(ctx context.Context, req model.JWTCreateRequest) (model.JWTCreateResponse, model.Error, error) {
resp, errResp, err := request[model.JWTCreateRequest, model.JWTCreateResponse](ctx, c, http.StatusCreated, network.PathJWTCreate, req)
@@ -165,16 +156,52 @@ func (c Client) JWTValidate(ctx context.Context, req model.JWTValidateRequest) (
return resp, errResp, nil
}
-// LinkCreate calls the /link/create endpoint and returns the appropriate response.
-func (c Client) LinkCreate(ctx context.Context, req model.LinkCreateRequest) (model.LinkCreateResponse, model.Error, error) {
- resp, errResp, err := request[model.LinkCreateRequest, model.LinkCreateResponse](ctx, c, http.StatusCreated, network.PathLinkCreate, req)
+// MagicLinkCreate calls the /magic-link/create endpoint and returns the appropriate response.
+func (c Client) MagicLinkCreate(ctx context.Context, req model.MagicLinkCreateRequest) (model.MagicLinkCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.MagicLinkCreateRequest, model.MagicLinkCreateResponse](ctx, c, http.StatusCreated, network.PathMagicLinkCreate, req)
+ if err != nil {
+ return model.MagicLinkCreateResponse{}, errResp, fmt.Errorf("failed to create link: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// MagicLinkEmailCreate calls the /magic-link-email/create endpoint and returns the appropriate response.
+func (c Client) MagicLinkEmailCreate(ctx context.Context, req model.MagicLinkEmailCreateRequest) (model.MagicLinkEmailCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.MagicLinkEmailCreateRequest, model.MagicLinkEmailCreateResponse](ctx, c, http.StatusCreated, network.PathMagicLinkEmailCreate, req)
+ if err != nil {
+ return model.MagicLinkEmailCreateResponse{}, errResp, fmt.Errorf("failed to create email link: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// OTPCreate calls the /otp/create endpoint and returns the appropriate response.
+func (c Client) OTPCreate(ctx context.Context, req model.OTPCreateRequest) (model.OTPCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.OTPCreateRequest, model.OTPCreateResponse](ctx, c, http.StatusCreated, network.PathOTPCreate, req)
+ if err != nil {
+ return model.OTPCreateResponse{}, errResp, fmt.Errorf("failed to create OTP: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// OTPValidate calls the /otp/validate endpoint and returns the appropriate response.
+func (c Client) OTPValidate(ctx context.Context, req model.OTPValidateRequest) (model.OTPValidateResponse, model.Error, error) {
+ resp, errResp, err := request[model.OTPValidateRequest, model.OTPValidateResponse](ctx, c, http.StatusOK, network.PathOTPValidate, req)
+ if err != nil {
+ return model.OTPValidateResponse{}, errResp, fmt.Errorf("failed to validate OTP: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// OTPEmailCreate calls the /otp-email/create endpoint and returns the appropriate response.
+func (c Client) OTPEmailCreate(ctx context.Context, req model.OTPEmailCreateRequest) (model.OTPEmailCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.OTPEmailCreateRequest, model.OTPEmailCreateResponse](ctx, c, http.StatusCreated, network.PathOTPEmailCreate, req)
if err != nil {
- return model.LinkCreateResponse{}, errResp, fmt.Errorf("failed to create link: %w", err)
+ return model.OTPEmailCreateResponse{}, errResp, fmt.Errorf("failed to create email OTP: %w", err)
}
return resp, errResp, nil
}
-// Ready calls the /ready endpoint. An error is returned if the service is not ready.
+// Ready calls the /ready endpoint. An error is returned if the service is not ready to accept requests.
func (c Client) Ready(ctx context.Context) error {
u, err := c.baseURL.Parse(network.PathReady)
if err != nil {
diff --git a/client/client_test.go b/client/client_test.go
index cea7c0e..4bfdf07 100644
--- a/client/client_test.go
+++ b/client/client_test.go
@@ -39,13 +39,13 @@ var (
_, attackerKey, _ = ed25519.GenerateKey(nil)
redirectPath, _ = url.Parse(mld.DefaultRelativePathRedirect)
- jwtCreateArgs = model.JWTCreateArgs{
- JWTClaims: mldtest.TClaims,
- JWTLifespanSeconds: 5,
+ jwtCreateParams = model.JWTCreateParams{
+ Claims: mldtest.TClaims,
+ LifespanSeconds: 5,
}
- linkArgs = model.LinkCreateArgs{
- JWTCreateArgs: jwtCreateArgs,
- LinkLifespan: 5,
+ linkParams = model.MagicLinkCreateParams{
+ JWTCreateParams: jwtCreateParams,
+ LifespanSeconds: 5,
RedirectQueryKey: magiclink.DefaultRedirectQueryKey,
RedirectURL: "http://example.com",
}
@@ -102,8 +102,8 @@ func TestEmailLinkCreate(t *testing.T) {
ctx := createCtx(t)
c := newClient(ctx, t)
- req := model.EmailLinkCreateRequest{
- EmailArgs: model.EmailLinkCreateArgs{
+ req := model.MagicLinkEmailCreateRequest{
+ MagicLinkEmailCreateParams: model.MagicLinkEmailCreateParams{
ButtonText: "Test button text",
Greeting: "Test greeting",
LogoClickURL: mldtest.LogoClickURL,
@@ -115,9 +115,9 @@ func TestEmailLinkCreate(t *testing.T) {
ToEmail: "customer@example.com",
ToName: "Test name",
},
- LinkArgs: linkArgs,
+ MagicLinkCreateParams: linkParams,
}
- resp, mldErr, err := c.EmailLinkCreate(ctx, req)
+ resp, mldErr, err := c.MagicLinkEmailCreate(ctx, req)
if err != nil {
t.Fatalf("Failed to create email link: %v.", err)
}
@@ -126,7 +126,7 @@ func TestEmailLinkCreate(t *testing.T) {
}
validateMetadata(t, resp.RequestMetadata)
- validateLinkResults(t, resp.EmailLinkCreateResults.LinkCreateResults)
+ validateLinkResults(t, resp.MagicLinkEmailCreateResults.MagicLinkCreateResults)
}
func TestJWTCreate(t *testing.T) {
@@ -179,7 +179,7 @@ func TestJWTValidate(t *testing.T) {
raw := jwtCreateHelper(ctx, t, c)
req := model.JWTValidateRequest{
- JWTValidateArgs: model.JWTValidateArgs{
+ JWTValidateParams: model.JWTValidateParams{
JWT: raw,
},
}
@@ -217,7 +217,7 @@ func TestJWTValidateForged(t *testing.T) {
}
req := model.JWTValidateRequest{
- JWTValidateArgs: model.JWTValidateArgs{
+ JWTValidateParams: model.JWTValidateParams{
JWT: raw,
},
}
@@ -237,10 +237,10 @@ func TestLinkCreate(t *testing.T) {
ctx := createCtx(t)
c := newClient(ctx, t)
- req := model.LinkCreateRequest{
- LinkArgs: linkArgs,
+ req := model.MagicLinkCreateRequest{
+ MagicLinkCreateParams: linkParams,
}
- resp, mldErr, err := c.LinkCreate(ctx, req)
+ resp, mldErr, err := c.MagicLinkCreate(ctx, req)
if err != nil {
t.Fatalf("Failed to create magic link: %v.", err)
}
@@ -249,7 +249,7 @@ func TestLinkCreate(t *testing.T) {
}
validateMetadata(t, resp.RequestMetadata)
- validateLinkResults(t, resp.LinkCreateResults)
+ validateLinkResults(t, resp.MagicLinkCreateResults)
}
func TestServiceAccountCreate(t *testing.T) {
@@ -257,7 +257,7 @@ func TestServiceAccountCreate(t *testing.T) {
c := newClient(ctx, t)
req := model.ServiceAccountCreateRequest{
- CreateServiceAccountArgs: model.ServiceAccountCreateArgs{},
+ ServiceAccountCreateParams: model.ServiceAccountCreateParams{},
}
resp, mldErr, err := c.ServiceAccountCreate(ctx, req)
if err != nil {
@@ -269,16 +269,16 @@ func TestServiceAccountCreate(t *testing.T) {
validateMetadata(t, resp.RequestMetadata)
- if resp.CreateServiceAccountResults.ServiceAccount.Admin {
+ if resp.ServiceAccountCreateResults.ServiceAccount.Admin {
t.Fatalf("Created service account should not be an admin.")
}
- if resp.CreateServiceAccountResults.ServiceAccount.UUID == uuid.Nil {
+ if resp.ServiceAccountCreateResults.ServiceAccount.UUID == uuid.Nil {
t.Fatalf("Created service account should have non-nil UUID.")
}
- if resp.CreateServiceAccountResults.ServiceAccount.Aud == uuid.Nil {
+ if resp.ServiceAccountCreateResults.ServiceAccount.Aud == uuid.Nil {
t.Fatalf("Created service account should have non-nil audience UUID.")
}
- if resp.CreateServiceAccountResults.ServiceAccount.APIKey == uuid.Nil {
+ if resp.ServiceAccountCreateResults.ServiceAccount.APIKey == uuid.Nil {
t.Fatalf("Created service account should have non-nil API key.")
}
}
@@ -291,7 +291,7 @@ func createCtx(t *testing.T) context.Context {
func jwtCreateHelper(ctx context.Context, t *testing.T, c Client) string {
req := model.JWTCreateRequest{
- JWTCreateArgs: jwtCreateArgs,
+ JWTCreateParams: jwtCreateParams,
}
resp, mldErr, err := c.JWTCreate(ctx, req)
if err != nil {
@@ -324,12 +324,12 @@ func jwtCreateHelper(ctx context.Context, t *testing.T, c Client) string {
func newClient(ctx context.Context, t *testing.T) Client {
conf := config.Config{
- AdminConfig: []model.AdminCreateArgs{
+ AdminCreateParams: []model.AdminCreateParams{
{
- APIKey: mldtest.APIKey,
- Aud: mldtest.Aud,
- UUID: mldtest.SAUUID,
- ServiceAccountCreateArgs: model.ServiceAccountCreateArgs{},
+ APIKey: mldtest.APIKey,
+ Aud: mldtest.Aud,
+ UUID: mldtest.SAUUID,
+ ServiceAccountCreateParams: model.ServiceAccountCreateParams{},
},
},
BaseURL: jt.New(baseURL),
@@ -407,7 +407,7 @@ func newClient(ctx context.Context, t *testing.T) Client {
return c
}
-func validateLinkResults(t *testing.T, results model.LinkCreateResults) {
+func validateLinkResults(t *testing.T, results model.MagicLinkCreateResults) {
ml, err := url.Parse(results.MagicLink)
if err != nil {
t.Fatalf("Failed to parse magic link: %v.", err)
diff --git a/cmd/stress/go.mod b/cmd/stress/go.mod
index 4f90781..48cc877 100644
--- a/cmd/stress/go.mod
+++ b/cmd/stress/go.mod
@@ -1,27 +1,31 @@
module github.com/MicahParks/magiclinksdev/cmd/stress
-go 1.21.1
+go 1.22.0
+
+toolchain go1.23.2
require (
- github.com/MicahParks/magiclinksdev v0.4.3
- golang.org/x/sync v0.3.0
+ github.com/MicahParks/magiclinksdev v0.5.1
+ golang.org/x/sync v0.8.0
)
require (
- github.com/MicahParks/jsontype v0.5.0 // indirect
- github.com/MicahParks/jwkset v0.3.1 // indirect
- github.com/MicahParks/keyfunc v1.9.0 // indirect
+ github.com/MicahParks/jsontype v0.6.1 // indirect
+ github.com/MicahParks/jwkset v0.5.20 // indirect
+ github.com/MicahParks/keyfunc/v3 v3.3.5 // indirect
github.com/MicahParks/recaptcha v0.0.5 // indirect
- github.com/golang-jwt/jwt/v4 v4.5.0 // indirect
- github.com/google/uuid v1.3.1 // indirect
+ github.com/golang-jwt/jwt/v5 v5.2.1 // indirect
+ github.com/google/uuid v1.6.0 // indirect
github.com/jackc/pgpassfile v1.0.0 // indirect
- github.com/jackc/pgservicefile v0.0.0-20221227161230-091c0ba34f0a // indirect
- github.com/jackc/pgx/v5 v5.4.3 // indirect
- github.com/tidwall/gjson v1.16.0 // indirect
+ github.com/jackc/pgservicefile v0.0.0-20240606120523-5a60cdf6a761 // indirect
+ github.com/jackc/pgx/v5 v5.7.1 // indirect
+ github.com/jackc/puddle/v2 v2.2.2 // indirect
+ github.com/tidwall/gjson v1.18.0 // indirect
github.com/tidwall/match v1.1.1 // indirect
github.com/tidwall/pretty v1.2.1 // indirect
github.com/tidwall/sjson v1.2.5 // indirect
- golang.org/x/crypto v0.13.0 // indirect
- golang.org/x/text v0.13.0 // indirect
- golang.org/x/time v0.3.0 // indirect
+ golang.org/x/crypto v0.28.0 // indirect
+ golang.org/x/mod v0.21.0 // indirect
+ golang.org/x/text v0.19.0 // indirect
+ golang.org/x/time v0.7.0 // indirect
)
diff --git a/cmd/stress/go.sum b/cmd/stress/go.sum
index ec3ddd3..5a63d40 100644
--- a/cmd/stress/go.sum
+++ b/cmd/stress/go.sum
@@ -1,47 +1,46 @@
-github.com/MicahParks/jsontype v0.5.0 h1:O/7LAAbWEe3sPNvwaLINy6eEvgINQlJRNEShyUV5Jrc=
-github.com/MicahParks/jsontype v0.5.0/go.mod h1:PVeg4g8eHt4QDlhe56X1sWzRuHiVlCg4m0vgkpEso/Y=
-github.com/MicahParks/jwkset v0.3.1 h1:DIVazR/elD8CLWPblrVo610TzovIDYMcvlM4X0UT0vQ=
-github.com/MicahParks/jwkset v0.3.1/go.mod h1:Ob0sxSgMmQZFg4GO59PVBnfm+jtdQ1MJbfZDU90tEwM=
-github.com/MicahParks/keyfunc v1.9.0 h1:lhKd5xrFHLNOWrDc4Tyb/Q1AJ4LCzQ48GVJyVIID3+o=
-github.com/MicahParks/keyfunc v1.9.0/go.mod h1:IdnCilugA0O/99dW+/MkvlyrsX8+L8+x95xuVNtM5jw=
-github.com/MicahParks/magiclinksdev v0.4.3 h1:kSnPlAZwW8uzdiE/aC2AcPNs8zcFAklHlzLVlMIdSIo=
-github.com/MicahParks/magiclinksdev v0.4.3/go.mod h1:avz0c4ftuAk6GWtOkBe/yUgAb+MZmUuTF3xPpsC/XJQ=
+github.com/MicahParks/jsontype v0.6.1 h1:yFiDEOgSCDT+Es8k17PYZkvpqbZJ9GxJH2ioeVGvgt0=
+github.com/MicahParks/jsontype v0.6.1/go.mod h1:PVeg4g8eHt4QDlhe56X1sWzRuHiVlCg4m0vgkpEso/Y=
+github.com/MicahParks/jwkset v0.5.20 h1:gTIKx9AofTqQJ0srd8AL7ty9NeadP5WUXSPOZadTpOI=
+github.com/MicahParks/jwkset v0.5.20/go.mod h1:q8ptTGn/Z9c4MwbcfeCDssADeVQb3Pk7PnVxrvi+2QY=
+github.com/MicahParks/keyfunc/v3 v3.3.5 h1:7ceAJLUAldnoueHDNzF8Bx06oVcQ5CfJnYwNt1U3YYo=
+github.com/MicahParks/keyfunc/v3 v3.3.5/go.mod h1:SdCCyMJn/bYqWDvARspC6nCT8Sk74MjuAY22C7dCST8=
+github.com/MicahParks/magiclinksdev v0.5.1 h1:EB6h0YP7Qd31ycnr6yZqDjag3eUXKWjGQgkb/QMVOZ0=
+github.com/MicahParks/magiclinksdev v0.5.1/go.mod h1:jwoiNsLu1qMyLEj4hSLD3mMwGPMXmMoyBMTwfhsAV8c=
github.com/MicahParks/recaptcha v0.0.5 h1:RvKq7E1BZJtz5ubSkBun20jXxIsMWt2oZ0ppTJOzX1A=
github.com/MicahParks/recaptcha v0.0.5/go.mod h1:aFv3iZDDs6Pbi6tRpUm8gofaTUnDxOQ27x5KsK0CZwE=
-github.com/aws/aws-sdk-go v1.45.6 h1:Y2isQQBZsnO15dzUQo9YQRThtHgrV200XCH05BRHVJI=
-github.com/aws/aws-sdk-go v1.45.6/go.mod h1:aVsgQcEevwlmQ7qHE9I3h+dtQgpqhFB+i8Phjh7fkwI=
+github.com/aws/aws-sdk-go v1.55.5 h1:KKUZBfBoyqy5d3swXyiC7Q76ic40rYcbqH7qjh59kzU=
+github.com/aws/aws-sdk-go v1.55.5/go.mod h1:eRwEWoyTWFMVYVQzKMNHWP5/RV4xIUGMQfXQHfHkpNU=
github.com/davecgh/go-spew v1.1.0/go.mod h1:J7Y8YcW2NihsgmVo/mv3lAwl/skON4iLHjSsI+c5H38=
github.com/davecgh/go-spew v1.1.1 h1:vj9j/u1bqnvCEfJOwUhtlOARqs3+rkHYY13jYWTU97c=
github.com/davecgh/go-spew v1.1.1/go.mod h1:J7Y8YcW2NihsgmVo/mv3lAwl/skON4iLHjSsI+c5H38=
-github.com/golang-jwt/jwt/v4 v4.4.2/go.mod h1:m21LjoU+eqJr34lmDMbreY2eSTRJ1cv77w39/MY0Ch0=
-github.com/golang-jwt/jwt/v4 v4.5.0 h1:7cYmW1XlMY7h7ii7UhUyChSgS5wUJEnm9uZVTGqOWzg=
-github.com/golang-jwt/jwt/v4 v4.5.0/go.mod h1:m21LjoU+eqJr34lmDMbreY2eSTRJ1cv77w39/MY0Ch0=
-github.com/google/uuid v1.3.1 h1:KjJaJ9iWZ3jOFZIf1Lqf4laDRCasjl0BCmnEGxkdLb4=
-github.com/google/uuid v1.3.1/go.mod h1:TIyPZe4MgqvfeYDBFedMoGGpEw/LqOeaOT+nhxU+yHo=
+github.com/golang-jwt/jwt/v5 v5.2.1 h1:OuVbFODueb089Lh128TAcimifWaLhJwVflnrgM17wHk=
+github.com/golang-jwt/jwt/v5 v5.2.1/go.mod h1:pqrtFR0X4osieyHYxtmOUWsAWrfe1Q5UVIyoH402zdk=
+github.com/google/uuid v1.6.0 h1:NIvaJDMOsjHA8n1jAhLSgzrAzy1Hgr+hNrb57e+94F0=
+github.com/google/uuid v1.6.0/go.mod h1:TIyPZe4MgqvfeYDBFedMoGGpEw/LqOeaOT+nhxU+yHo=
github.com/jackc/pgpassfile v1.0.0 h1:/6Hmqy13Ss2zCq62VdNG8tM1wchn8zjSGOBJ6icpsIM=
github.com/jackc/pgpassfile v1.0.0/go.mod h1:CEx0iS5ambNFdcRtxPj5JhEz+xB6uRky5eyVu/W2HEg=
-github.com/jackc/pgservicefile v0.0.0-20221227161230-091c0ba34f0a h1:bbPeKD0xmW/Y25WS6cokEszi5g+S0QxI/d45PkRi7Nk=
-github.com/jackc/pgservicefile v0.0.0-20221227161230-091c0ba34f0a/go.mod h1:5TJZWKEWniPve33vlWYSoGYefn3gLQRzjfDlhSJ9ZKM=
-github.com/jackc/pgx/v5 v5.4.3 h1:cxFyXhxlvAifxnkKKdlxv8XqUf59tDlYjnV5YYfsJJY=
-github.com/jackc/pgx/v5 v5.4.3/go.mod h1:Ig06C2Vu0t5qXC60W8sqIthScaEnFvojjj9dSljmHRA=
-github.com/jackc/puddle/v2 v2.2.1 h1:RhxXJtFG022u4ibrCSMSiu5aOq1i77R3OHKNJj77OAk=
-github.com/jackc/puddle/v2 v2.2.1/go.mod h1:vriiEXHvEE654aYKXXjOvZM39qJ0q+azkZFrfEOc3H4=
+github.com/jackc/pgservicefile v0.0.0-20240606120523-5a60cdf6a761 h1:iCEnooe7UlwOQYpKFhBabPMi4aNAfoODPEFNiAnClxo=
+github.com/jackc/pgservicefile v0.0.0-20240606120523-5a60cdf6a761/go.mod h1:5TJZWKEWniPve33vlWYSoGYefn3gLQRzjfDlhSJ9ZKM=
+github.com/jackc/pgx/v5 v5.7.1 h1:x7SYsPBYDkHDksogeSmZZ5xzThcTgRz++I5E+ePFUcs=
+github.com/jackc/pgx/v5 v5.7.1/go.mod h1:e7O26IywZZ+naJtWWos6i6fvWK+29etgITqrqHLfoZA=
+github.com/jackc/puddle/v2 v2.2.2 h1:PR8nw+E/1w0GLuRFSmiioY6UooMp6KJv0/61nB7icHo=
+github.com/jackc/puddle/v2 v2.2.2/go.mod h1:vriiEXHvEE654aYKXXjOvZM39qJ0q+azkZFrfEOc3H4=
github.com/jmespath/go-jmespath v0.4.0 h1:BEgLn5cpjn8UN1mAw4NjwDrS35OdebyEtFe+9YPoQUg=
github.com/jmespath/go-jmespath v0.4.0/go.mod h1:T8mJZnbsbmF+m6zOOFylbeCJqk5+pHWvzYPziyZiYoo=
github.com/pmezard/go-difflib v1.0.0 h1:4DBwDE0NGyQoBHbLQYPwSUPoCMWR5BEzIk/f1lZbAQM=
github.com/pmezard/go-difflib v1.0.0/go.mod h1:iKH77koFhYxTK1pcRnkKkqfTogsbg7gZNVY4sRDYZ/4=
github.com/sendgrid/rest v2.6.9+incompatible h1:1EyIcsNdn9KIisLW50MKwmSRSK+ekueiEMJ7NEoxJo0=
github.com/sendgrid/rest v2.6.9+incompatible/go.mod h1:kXX7q3jZtJXK5c5qK83bSGMdV6tsOE70KbHoqJls4lE=
-github.com/sendgrid/sendgrid-go v3.13.0+incompatible h1:HZrzc06/QfBGesY9o3n1lvBrRONA+57rbDRKet7plos=
-github.com/sendgrid/sendgrid-go v3.13.0+incompatible/go.mod h1:QRQt+LX/NmgVEvmdRw0VT/QgUn499+iza2FnDca9fg8=
+github.com/sendgrid/sendgrid-go v3.16.0+incompatible h1:i8eE6IMkiCy7vusSdacHHSBUpXyTcTXy/Rl9N9aZ/Qw=
+github.com/sendgrid/sendgrid-go v3.16.0+incompatible/go.mod h1:QRQt+LX/NmgVEvmdRw0VT/QgUn499+iza2FnDca9fg8=
github.com/stretchr/objx v0.1.0/go.mod h1:HFkY916IF+rwdDfMAkV7OtwuqBVzrE8GR6GFx+wExME=
github.com/stretchr/testify v1.3.0/go.mod h1:M5WIy9Dh21IEIfnGCwXGc5bZfKNJtfHm1UVUgZn+9EI=
github.com/stretchr/testify v1.7.0/go.mod h1:6Fq8oRcR53rry900zMqJjRRixrwX3KX962/h/Wwjteg=
github.com/stretchr/testify v1.8.1 h1:w7B6lhMri9wdJUVmEZPGGhZzrYTPvgJArz7wNPgYKsk=
github.com/stretchr/testify v1.8.1/go.mod h1:w2LPCIKwWwSfY2zedu0+kehJoqGctiVI29o6fzry7u4=
github.com/tidwall/gjson v1.14.2/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
-github.com/tidwall/gjson v1.16.0 h1:SyXa+dsSPpUlcwEDuKuEBJEz5vzTvOea+9rjyYodQFg=
-github.com/tidwall/gjson v1.16.0/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
+github.com/tidwall/gjson v1.18.0 h1:FIDeeyB800efLX89e5a8Y0BNH+LOngJyGrIWxG2FKQY=
+github.com/tidwall/gjson v1.18.0/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
github.com/tidwall/match v1.1.1 h1:+Ho715JplO36QYgwN9PGYNhgZvoUSc9X2c80KVTi+GA=
github.com/tidwall/match v1.1.1/go.mod h1:eRSPERbgtNPcGhD8UCthc6PmLEQXEWd3PRB5JTxsfmM=
github.com/tidwall/pretty v1.2.0/go.mod h1:ITEVvHYasfjBbM0u2Pg8T2nJnzm8xPwvNhhsoaGGjNU=
@@ -49,16 +48,16 @@ github.com/tidwall/pretty v1.2.1 h1:qjsOFOWWQl+N3RsoF5/ssm1pHmJJwhjlSbZ51I6wMl4=
github.com/tidwall/pretty v1.2.1/go.mod h1:ITEVvHYasfjBbM0u2Pg8T2nJnzm8xPwvNhhsoaGGjNU=
github.com/tidwall/sjson v1.2.5 h1:kLy8mja+1c9jlljvWTlSazM7cKDRfJuR/bOJhcY5NcY=
github.com/tidwall/sjson v1.2.5/go.mod h1:Fvgq9kS/6ociJEDnK0Fk1cpYF4FIW6ZF7LAe+6jwd28=
-golang.org/x/crypto v0.13.0 h1:mvySKfSWJ+UKUii46M40LOvyWfN0s2U+46/jDd0e6Ck=
-golang.org/x/crypto v0.13.0/go.mod h1:y6Z2r+Rw4iayiXXAIxJIDAJ1zMW4yaTpebo8fPOliYc=
-golang.org/x/mod v0.12.0 h1:rmsUpXtvNzj340zd98LZ4KntptpfRHwpFOHG188oHXc=
-golang.org/x/mod v0.12.0/go.mod h1:iBbtSCu2XBx23ZKBPSOrRkjjQPZFPuis4dIYUhu/chs=
-golang.org/x/sync v0.3.0 h1:ftCYgMx6zT/asHUrPw8BLLscYtGznsLAnjq5RH9P66E=
-golang.org/x/sync v0.3.0/go.mod h1:FU7BRWz2tNW+3quACPkgCx/L+uEAv1htQ0V83Z9Rj+Y=
-golang.org/x/text v0.13.0 h1:ablQoSUd0tRdKxZewP80B+BaqeKJuVhuRxj/dkrun3k=
-golang.org/x/text v0.13.0/go.mod h1:TvPlkZtksWOMsz7fbANvkp4WM8x/WCo/om8BMLbz+aE=
-golang.org/x/time v0.3.0 h1:rg5rLMjNzMS1RkNLzCG38eapWhnYLFYXDXj2gOlr8j4=
-golang.org/x/time v0.3.0/go.mod h1:tRJNPiyCQ0inRvYxbN9jk5I+vvW/OXSQhTDSoE431IQ=
+golang.org/x/crypto v0.28.0 h1:GBDwsMXVQi34v5CCYUm2jkJvu4cbtru2U4TN2PSyQnw=
+golang.org/x/crypto v0.28.0/go.mod h1:rmgy+3RHxRZMyY0jjAJShp2zgEdOqj2AO7U0pYmeQ7U=
+golang.org/x/mod v0.21.0 h1:vvrHzRwRfVKSiLrG+d4FMl/Qi4ukBCE6kZlTUkDYRT0=
+golang.org/x/mod v0.21.0/go.mod h1:6SkKJ3Xj0I0BrPOZoBy3bdMptDDU9oJrpohJ3eWZ1fY=
+golang.org/x/sync v0.8.0 h1:3NFvSEYkUoMifnESzZl15y791HH1qU2xm6eCJU5ZPXQ=
+golang.org/x/sync v0.8.0/go.mod h1:Czt+wKu1gCyEFDUtn0jG5QVvpJ6rzVqr5aXyt9drQfk=
+golang.org/x/text v0.19.0 h1:kTxAhCbGbxhK0IwgSKiMO5awPoDQ0RpfiVYBfK860YM=
+golang.org/x/text v0.19.0/go.mod h1:BuEKDfySbSR4drPmRPG/7iBdf8hvFMuRexcpahXilzY=
+golang.org/x/time v0.7.0 h1:ntUhktv3OPE6TgYxXWv9vKvUSJyIFJlyohwbkEwPrKQ=
+golang.org/x/time v0.7.0/go.mod h1:3BpzKBy/shNhVucY/MWOyx10tF3SFh9QdLuxbVysPQM=
gopkg.in/check.v1 v0.0.0-20161208181325-20d25e280405/go.mod h1:Co6ibVJAznAaIkqp8huTwlJQCZ016jof/cbN4VW5Yz0=
gopkg.in/yaml.v3 v3.0.0-20200313102051-9f266ea9e77c/go.mod h1:K4uyk7z7BCEPqu6E+C64Yfv1cQ7kz7rIZviUmN+EgEM=
gopkg.in/yaml.v3 v3.0.1 h1:fxVm/GzAzEWqLHuvctI91KS9hhNmmWOoWu0XTYJS7CA=
diff --git a/cmd/stress/go.work b/cmd/stress/go.work
new file mode 100644
index 0000000..5fb1412
--- /dev/null
+++ b/cmd/stress/go.work
@@ -0,0 +1,6 @@
+go 1.23.2
+
+use (
+ .
+ ../..
+)
diff --git a/cmd/stress/go.work.sum b/cmd/stress/go.work.sum
new file mode 100644
index 0000000..3ea587c
--- /dev/null
+++ b/cmd/stress/go.work.sum
@@ -0,0 +1,56 @@
+github.com/creack/pty v1.1.9 h1:uDmaGzcdjhF4i/plgjmEsriH11Y0o7RKapEf/LDaM3w=
+github.com/creack/pty v1.1.9/go.mod h1:oKZEueFk5CKHvIhNR5MUki03XCEU+Q6VDXinZuGJ33E=
+github.com/google/go-cmp v0.6.0 h1:ofyhxvXcZhMsU5ulbFiLKl/XBFqE1GSq7atu8tAmTRI=
+github.com/google/go-cmp v0.6.0/go.mod h1:17dUlkBOakJ0+DkrSSNjCkIjxS6bF9zb3elmeNGIjoY=
+github.com/kr/pretty v0.1.0/go.mod h1:dAy3ld7l9f0ibDNOQOHHMYYIIbhfbHSm3C4ZsoJORNo=
+github.com/kr/pretty v0.2.1/go.mod h1:ipq/a2n7PKx3OHsz4KJII5eveXtPO4qwEXGdVfWzfnI=
+github.com/kr/pretty v0.3.0 h1:WgNl7dwNpEZ6jJ9k1snq4pZsg7DOEN8hP9Xw0Tsjwk0=
+github.com/kr/pretty v0.3.0/go.mod h1:640gp4NfQd8pI5XOwp5fnNeVWj67G7CFk/SaSQn7NBk=
+github.com/kr/pty v1.1.1 h1:VkoXIwSboBpnk99O/KFauAEILuNHv5DVFKZMBN/gUgw=
+github.com/kr/pty v1.1.1/go.mod h1:pFQYn66WHrOpPYNljwOMqo10TkYh1fy3cYio2l3bCsQ=
+github.com/kr/text v0.1.0/go.mod h1:4Jbv+DJW3UT/LiOwJeYQe1efqtUx/iVham/4vfdArNI=
+github.com/kr/text v0.2.0 h1:5Nx0Ya0ZqY2ygV366QzturHI13Jq95ApcVaJBhpS+AY=
+github.com/kr/text v0.2.0/go.mod h1:eLer722TekiGuMkidMxC/pM04lWEeraHUUmBw8l2grE=
+github.com/rogpeppe/go-internal v1.6.1 h1:/FiVV8dS/e+YqF2JvO3yXRFbBLTIuSDkuC7aBOAvL+k=
+github.com/rogpeppe/go-internal v1.6.1/go.mod h1:xXDCJY+GAPziupqXw64V24skbSoqbTEfhy4qGm1nDQc=
+github.com/stretchr/objx v0.1.0 h1:4G4v2dO3VZwixGIRoQ5Lfboy6nUhCyYzaqnIAPPhYs4=
+github.com/stretchr/objx v0.4.0/go.mod h1:YvHI0jy2hoMjB+UWwv71VJQ9isScKT/TqJzVSSt89Yw=
+github.com/stretchr/objx v0.5.0 h1:1zr/of2m5FGMsad5YfcqgdqdWrIhu+EBEJRhR1U7z/c=
+github.com/stretchr/objx v0.5.0/go.mod h1:Yh+to48EsGEfYuaHDzXPcE3xhTkx73EhmCGUpEOglKo=
+github.com/stretchr/testify v1.7.1/go.mod h1:6Fq8oRcR53rry900zMqJjRRixrwX3KX962/h/Wwjteg=
+github.com/stretchr/testify v1.8.0/go.mod h1:yNjHg4UonilssWZ8iaSj1OCr/vHnekPRkoO+kdMU+MU=
+github.com/yuin/goldmark v1.4.13 h1:fVcFKWvrslecOb/tg+Cc05dkeYx540o0FuFt3nUVDoE=
+github.com/yuin/goldmark v1.4.13/go.mod h1:6yULJ656Px+3vBD8DxQVa3kxgyrAnzto9xy5taEt/CY=
+golang.org/x/crypto v0.23.0/go.mod h1:CKFgDieR+mRhux2Lsu27y0fO304Db0wZe70UKqHu0v8=
+golang.org/x/crypto v0.27.0/go.mod h1:1Xngt8kV6Dvbssa53Ziq6Eqn0HqbZi5Z6R0ZpwQzt70=
+golang.org/x/mod v0.17.0/go.mod h1:hTbmBsO62+eylJbnUtE2MGJUyE7QWk4xUqPFrRgJ+7c=
+golang.org/x/net v0.10.0 h1:X2//UzNDwYmtCLn7To6G58Wr6f5ahEAQgKNzv9Y951M=
+golang.org/x/net v0.10.0/go.mod h1:0qNGK6F8kojg2nk9dLZ2mShWaEBan6FAoqfSigmmuDg=
+golang.org/x/net v0.25.0 h1:d/OCCoBEUq33pjydKrGQhw7IlUPI2Oylr+8qLx49kac=
+golang.org/x/net v0.25.0/go.mod h1:JkAGAh7GEvH74S6FOH42FLoXpXbE/aqXSrIQjXgsiwM=
+golang.org/x/sync v0.7.0/go.mod h1:Czt+wKu1gCyEFDUtn0jG5QVvpJ6rzVqr5aXyt9drQfk=
+golang.org/x/sys v0.12.0 h1:CM0HF96J0hcLAwsHPJZjfdNzs0gftsLfgKt57wWHJ0o=
+golang.org/x/sys v0.12.0/go.mod h1:oPkhp1MJrh7nUepCBck5+mAzfO9JrbApNNgaTdGDITg=
+golang.org/x/sys v0.20.0/go.mod h1:/VUhepiaJMQUp4+oa/7Zr1D23ma6VTLIYjOOTFZPUcA=
+golang.org/x/sys v0.26.0 h1:KHjCJyddX0LoSTb3J+vWpupP9p0oznkqVk/IfjymZbo=
+golang.org/x/sys v0.26.0/go.mod h1:/VUhepiaJMQUp4+oa/7Zr1D23ma6VTLIYjOOTFZPUcA=
+golang.org/x/telemetry v0.0.0-20240228155512-f48c80bd79b2 h1:IRJeR9r1pYWsHKTRe/IInb7lYvbBVIqOgsX/u0mbOWY=
+golang.org/x/telemetry v0.0.0-20240228155512-f48c80bd79b2/go.mod h1:TeRTkGYfJXctD9OcfyVLyj2J3IxLnKwHJR8f4D8a3YE=
+golang.org/x/term v0.12.0 h1:/ZfYdc3zq+q02Rv9vGqTeSItdzZTSNDmfTi0mBAuidU=
+golang.org/x/term v0.12.0/go.mod h1:owVbMEjm3cBLCHdkQu9b1opXd4ETQWc3BhuQGKgXgvU=
+golang.org/x/term v0.20.0/go.mod h1:8UkIAJTvZgivsXaD6/pH6U9ecQzZ45awqEOzuCvwpFY=
+golang.org/x/term v0.25.0 h1:WtHI/ltw4NvSUig5KARz9h521QvRC8RmF/cuYqifU24=
+golang.org/x/term v0.25.0/go.mod h1:RPyXicDX+6vLxogjjRxjgD2TKtmAO6NZBsBRfrOLu7M=
+golang.org/x/text v0.15.0/go.mod h1:18ZOQIKpY8NJVqYksKHtTdi31H5itFRjB5/qKTNYzSU=
+golang.org/x/text v0.18.0/go.mod h1:BuEKDfySbSR4drPmRPG/7iBdf8hvFMuRexcpahXilzY=
+golang.org/x/time v0.5.0/go.mod h1:3BpzKBy/shNhVucY/MWOyx10tF3SFh9QdLuxbVysPQM=
+golang.org/x/tools v0.6.0 h1:BOw41kyTf3PuCW1pVQf8+Cyg8pMlkYB1oo9iJ6D/lKM=
+golang.org/x/tools v0.6.0/go.mod h1:Xwgl3UAJ/d3gWutnCtw505GrjyAbvKui8lOU390QaIU=
+golang.org/x/tools v0.13.0/go.mod h1:HvlwmtVNQAhOuCjW7xxvovg8wbNq7LwfXh/k7wXUl58=
+golang.org/x/tools v0.21.1-0.20240508182429-e35e4ccd0d2d h1:vU5i/LfpvrRCpgM/VPfJLg5KjxD3E+hfT1SH+d9zLwg=
+golang.org/x/tools v0.21.1-0.20240508182429-e35e4ccd0d2d/go.mod h1:aiJjzUbINMkxbQROHiO6hDPo2LHcIPhhQsa9DLh0yGk=
+gopkg.in/check.v1 v1.0.0-20180628173108-788fd7840127/go.mod h1:Co6ibVJAznAaIkqp8huTwlJQCZ016jof/cbN4VW5Yz0=
+gopkg.in/check.v1 v1.0.0-20201130134442-10cb98267c6c h1:Hei/4ADfdWqJk1ZMxUNpqntNwaWcugrBjAiHlqqRiVk=
+gopkg.in/check.v1 v1.0.0-20201130134442-10cb98267c6c/go.mod h1:JHkPIbrfpd72SG/EVd6muEfDQjcINNoR0C8j2r3qZ4Q=
+gopkg.in/errgo.v2 v2.1.0 h1:0vLT13EuvQ0hNvakwLuFZ/jYrLp5F3kcWHXdRggjCE8=
+gopkg.in/errgo.v2 v2.1.0/go.mod h1:hNsd1EY+bozCKY1Ytp96fpM3vjJbqLJn88ws8XvfDNI=
diff --git a/cmd/stress/link.example.json b/cmd/stress/link.example.json
index 1395e88..1284f2c 100644
--- a/cmd/stress/link.example.json
+++ b/cmd/stress/link.example.json
@@ -1,13 +1,13 @@
{
- "linkArgs": {
- "jwtCreateArgs": {
- "jwtClaims": {
+ "magicLinkCreateParams": {
+ "jwtCreateParams": {
+ "claims": {
"foo": "bar"
},
- "jwtLifespanSeconds": 0
+ "lifespanSeconds": 0
},
- "linkLifespan": 0,
+ "lifespanSeconds": 0,
"redirectQueryKey": "",
- "redirectUrl": "https://jwtdebug.micahparks.com"
+ "redirectURL": "https://jwtdebug.micahparks.com"
}
}
diff --git a/cmd/stress/main.go b/cmd/stress/main.go
index fe902b5..308a028 100644
--- a/cmd/stress/main.go
+++ b/cmd/stress/main.go
@@ -11,15 +11,16 @@ import (
"strings"
"time"
- "github.com/MicahParks/magiclinksdev/mldtest"
"golang.org/x/sync/errgroup"
+ "github.com/MicahParks/magiclinksdev/mldtest"
+
mld "github.com/MicahParks/magiclinksdev"
"github.com/MicahParks/magiclinksdev/network"
"github.com/MicahParks/magiclinksdev/network/middleware"
)
-//go:embed link.prod.json
+//go:embed link.example.json
var linkJSON []byte
func main() {
@@ -35,7 +36,7 @@ func main() {
)
exit(ctx, l, time.Now(), 1)
}
- u, err = u.Parse("/api/v1/" + network.PathLinkCreate)
+ u, err = u.Parse("/api/v2/" + network.PathMagicLinkCreate)
if err != nil {
l.ErrorContext(ctx, "Failed to parse URL.",
mld.LogErr, err,
diff --git a/compose.yaml b/compose.yaml
index 2ca0caf..f14f6cd 100644
--- a/compose.yaml
+++ b/compose.yaml
@@ -1,4 +1,3 @@
-version: "3.8"
services:
magiclinksdev:
image: "micahparks/magiclinksdevnop"
diff --git a/config.quickstart.json b/config.quickstart.json
index 193f20d..bd813db 100644
--- a/config.quickstart.json
+++ b/config.quickstart.json
@@ -1,14 +1,14 @@
{
"server": {
- "adminConfig": [
+ "adminCreateParams": [
{
"apiKey": "40084740-0bc3-455d-b298-e23a31561580",
"aud": "ad9e9d84-92ea-4f07-bac9-5d898d59c83b",
"uuid": "1e079d6d-a8b9-4065-aa8d-86906accd211",
- "serviceAccountCreateArgs": {}
+ "serviceAccountCreateParams": {}
}
],
- "baseURL": "http://localhost:8080/api/v1/",
+ "baseURL": "http://localhost:8080/api/v2/",
"iss": "http://localhost:8080"
},
"storage": {
diff --git a/config.test.json b/config.test.json
index 407a213..c241f92 100644
--- a/config.test.json
+++ b/config.test.json
@@ -9,15 +9,15 @@
"refillRate": 0
},
"server": {
- "adminConfig": [
+ "adminCreateParams": [
{
"apiKey": "40084740-0bc3-455d-b298-e23a31561580",
"aud": "ad9e9d84-92ea-4f07-bac9-5d898d59c83b",
"uuid": "1e079d6d-a8b9-4065-aa8d-86906accd211",
- "serviceAccountCreateArgs": {}
+ "serviceAccountCreateParams": {}
}
],
- "baseURL": "http://localtest/api/v1/",
+ "baseURL": "http://localtest/api/v2/",
"iss": "testIssuer",
"jwks": {
"ignoreDefault": false
diff --git a/config/config.go b/config/config.go
index 85249c1..9f5049b 100644
--- a/config/config.go
+++ b/config/config.go
@@ -24,7 +24,7 @@ type LogLevel string
// Config is the configuration for the magiclinksdev server.
type Config struct {
- AdminConfig []model.AdminCreateArgs `json:"adminConfig"`
+ AdminCreateParams []model.AdminCreateParams `json:"adminCreateParams"`
BaseURL *jt.JSONType[*url.URL] `json:"baseURL"`
Iss string `json:"iss"`
JWKS JWKS `json:"jwks"`
diff --git a/constants.go b/constants.go
index c2e4d49..0902b6a 100644
--- a/constants.go
+++ b/constants.go
@@ -1,8 +1,15 @@
package magiclinksdev
+import (
+ "errors"
+ "time"
+)
+
const (
// ContentTypeJSON is the content type for JSON.
ContentTypeJSON = "application/json"
+ // DefaultOTPLength is the default length for OTPs.
+ DefaultOTPLength = 6
// DefaultRelativePathRedirect is the default relative path for redirecting.
DefaultRelativePathRedirect = "redirect"
// HeaderContentType is the content type header.
@@ -15,6 +22,8 @@ const (
LogRequestBody = "requestBody"
// LogResponseBody is key for logging the response body.
LogResponseBody = "responseBody"
+ // Over250Years is the maximum duration for this project. Restriction derived from Golang's time.Duration.
+ Over250Years = 250 * 366 * 24 * time.Hour
// ResponseInternalServerError is the response for internal server errors.
ResponseInternalServerError = "Internal server error."
// ResponseTooManyRequests is the response for too many requests.
@@ -23,6 +32,10 @@ const (
ResponseUnauthorized = "Unauthorized."
)
+var (
+ ErrParams = errors.New("invalid parameters")
+)
+
func Ptr[T any](v T) *T {
return &v
}
diff --git a/email/html.gohtml b/email/html.gohtml
deleted file mode 100644
index 5cce72b..0000000
--- a/email/html.gohtml
+++ /dev/null
@@ -1,166 +0,0 @@
-{{- /*gotype: github.com/MicahParks/magiclinksdev/email.TemplateData*/ -}}
-
-
-
-
-
-
-
-
-
- {{.Meta.MSOHead}}
-
## Self-hosting the service
-The **magiclinksdev** project can be self-hosted. Check out the [**Quickstart**](https://docs.magiclinks.dev/quickstart)
-page to get started in minutes. For reference on configuring your self-hosted instance, check out the
-[**Configuration**](https://docs.magiclinks.dev/configuration).
+The **magiclinksdev** project is open-source and can be self-hosted. Check out the [**Quickstart**](https://docs.magiclinks.dev/self-host-quickstart) page
+to get started in minutes. For reference on configuring your self-hosted instance, check out the
+[**Configuration**](https://docs.magiclinks.dev/self-host-configuration).
## Source code and license
The **magiclinksdev** project is [open source on GitHub](https://github.com/MicahParks/magiclinksdev) and licensed
-under [Apache License 2.0](https://github.com/MicahParks/magiclinksdev/blob/master/LICENSE).
+under [**Apache License 2.0**](https://github.com/MicahParks/magiclinksdev/blob/master/LICENSE).
## Optional SaaS platform
diff --git a/buildDocker.sh b/buildDocker.sh
index 18c498f..95a4769 100644
--- a/buildDocker.sh
+++ b/buildDocker.sh
@@ -7,16 +7,16 @@ if [ "$1" = "push" ]; then
then
exit 1
fi
- docker build --pull --push --file nop.Dockerfile --tag micahparks/magiclinksdevmulti .
+ docker build --pull --push --file multi.Dockerfile --tag micahparks/magiclinksdevmulti .
docker build --pull --push --file nop.Dockerfile --tag micahparks/magiclinksdevnop .
docker build --pull --push --file ses.Dockerfile --tag micahparks/magiclinksdevses .
docker build --pull --push --file sendgrid.Dockerfile --tag micahparks/magiclinksdevsendgrid .
- docker build --pull --push --file nop.Dockerfile --tag "micahparks/magiclinksdevmulti:$TAG" .
+ docker build --pull --push --file multi.Dockerfile --tag "micahparks/magiclinksdevmulti:$TAG" .
docker build --pull --push --file nop.Dockerfile --tag "micahparks/magiclinksdevnop:$TAG" .
docker build --pull --push --file ses.Dockerfile --tag "micahparks/magiclinksdevses:$TAG" .
docker build --pull --push --file sendgrid.Dockerfile --tag "micahparks/magiclinksdevsendgrid:$TAG" .
else
- docker build --pull --file nop.Dockerfile --tag micahparks/magiclinksdevmulti .
+ docker build --pull --file multi.Dockerfile --tag micahparks/magiclinksdevmulti .
docker build --pull --file nop.Dockerfile --tag micahparks/magiclinksdevnop .
docker build --pull --file ses.Dockerfile --tag micahparks/magiclinksdevses .
docker build --pull --file sendgrid.Dockerfile --tag micahparks/magiclinksdevsendgrid .
diff --git a/client/client.go b/client/client.go
index ec84d23..dc76e6c 100644
--- a/client/client.go
+++ b/client/client.go
@@ -22,8 +22,8 @@ import (
)
const (
- // SaaSBaseURL is the base URL for the SaaS offering. The SaaS offering is optional and the magiclinksdev project
- // can be self-hosted.
+ // SaaSBaseURL is the base URL for the SaaS platform. The SaaS platform is optional and the magiclinksdev project
+ // is open-source and can be self-hosted.
SaaSBaseURL = "https://magiclinks.dev"
// SaaSIss is the iss claim for JWTs in the SaaS offering.
SaaSIss = SaaSBaseURL
@@ -43,7 +43,7 @@ type Options struct {
HTTP *http.Client
}
-// Client is a client for the magiclinksdev project.
+// Client is the official Golang API client for the magiclinksdev project.
type Client struct {
apiKey uuid.UUID
aud uuid.UUID
@@ -54,9 +54,9 @@ type Client struct {
}
// New creates a new magiclinksdev client. The apiKey and aud are tied to the service account being used. The baseURL is
-// the HTTP(S) location of the magiclinksdev deployment. Only use HTTPS in production. For the SaaS offering, use the
+// the HTTP(S) location of the magiclinksdev deployment. Only use HTTPS in production. For the SaaS platform, use the
// SaaSBaseURL constant. The iss is the issuer of the JWTs, which is in the configuration of the magiclinksdev
-// deployment. For the SaaS offering, use the SaaSIss constant. Providing an empty string for the iss will disable
+// deployment. For the SaaS platform, use the SaaSIss constant. Providing an empty string for the iss will disable
// issuer validation.
func New(apiKey, aud uuid.UUID, baseURL, iss string, options Options) (Client, error) {
u, err := url.Parse(baseURL)
@@ -96,8 +96,8 @@ func New(apiKey, aud uuid.UUID, baseURL, iss string, options Options) (Client, e
}
// LocalJWTValidate validates a JWT locally. If the claims argument is not nil, its value will be passed directly to
-// jwt.ParseWithClaims. The claims should be unmarshalled into the provided non-nil pointer after the function call. See
-// the documentation for jwt.ParseWithClaims for more information. Registered JWT claims will be validated regardless if
+// jwt.ParseWithClaims. The claims should be unmarshalled into the claims argument if it is a non-nil pointer. See the
+// documentation for jwt.ParseWithClaims for more information. Registered JWT claims will be validated regardless if
// claims are specified or not.
func (c Client) LocalJWTValidate(token string, claims jwt.Claims) (*jwt.Token, error) {
if c.keyf == nil {
@@ -136,15 +136,6 @@ func (c Client) LocalJWTValidate(token string, claims jwt.Claims) (*jwt.Token, e
return t, nil
}
-// EmailLinkCreate calls the /email-link/create endpoint and returns the appropriate response.
-func (c Client) EmailLinkCreate(ctx context.Context, req model.EmailLinkCreateRequest) (model.EmailLinkCreateResponse, model.Error, error) {
- resp, errResp, err := request[model.EmailLinkCreateRequest, model.EmailLinkCreateResponse](ctx, c, http.StatusCreated, network.PathEmailLinkCreate, req)
- if err != nil {
- return model.EmailLinkCreateResponse{}, errResp, fmt.Errorf("failed to create email link: %w", err)
- }
- return resp, errResp, nil
-}
-
// JWTCreate calls the /jwt/create endpoint and returns the appropriate response.
func (c Client) JWTCreate(ctx context.Context, req model.JWTCreateRequest) (model.JWTCreateResponse, model.Error, error) {
resp, errResp, err := request[model.JWTCreateRequest, model.JWTCreateResponse](ctx, c, http.StatusCreated, network.PathJWTCreate, req)
@@ -165,16 +156,52 @@ func (c Client) JWTValidate(ctx context.Context, req model.JWTValidateRequest) (
return resp, errResp, nil
}
-// LinkCreate calls the /link/create endpoint and returns the appropriate response.
-func (c Client) LinkCreate(ctx context.Context, req model.LinkCreateRequest) (model.LinkCreateResponse, model.Error, error) {
- resp, errResp, err := request[model.LinkCreateRequest, model.LinkCreateResponse](ctx, c, http.StatusCreated, network.PathLinkCreate, req)
+// MagicLinkCreate calls the /magic-link/create endpoint and returns the appropriate response.
+func (c Client) MagicLinkCreate(ctx context.Context, req model.MagicLinkCreateRequest) (model.MagicLinkCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.MagicLinkCreateRequest, model.MagicLinkCreateResponse](ctx, c, http.StatusCreated, network.PathMagicLinkCreate, req)
+ if err != nil {
+ return model.MagicLinkCreateResponse{}, errResp, fmt.Errorf("failed to create link: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// MagicLinkEmailCreate calls the /magic-link-email/create endpoint and returns the appropriate response.
+func (c Client) MagicLinkEmailCreate(ctx context.Context, req model.MagicLinkEmailCreateRequest) (model.MagicLinkEmailCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.MagicLinkEmailCreateRequest, model.MagicLinkEmailCreateResponse](ctx, c, http.StatusCreated, network.PathMagicLinkEmailCreate, req)
+ if err != nil {
+ return model.MagicLinkEmailCreateResponse{}, errResp, fmt.Errorf("failed to create email link: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// OTPCreate calls the /otp/create endpoint and returns the appropriate response.
+func (c Client) OTPCreate(ctx context.Context, req model.OTPCreateRequest) (model.OTPCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.OTPCreateRequest, model.OTPCreateResponse](ctx, c, http.StatusCreated, network.PathOTPCreate, req)
+ if err != nil {
+ return model.OTPCreateResponse{}, errResp, fmt.Errorf("failed to create OTP: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// OTPValidate calls the /otp/validate endpoint and returns the appropriate response.
+func (c Client) OTPValidate(ctx context.Context, req model.OTPValidateRequest) (model.OTPValidateResponse, model.Error, error) {
+ resp, errResp, err := request[model.OTPValidateRequest, model.OTPValidateResponse](ctx, c, http.StatusOK, network.PathOTPValidate, req)
+ if err != nil {
+ return model.OTPValidateResponse{}, errResp, fmt.Errorf("failed to validate OTP: %w", err)
+ }
+ return resp, errResp, nil
+}
+
+// OTPEmailCreate calls the /otp-email/create endpoint and returns the appropriate response.
+func (c Client) OTPEmailCreate(ctx context.Context, req model.OTPEmailCreateRequest) (model.OTPEmailCreateResponse, model.Error, error) {
+ resp, errResp, err := request[model.OTPEmailCreateRequest, model.OTPEmailCreateResponse](ctx, c, http.StatusCreated, network.PathOTPEmailCreate, req)
if err != nil {
- return model.LinkCreateResponse{}, errResp, fmt.Errorf("failed to create link: %w", err)
+ return model.OTPEmailCreateResponse{}, errResp, fmt.Errorf("failed to create email OTP: %w", err)
}
return resp, errResp, nil
}
-// Ready calls the /ready endpoint. An error is returned if the service is not ready.
+// Ready calls the /ready endpoint. An error is returned if the service is not ready to accept requests.
func (c Client) Ready(ctx context.Context) error {
u, err := c.baseURL.Parse(network.PathReady)
if err != nil {
diff --git a/client/client_test.go b/client/client_test.go
index cea7c0e..4bfdf07 100644
--- a/client/client_test.go
+++ b/client/client_test.go
@@ -39,13 +39,13 @@ var (
_, attackerKey, _ = ed25519.GenerateKey(nil)
redirectPath, _ = url.Parse(mld.DefaultRelativePathRedirect)
- jwtCreateArgs = model.JWTCreateArgs{
- JWTClaims: mldtest.TClaims,
- JWTLifespanSeconds: 5,
+ jwtCreateParams = model.JWTCreateParams{
+ Claims: mldtest.TClaims,
+ LifespanSeconds: 5,
}
- linkArgs = model.LinkCreateArgs{
- JWTCreateArgs: jwtCreateArgs,
- LinkLifespan: 5,
+ linkParams = model.MagicLinkCreateParams{
+ JWTCreateParams: jwtCreateParams,
+ LifespanSeconds: 5,
RedirectQueryKey: magiclink.DefaultRedirectQueryKey,
RedirectURL: "http://example.com",
}
@@ -102,8 +102,8 @@ func TestEmailLinkCreate(t *testing.T) {
ctx := createCtx(t)
c := newClient(ctx, t)
- req := model.EmailLinkCreateRequest{
- EmailArgs: model.EmailLinkCreateArgs{
+ req := model.MagicLinkEmailCreateRequest{
+ MagicLinkEmailCreateParams: model.MagicLinkEmailCreateParams{
ButtonText: "Test button text",
Greeting: "Test greeting",
LogoClickURL: mldtest.LogoClickURL,
@@ -115,9 +115,9 @@ func TestEmailLinkCreate(t *testing.T) {
ToEmail: "customer@example.com",
ToName: "Test name",
},
- LinkArgs: linkArgs,
+ MagicLinkCreateParams: linkParams,
}
- resp, mldErr, err := c.EmailLinkCreate(ctx, req)
+ resp, mldErr, err := c.MagicLinkEmailCreate(ctx, req)
if err != nil {
t.Fatalf("Failed to create email link: %v.", err)
}
@@ -126,7 +126,7 @@ func TestEmailLinkCreate(t *testing.T) {
}
validateMetadata(t, resp.RequestMetadata)
- validateLinkResults(t, resp.EmailLinkCreateResults.LinkCreateResults)
+ validateLinkResults(t, resp.MagicLinkEmailCreateResults.MagicLinkCreateResults)
}
func TestJWTCreate(t *testing.T) {
@@ -179,7 +179,7 @@ func TestJWTValidate(t *testing.T) {
raw := jwtCreateHelper(ctx, t, c)
req := model.JWTValidateRequest{
- JWTValidateArgs: model.JWTValidateArgs{
+ JWTValidateParams: model.JWTValidateParams{
JWT: raw,
},
}
@@ -217,7 +217,7 @@ func TestJWTValidateForged(t *testing.T) {
}
req := model.JWTValidateRequest{
- JWTValidateArgs: model.JWTValidateArgs{
+ JWTValidateParams: model.JWTValidateParams{
JWT: raw,
},
}
@@ -237,10 +237,10 @@ func TestLinkCreate(t *testing.T) {
ctx := createCtx(t)
c := newClient(ctx, t)
- req := model.LinkCreateRequest{
- LinkArgs: linkArgs,
+ req := model.MagicLinkCreateRequest{
+ MagicLinkCreateParams: linkParams,
}
- resp, mldErr, err := c.LinkCreate(ctx, req)
+ resp, mldErr, err := c.MagicLinkCreate(ctx, req)
if err != nil {
t.Fatalf("Failed to create magic link: %v.", err)
}
@@ -249,7 +249,7 @@ func TestLinkCreate(t *testing.T) {
}
validateMetadata(t, resp.RequestMetadata)
- validateLinkResults(t, resp.LinkCreateResults)
+ validateLinkResults(t, resp.MagicLinkCreateResults)
}
func TestServiceAccountCreate(t *testing.T) {
@@ -257,7 +257,7 @@ func TestServiceAccountCreate(t *testing.T) {
c := newClient(ctx, t)
req := model.ServiceAccountCreateRequest{
- CreateServiceAccountArgs: model.ServiceAccountCreateArgs{},
+ ServiceAccountCreateParams: model.ServiceAccountCreateParams{},
}
resp, mldErr, err := c.ServiceAccountCreate(ctx, req)
if err != nil {
@@ -269,16 +269,16 @@ func TestServiceAccountCreate(t *testing.T) {
validateMetadata(t, resp.RequestMetadata)
- if resp.CreateServiceAccountResults.ServiceAccount.Admin {
+ if resp.ServiceAccountCreateResults.ServiceAccount.Admin {
t.Fatalf("Created service account should not be an admin.")
}
- if resp.CreateServiceAccountResults.ServiceAccount.UUID == uuid.Nil {
+ if resp.ServiceAccountCreateResults.ServiceAccount.UUID == uuid.Nil {
t.Fatalf("Created service account should have non-nil UUID.")
}
- if resp.CreateServiceAccountResults.ServiceAccount.Aud == uuid.Nil {
+ if resp.ServiceAccountCreateResults.ServiceAccount.Aud == uuid.Nil {
t.Fatalf("Created service account should have non-nil audience UUID.")
}
- if resp.CreateServiceAccountResults.ServiceAccount.APIKey == uuid.Nil {
+ if resp.ServiceAccountCreateResults.ServiceAccount.APIKey == uuid.Nil {
t.Fatalf("Created service account should have non-nil API key.")
}
}
@@ -291,7 +291,7 @@ func createCtx(t *testing.T) context.Context {
func jwtCreateHelper(ctx context.Context, t *testing.T, c Client) string {
req := model.JWTCreateRequest{
- JWTCreateArgs: jwtCreateArgs,
+ JWTCreateParams: jwtCreateParams,
}
resp, mldErr, err := c.JWTCreate(ctx, req)
if err != nil {
@@ -324,12 +324,12 @@ func jwtCreateHelper(ctx context.Context, t *testing.T, c Client) string {
func newClient(ctx context.Context, t *testing.T) Client {
conf := config.Config{
- AdminConfig: []model.AdminCreateArgs{
+ AdminCreateParams: []model.AdminCreateParams{
{
- APIKey: mldtest.APIKey,
- Aud: mldtest.Aud,
- UUID: mldtest.SAUUID,
- ServiceAccountCreateArgs: model.ServiceAccountCreateArgs{},
+ APIKey: mldtest.APIKey,
+ Aud: mldtest.Aud,
+ UUID: mldtest.SAUUID,
+ ServiceAccountCreateParams: model.ServiceAccountCreateParams{},
},
},
BaseURL: jt.New(baseURL),
@@ -407,7 +407,7 @@ func newClient(ctx context.Context, t *testing.T) Client {
return c
}
-func validateLinkResults(t *testing.T, results model.LinkCreateResults) {
+func validateLinkResults(t *testing.T, results model.MagicLinkCreateResults) {
ml, err := url.Parse(results.MagicLink)
if err != nil {
t.Fatalf("Failed to parse magic link: %v.", err)
diff --git a/cmd/stress/go.mod b/cmd/stress/go.mod
index 4f90781..48cc877 100644
--- a/cmd/stress/go.mod
+++ b/cmd/stress/go.mod
@@ -1,27 +1,31 @@
module github.com/MicahParks/magiclinksdev/cmd/stress
-go 1.21.1
+go 1.22.0
+
+toolchain go1.23.2
require (
- github.com/MicahParks/magiclinksdev v0.4.3
- golang.org/x/sync v0.3.0
+ github.com/MicahParks/magiclinksdev v0.5.1
+ golang.org/x/sync v0.8.0
)
require (
- github.com/MicahParks/jsontype v0.5.0 // indirect
- github.com/MicahParks/jwkset v0.3.1 // indirect
- github.com/MicahParks/keyfunc v1.9.0 // indirect
+ github.com/MicahParks/jsontype v0.6.1 // indirect
+ github.com/MicahParks/jwkset v0.5.20 // indirect
+ github.com/MicahParks/keyfunc/v3 v3.3.5 // indirect
github.com/MicahParks/recaptcha v0.0.5 // indirect
- github.com/golang-jwt/jwt/v4 v4.5.0 // indirect
- github.com/google/uuid v1.3.1 // indirect
+ github.com/golang-jwt/jwt/v5 v5.2.1 // indirect
+ github.com/google/uuid v1.6.0 // indirect
github.com/jackc/pgpassfile v1.0.0 // indirect
- github.com/jackc/pgservicefile v0.0.0-20221227161230-091c0ba34f0a // indirect
- github.com/jackc/pgx/v5 v5.4.3 // indirect
- github.com/tidwall/gjson v1.16.0 // indirect
+ github.com/jackc/pgservicefile v0.0.0-20240606120523-5a60cdf6a761 // indirect
+ github.com/jackc/pgx/v5 v5.7.1 // indirect
+ github.com/jackc/puddle/v2 v2.2.2 // indirect
+ github.com/tidwall/gjson v1.18.0 // indirect
github.com/tidwall/match v1.1.1 // indirect
github.com/tidwall/pretty v1.2.1 // indirect
github.com/tidwall/sjson v1.2.5 // indirect
- golang.org/x/crypto v0.13.0 // indirect
- golang.org/x/text v0.13.0 // indirect
- golang.org/x/time v0.3.0 // indirect
+ golang.org/x/crypto v0.28.0 // indirect
+ golang.org/x/mod v0.21.0 // indirect
+ golang.org/x/text v0.19.0 // indirect
+ golang.org/x/time v0.7.0 // indirect
)
diff --git a/cmd/stress/go.sum b/cmd/stress/go.sum
index ec3ddd3..5a63d40 100644
--- a/cmd/stress/go.sum
+++ b/cmd/stress/go.sum
@@ -1,47 +1,46 @@
-github.com/MicahParks/jsontype v0.5.0 h1:O/7LAAbWEe3sPNvwaLINy6eEvgINQlJRNEShyUV5Jrc=
-github.com/MicahParks/jsontype v0.5.0/go.mod h1:PVeg4g8eHt4QDlhe56X1sWzRuHiVlCg4m0vgkpEso/Y=
-github.com/MicahParks/jwkset v0.3.1 h1:DIVazR/elD8CLWPblrVo610TzovIDYMcvlM4X0UT0vQ=
-github.com/MicahParks/jwkset v0.3.1/go.mod h1:Ob0sxSgMmQZFg4GO59PVBnfm+jtdQ1MJbfZDU90tEwM=
-github.com/MicahParks/keyfunc v1.9.0 h1:lhKd5xrFHLNOWrDc4Tyb/Q1AJ4LCzQ48GVJyVIID3+o=
-github.com/MicahParks/keyfunc v1.9.0/go.mod h1:IdnCilugA0O/99dW+/MkvlyrsX8+L8+x95xuVNtM5jw=
-github.com/MicahParks/magiclinksdev v0.4.3 h1:kSnPlAZwW8uzdiE/aC2AcPNs8zcFAklHlzLVlMIdSIo=
-github.com/MicahParks/magiclinksdev v0.4.3/go.mod h1:avz0c4ftuAk6GWtOkBe/yUgAb+MZmUuTF3xPpsC/XJQ=
+github.com/MicahParks/jsontype v0.6.1 h1:yFiDEOgSCDT+Es8k17PYZkvpqbZJ9GxJH2ioeVGvgt0=
+github.com/MicahParks/jsontype v0.6.1/go.mod h1:PVeg4g8eHt4QDlhe56X1sWzRuHiVlCg4m0vgkpEso/Y=
+github.com/MicahParks/jwkset v0.5.20 h1:gTIKx9AofTqQJ0srd8AL7ty9NeadP5WUXSPOZadTpOI=
+github.com/MicahParks/jwkset v0.5.20/go.mod h1:q8ptTGn/Z9c4MwbcfeCDssADeVQb3Pk7PnVxrvi+2QY=
+github.com/MicahParks/keyfunc/v3 v3.3.5 h1:7ceAJLUAldnoueHDNzF8Bx06oVcQ5CfJnYwNt1U3YYo=
+github.com/MicahParks/keyfunc/v3 v3.3.5/go.mod h1:SdCCyMJn/bYqWDvARspC6nCT8Sk74MjuAY22C7dCST8=
+github.com/MicahParks/magiclinksdev v0.5.1 h1:EB6h0YP7Qd31ycnr6yZqDjag3eUXKWjGQgkb/QMVOZ0=
+github.com/MicahParks/magiclinksdev v0.5.1/go.mod h1:jwoiNsLu1qMyLEj4hSLD3mMwGPMXmMoyBMTwfhsAV8c=
github.com/MicahParks/recaptcha v0.0.5 h1:RvKq7E1BZJtz5ubSkBun20jXxIsMWt2oZ0ppTJOzX1A=
github.com/MicahParks/recaptcha v0.0.5/go.mod h1:aFv3iZDDs6Pbi6tRpUm8gofaTUnDxOQ27x5KsK0CZwE=
-github.com/aws/aws-sdk-go v1.45.6 h1:Y2isQQBZsnO15dzUQo9YQRThtHgrV200XCH05BRHVJI=
-github.com/aws/aws-sdk-go v1.45.6/go.mod h1:aVsgQcEevwlmQ7qHE9I3h+dtQgpqhFB+i8Phjh7fkwI=
+github.com/aws/aws-sdk-go v1.55.5 h1:KKUZBfBoyqy5d3swXyiC7Q76ic40rYcbqH7qjh59kzU=
+github.com/aws/aws-sdk-go v1.55.5/go.mod h1:eRwEWoyTWFMVYVQzKMNHWP5/RV4xIUGMQfXQHfHkpNU=
github.com/davecgh/go-spew v1.1.0/go.mod h1:J7Y8YcW2NihsgmVo/mv3lAwl/skON4iLHjSsI+c5H38=
github.com/davecgh/go-spew v1.1.1 h1:vj9j/u1bqnvCEfJOwUhtlOARqs3+rkHYY13jYWTU97c=
github.com/davecgh/go-spew v1.1.1/go.mod h1:J7Y8YcW2NihsgmVo/mv3lAwl/skON4iLHjSsI+c5H38=
-github.com/golang-jwt/jwt/v4 v4.4.2/go.mod h1:m21LjoU+eqJr34lmDMbreY2eSTRJ1cv77w39/MY0Ch0=
-github.com/golang-jwt/jwt/v4 v4.5.0 h1:7cYmW1XlMY7h7ii7UhUyChSgS5wUJEnm9uZVTGqOWzg=
-github.com/golang-jwt/jwt/v4 v4.5.0/go.mod h1:m21LjoU+eqJr34lmDMbreY2eSTRJ1cv77w39/MY0Ch0=
-github.com/google/uuid v1.3.1 h1:KjJaJ9iWZ3jOFZIf1Lqf4laDRCasjl0BCmnEGxkdLb4=
-github.com/google/uuid v1.3.1/go.mod h1:TIyPZe4MgqvfeYDBFedMoGGpEw/LqOeaOT+nhxU+yHo=
+github.com/golang-jwt/jwt/v5 v5.2.1 h1:OuVbFODueb089Lh128TAcimifWaLhJwVflnrgM17wHk=
+github.com/golang-jwt/jwt/v5 v5.2.1/go.mod h1:pqrtFR0X4osieyHYxtmOUWsAWrfe1Q5UVIyoH402zdk=
+github.com/google/uuid v1.6.0 h1:NIvaJDMOsjHA8n1jAhLSgzrAzy1Hgr+hNrb57e+94F0=
+github.com/google/uuid v1.6.0/go.mod h1:TIyPZe4MgqvfeYDBFedMoGGpEw/LqOeaOT+nhxU+yHo=
github.com/jackc/pgpassfile v1.0.0 h1:/6Hmqy13Ss2zCq62VdNG8tM1wchn8zjSGOBJ6icpsIM=
github.com/jackc/pgpassfile v1.0.0/go.mod h1:CEx0iS5ambNFdcRtxPj5JhEz+xB6uRky5eyVu/W2HEg=
-github.com/jackc/pgservicefile v0.0.0-20221227161230-091c0ba34f0a h1:bbPeKD0xmW/Y25WS6cokEszi5g+S0QxI/d45PkRi7Nk=
-github.com/jackc/pgservicefile v0.0.0-20221227161230-091c0ba34f0a/go.mod h1:5TJZWKEWniPve33vlWYSoGYefn3gLQRzjfDlhSJ9ZKM=
-github.com/jackc/pgx/v5 v5.4.3 h1:cxFyXhxlvAifxnkKKdlxv8XqUf59tDlYjnV5YYfsJJY=
-github.com/jackc/pgx/v5 v5.4.3/go.mod h1:Ig06C2Vu0t5qXC60W8sqIthScaEnFvojjj9dSljmHRA=
-github.com/jackc/puddle/v2 v2.2.1 h1:RhxXJtFG022u4ibrCSMSiu5aOq1i77R3OHKNJj77OAk=
-github.com/jackc/puddle/v2 v2.2.1/go.mod h1:vriiEXHvEE654aYKXXjOvZM39qJ0q+azkZFrfEOc3H4=
+github.com/jackc/pgservicefile v0.0.0-20240606120523-5a60cdf6a761 h1:iCEnooe7UlwOQYpKFhBabPMi4aNAfoODPEFNiAnClxo=
+github.com/jackc/pgservicefile v0.0.0-20240606120523-5a60cdf6a761/go.mod h1:5TJZWKEWniPve33vlWYSoGYefn3gLQRzjfDlhSJ9ZKM=
+github.com/jackc/pgx/v5 v5.7.1 h1:x7SYsPBYDkHDksogeSmZZ5xzThcTgRz++I5E+ePFUcs=
+github.com/jackc/pgx/v5 v5.7.1/go.mod h1:e7O26IywZZ+naJtWWos6i6fvWK+29etgITqrqHLfoZA=
+github.com/jackc/puddle/v2 v2.2.2 h1:PR8nw+E/1w0GLuRFSmiioY6UooMp6KJv0/61nB7icHo=
+github.com/jackc/puddle/v2 v2.2.2/go.mod h1:vriiEXHvEE654aYKXXjOvZM39qJ0q+azkZFrfEOc3H4=
github.com/jmespath/go-jmespath v0.4.0 h1:BEgLn5cpjn8UN1mAw4NjwDrS35OdebyEtFe+9YPoQUg=
github.com/jmespath/go-jmespath v0.4.0/go.mod h1:T8mJZnbsbmF+m6zOOFylbeCJqk5+pHWvzYPziyZiYoo=
github.com/pmezard/go-difflib v1.0.0 h1:4DBwDE0NGyQoBHbLQYPwSUPoCMWR5BEzIk/f1lZbAQM=
github.com/pmezard/go-difflib v1.0.0/go.mod h1:iKH77koFhYxTK1pcRnkKkqfTogsbg7gZNVY4sRDYZ/4=
github.com/sendgrid/rest v2.6.9+incompatible h1:1EyIcsNdn9KIisLW50MKwmSRSK+ekueiEMJ7NEoxJo0=
github.com/sendgrid/rest v2.6.9+incompatible/go.mod h1:kXX7q3jZtJXK5c5qK83bSGMdV6tsOE70KbHoqJls4lE=
-github.com/sendgrid/sendgrid-go v3.13.0+incompatible h1:HZrzc06/QfBGesY9o3n1lvBrRONA+57rbDRKet7plos=
-github.com/sendgrid/sendgrid-go v3.13.0+incompatible/go.mod h1:QRQt+LX/NmgVEvmdRw0VT/QgUn499+iza2FnDca9fg8=
+github.com/sendgrid/sendgrid-go v3.16.0+incompatible h1:i8eE6IMkiCy7vusSdacHHSBUpXyTcTXy/Rl9N9aZ/Qw=
+github.com/sendgrid/sendgrid-go v3.16.0+incompatible/go.mod h1:QRQt+LX/NmgVEvmdRw0VT/QgUn499+iza2FnDca9fg8=
github.com/stretchr/objx v0.1.0/go.mod h1:HFkY916IF+rwdDfMAkV7OtwuqBVzrE8GR6GFx+wExME=
github.com/stretchr/testify v1.3.0/go.mod h1:M5WIy9Dh21IEIfnGCwXGc5bZfKNJtfHm1UVUgZn+9EI=
github.com/stretchr/testify v1.7.0/go.mod h1:6Fq8oRcR53rry900zMqJjRRixrwX3KX962/h/Wwjteg=
github.com/stretchr/testify v1.8.1 h1:w7B6lhMri9wdJUVmEZPGGhZzrYTPvgJArz7wNPgYKsk=
github.com/stretchr/testify v1.8.1/go.mod h1:w2LPCIKwWwSfY2zedu0+kehJoqGctiVI29o6fzry7u4=
github.com/tidwall/gjson v1.14.2/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
-github.com/tidwall/gjson v1.16.0 h1:SyXa+dsSPpUlcwEDuKuEBJEz5vzTvOea+9rjyYodQFg=
-github.com/tidwall/gjson v1.16.0/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
+github.com/tidwall/gjson v1.18.0 h1:FIDeeyB800efLX89e5a8Y0BNH+LOngJyGrIWxG2FKQY=
+github.com/tidwall/gjson v1.18.0/go.mod h1:/wbyibRr2FHMks5tjHJ5F8dMZh3AcwJEMf5vlfC0lxk=
github.com/tidwall/match v1.1.1 h1:+Ho715JplO36QYgwN9PGYNhgZvoUSc9X2c80KVTi+GA=
github.com/tidwall/match v1.1.1/go.mod h1:eRSPERbgtNPcGhD8UCthc6PmLEQXEWd3PRB5JTxsfmM=
github.com/tidwall/pretty v1.2.0/go.mod h1:ITEVvHYasfjBbM0u2Pg8T2nJnzm8xPwvNhhsoaGGjNU=
@@ -49,16 +48,16 @@ github.com/tidwall/pretty v1.2.1 h1:qjsOFOWWQl+N3RsoF5/ssm1pHmJJwhjlSbZ51I6wMl4=
github.com/tidwall/pretty v1.2.1/go.mod h1:ITEVvHYasfjBbM0u2Pg8T2nJnzm8xPwvNhhsoaGGjNU=
github.com/tidwall/sjson v1.2.5 h1:kLy8mja+1c9jlljvWTlSazM7cKDRfJuR/bOJhcY5NcY=
github.com/tidwall/sjson v1.2.5/go.mod h1:Fvgq9kS/6ociJEDnK0Fk1cpYF4FIW6ZF7LAe+6jwd28=
-golang.org/x/crypto v0.13.0 h1:mvySKfSWJ+UKUii46M40LOvyWfN0s2U+46/jDd0e6Ck=
-golang.org/x/crypto v0.13.0/go.mod h1:y6Z2r+Rw4iayiXXAIxJIDAJ1zMW4yaTpebo8fPOliYc=
-golang.org/x/mod v0.12.0 h1:rmsUpXtvNzj340zd98LZ4KntptpfRHwpFOHG188oHXc=
-golang.org/x/mod v0.12.0/go.mod h1:iBbtSCu2XBx23ZKBPSOrRkjjQPZFPuis4dIYUhu/chs=
-golang.org/x/sync v0.3.0 h1:ftCYgMx6zT/asHUrPw8BLLscYtGznsLAnjq5RH9P66E=
-golang.org/x/sync v0.3.0/go.mod h1:FU7BRWz2tNW+3quACPkgCx/L+uEAv1htQ0V83Z9Rj+Y=
-golang.org/x/text v0.13.0 h1:ablQoSUd0tRdKxZewP80B+BaqeKJuVhuRxj/dkrun3k=
-golang.org/x/text v0.13.0/go.mod h1:TvPlkZtksWOMsz7fbANvkp4WM8x/WCo/om8BMLbz+aE=
-golang.org/x/time v0.3.0 h1:rg5rLMjNzMS1RkNLzCG38eapWhnYLFYXDXj2gOlr8j4=
-golang.org/x/time v0.3.0/go.mod h1:tRJNPiyCQ0inRvYxbN9jk5I+vvW/OXSQhTDSoE431IQ=
+golang.org/x/crypto v0.28.0 h1:GBDwsMXVQi34v5CCYUm2jkJvu4cbtru2U4TN2PSyQnw=
+golang.org/x/crypto v0.28.0/go.mod h1:rmgy+3RHxRZMyY0jjAJShp2zgEdOqj2AO7U0pYmeQ7U=
+golang.org/x/mod v0.21.0 h1:vvrHzRwRfVKSiLrG+d4FMl/Qi4ukBCE6kZlTUkDYRT0=
+golang.org/x/mod v0.21.0/go.mod h1:6SkKJ3Xj0I0BrPOZoBy3bdMptDDU9oJrpohJ3eWZ1fY=
+golang.org/x/sync v0.8.0 h1:3NFvSEYkUoMifnESzZl15y791HH1qU2xm6eCJU5ZPXQ=
+golang.org/x/sync v0.8.0/go.mod h1:Czt+wKu1gCyEFDUtn0jG5QVvpJ6rzVqr5aXyt9drQfk=
+golang.org/x/text v0.19.0 h1:kTxAhCbGbxhK0IwgSKiMO5awPoDQ0RpfiVYBfK860YM=
+golang.org/x/text v0.19.0/go.mod h1:BuEKDfySbSR4drPmRPG/7iBdf8hvFMuRexcpahXilzY=
+golang.org/x/time v0.7.0 h1:ntUhktv3OPE6TgYxXWv9vKvUSJyIFJlyohwbkEwPrKQ=
+golang.org/x/time v0.7.0/go.mod h1:3BpzKBy/shNhVucY/MWOyx10tF3SFh9QdLuxbVysPQM=
gopkg.in/check.v1 v0.0.0-20161208181325-20d25e280405/go.mod h1:Co6ibVJAznAaIkqp8huTwlJQCZ016jof/cbN4VW5Yz0=
gopkg.in/yaml.v3 v3.0.0-20200313102051-9f266ea9e77c/go.mod h1:K4uyk7z7BCEPqu6E+C64Yfv1cQ7kz7rIZviUmN+EgEM=
gopkg.in/yaml.v3 v3.0.1 h1:fxVm/GzAzEWqLHuvctI91KS9hhNmmWOoWu0XTYJS7CA=
diff --git a/cmd/stress/go.work b/cmd/stress/go.work
new file mode 100644
index 0000000..5fb1412
--- /dev/null
+++ b/cmd/stress/go.work
@@ -0,0 +1,6 @@
+go 1.23.2
+
+use (
+ .
+ ../..
+)
diff --git a/cmd/stress/go.work.sum b/cmd/stress/go.work.sum
new file mode 100644
index 0000000..3ea587c
--- /dev/null
+++ b/cmd/stress/go.work.sum
@@ -0,0 +1,56 @@
+github.com/creack/pty v1.1.9 h1:uDmaGzcdjhF4i/plgjmEsriH11Y0o7RKapEf/LDaM3w=
+github.com/creack/pty v1.1.9/go.mod h1:oKZEueFk5CKHvIhNR5MUki03XCEU+Q6VDXinZuGJ33E=
+github.com/google/go-cmp v0.6.0 h1:ofyhxvXcZhMsU5ulbFiLKl/XBFqE1GSq7atu8tAmTRI=
+github.com/google/go-cmp v0.6.0/go.mod h1:17dUlkBOakJ0+DkrSSNjCkIjxS6bF9zb3elmeNGIjoY=
+github.com/kr/pretty v0.1.0/go.mod h1:dAy3ld7l9f0ibDNOQOHHMYYIIbhfbHSm3C4ZsoJORNo=
+github.com/kr/pretty v0.2.1/go.mod h1:ipq/a2n7PKx3OHsz4KJII5eveXtPO4qwEXGdVfWzfnI=
+github.com/kr/pretty v0.3.0 h1:WgNl7dwNpEZ6jJ9k1snq4pZsg7DOEN8hP9Xw0Tsjwk0=
+github.com/kr/pretty v0.3.0/go.mod h1:640gp4NfQd8pI5XOwp5fnNeVWj67G7CFk/SaSQn7NBk=
+github.com/kr/pty v1.1.1 h1:VkoXIwSboBpnk99O/KFauAEILuNHv5DVFKZMBN/gUgw=
+github.com/kr/pty v1.1.1/go.mod h1:pFQYn66WHrOpPYNljwOMqo10TkYh1fy3cYio2l3bCsQ=
+github.com/kr/text v0.1.0/go.mod h1:4Jbv+DJW3UT/LiOwJeYQe1efqtUx/iVham/4vfdArNI=
+github.com/kr/text v0.2.0 h1:5Nx0Ya0ZqY2ygV366QzturHI13Jq95ApcVaJBhpS+AY=
+github.com/kr/text v0.2.0/go.mod h1:eLer722TekiGuMkidMxC/pM04lWEeraHUUmBw8l2grE=
+github.com/rogpeppe/go-internal v1.6.1 h1:/FiVV8dS/e+YqF2JvO3yXRFbBLTIuSDkuC7aBOAvL+k=
+github.com/rogpeppe/go-internal v1.6.1/go.mod h1:xXDCJY+GAPziupqXw64V24skbSoqbTEfhy4qGm1nDQc=
+github.com/stretchr/objx v0.1.0 h1:4G4v2dO3VZwixGIRoQ5Lfboy6nUhCyYzaqnIAPPhYs4=
+github.com/stretchr/objx v0.4.0/go.mod h1:YvHI0jy2hoMjB+UWwv71VJQ9isScKT/TqJzVSSt89Yw=
+github.com/stretchr/objx v0.5.0 h1:1zr/of2m5FGMsad5YfcqgdqdWrIhu+EBEJRhR1U7z/c=
+github.com/stretchr/objx v0.5.0/go.mod h1:Yh+to48EsGEfYuaHDzXPcE3xhTkx73EhmCGUpEOglKo=
+github.com/stretchr/testify v1.7.1/go.mod h1:6Fq8oRcR53rry900zMqJjRRixrwX3KX962/h/Wwjteg=
+github.com/stretchr/testify v1.8.0/go.mod h1:yNjHg4UonilssWZ8iaSj1OCr/vHnekPRkoO+kdMU+MU=
+github.com/yuin/goldmark v1.4.13 h1:fVcFKWvrslecOb/tg+Cc05dkeYx540o0FuFt3nUVDoE=
+github.com/yuin/goldmark v1.4.13/go.mod h1:6yULJ656Px+3vBD8DxQVa3kxgyrAnzto9xy5taEt/CY=
+golang.org/x/crypto v0.23.0/go.mod h1:CKFgDieR+mRhux2Lsu27y0fO304Db0wZe70UKqHu0v8=
+golang.org/x/crypto v0.27.0/go.mod h1:1Xngt8kV6Dvbssa53Ziq6Eqn0HqbZi5Z6R0ZpwQzt70=
+golang.org/x/mod v0.17.0/go.mod h1:hTbmBsO62+eylJbnUtE2MGJUyE7QWk4xUqPFrRgJ+7c=
+golang.org/x/net v0.10.0 h1:X2//UzNDwYmtCLn7To6G58Wr6f5ahEAQgKNzv9Y951M=
+golang.org/x/net v0.10.0/go.mod h1:0qNGK6F8kojg2nk9dLZ2mShWaEBan6FAoqfSigmmuDg=
+golang.org/x/net v0.25.0 h1:d/OCCoBEUq33pjydKrGQhw7IlUPI2Oylr+8qLx49kac=
+golang.org/x/net v0.25.0/go.mod h1:JkAGAh7GEvH74S6FOH42FLoXpXbE/aqXSrIQjXgsiwM=
+golang.org/x/sync v0.7.0/go.mod h1:Czt+wKu1gCyEFDUtn0jG5QVvpJ6rzVqr5aXyt9drQfk=
+golang.org/x/sys v0.12.0 h1:CM0HF96J0hcLAwsHPJZjfdNzs0gftsLfgKt57wWHJ0o=
+golang.org/x/sys v0.12.0/go.mod h1:oPkhp1MJrh7nUepCBck5+mAzfO9JrbApNNgaTdGDITg=
+golang.org/x/sys v0.20.0/go.mod h1:/VUhepiaJMQUp4+oa/7Zr1D23ma6VTLIYjOOTFZPUcA=
+golang.org/x/sys v0.26.0 h1:KHjCJyddX0LoSTb3J+vWpupP9p0oznkqVk/IfjymZbo=
+golang.org/x/sys v0.26.0/go.mod h1:/VUhepiaJMQUp4+oa/7Zr1D23ma6VTLIYjOOTFZPUcA=
+golang.org/x/telemetry v0.0.0-20240228155512-f48c80bd79b2 h1:IRJeR9r1pYWsHKTRe/IInb7lYvbBVIqOgsX/u0mbOWY=
+golang.org/x/telemetry v0.0.0-20240228155512-f48c80bd79b2/go.mod h1:TeRTkGYfJXctD9OcfyVLyj2J3IxLnKwHJR8f4D8a3YE=
+golang.org/x/term v0.12.0 h1:/ZfYdc3zq+q02Rv9vGqTeSItdzZTSNDmfTi0mBAuidU=
+golang.org/x/term v0.12.0/go.mod h1:owVbMEjm3cBLCHdkQu9b1opXd4ETQWc3BhuQGKgXgvU=
+golang.org/x/term v0.20.0/go.mod h1:8UkIAJTvZgivsXaD6/pH6U9ecQzZ45awqEOzuCvwpFY=
+golang.org/x/term v0.25.0 h1:WtHI/ltw4NvSUig5KARz9h521QvRC8RmF/cuYqifU24=
+golang.org/x/term v0.25.0/go.mod h1:RPyXicDX+6vLxogjjRxjgD2TKtmAO6NZBsBRfrOLu7M=
+golang.org/x/text v0.15.0/go.mod h1:18ZOQIKpY8NJVqYksKHtTdi31H5itFRjB5/qKTNYzSU=
+golang.org/x/text v0.18.0/go.mod h1:BuEKDfySbSR4drPmRPG/7iBdf8hvFMuRexcpahXilzY=
+golang.org/x/time v0.5.0/go.mod h1:3BpzKBy/shNhVucY/MWOyx10tF3SFh9QdLuxbVysPQM=
+golang.org/x/tools v0.6.0 h1:BOw41kyTf3PuCW1pVQf8+Cyg8pMlkYB1oo9iJ6D/lKM=
+golang.org/x/tools v0.6.0/go.mod h1:Xwgl3UAJ/d3gWutnCtw505GrjyAbvKui8lOU390QaIU=
+golang.org/x/tools v0.13.0/go.mod h1:HvlwmtVNQAhOuCjW7xxvovg8wbNq7LwfXh/k7wXUl58=
+golang.org/x/tools v0.21.1-0.20240508182429-e35e4ccd0d2d h1:vU5i/LfpvrRCpgM/VPfJLg5KjxD3E+hfT1SH+d9zLwg=
+golang.org/x/tools v0.21.1-0.20240508182429-e35e4ccd0d2d/go.mod h1:aiJjzUbINMkxbQROHiO6hDPo2LHcIPhhQsa9DLh0yGk=
+gopkg.in/check.v1 v1.0.0-20180628173108-788fd7840127/go.mod h1:Co6ibVJAznAaIkqp8huTwlJQCZ016jof/cbN4VW5Yz0=
+gopkg.in/check.v1 v1.0.0-20201130134442-10cb98267c6c h1:Hei/4ADfdWqJk1ZMxUNpqntNwaWcugrBjAiHlqqRiVk=
+gopkg.in/check.v1 v1.0.0-20201130134442-10cb98267c6c/go.mod h1:JHkPIbrfpd72SG/EVd6muEfDQjcINNoR0C8j2r3qZ4Q=
+gopkg.in/errgo.v2 v2.1.0 h1:0vLT13EuvQ0hNvakwLuFZ/jYrLp5F3kcWHXdRggjCE8=
+gopkg.in/errgo.v2 v2.1.0/go.mod h1:hNsd1EY+bozCKY1Ytp96fpM3vjJbqLJn88ws8XvfDNI=
diff --git a/cmd/stress/link.example.json b/cmd/stress/link.example.json
index 1395e88..1284f2c 100644
--- a/cmd/stress/link.example.json
+++ b/cmd/stress/link.example.json
@@ -1,13 +1,13 @@
{
- "linkArgs": {
- "jwtCreateArgs": {
- "jwtClaims": {
+ "magicLinkCreateParams": {
+ "jwtCreateParams": {
+ "claims": {
"foo": "bar"
},
- "jwtLifespanSeconds": 0
+ "lifespanSeconds": 0
},
- "linkLifespan": 0,
+ "lifespanSeconds": 0,
"redirectQueryKey": "",
- "redirectUrl": "https://jwtdebug.micahparks.com"
+ "redirectURL": "https://jwtdebug.micahparks.com"
}
}
diff --git a/cmd/stress/main.go b/cmd/stress/main.go
index fe902b5..308a028 100644
--- a/cmd/stress/main.go
+++ b/cmd/stress/main.go
@@ -11,15 +11,16 @@ import (
"strings"
"time"
- "github.com/MicahParks/magiclinksdev/mldtest"
"golang.org/x/sync/errgroup"
+ "github.com/MicahParks/magiclinksdev/mldtest"
+
mld "github.com/MicahParks/magiclinksdev"
"github.com/MicahParks/magiclinksdev/network"
"github.com/MicahParks/magiclinksdev/network/middleware"
)
-//go:embed link.prod.json
+//go:embed link.example.json
var linkJSON []byte
func main() {
@@ -35,7 +36,7 @@ func main() {
)
exit(ctx, l, time.Now(), 1)
}
- u, err = u.Parse("/api/v1/" + network.PathLinkCreate)
+ u, err = u.Parse("/api/v2/" + network.PathMagicLinkCreate)
if err != nil {
l.ErrorContext(ctx, "Failed to parse URL.",
mld.LogErr, err,
diff --git a/compose.yaml b/compose.yaml
index 2ca0caf..f14f6cd 100644
--- a/compose.yaml
+++ b/compose.yaml
@@ -1,4 +1,3 @@
-version: "3.8"
services:
magiclinksdev:
image: "micahparks/magiclinksdevnop"
diff --git a/config.quickstart.json b/config.quickstart.json
index 193f20d..bd813db 100644
--- a/config.quickstart.json
+++ b/config.quickstart.json
@@ -1,14 +1,14 @@
{
"server": {
- "adminConfig": [
+ "adminCreateParams": [
{
"apiKey": "40084740-0bc3-455d-b298-e23a31561580",
"aud": "ad9e9d84-92ea-4f07-bac9-5d898d59c83b",
"uuid": "1e079d6d-a8b9-4065-aa8d-86906accd211",
- "serviceAccountCreateArgs": {}
+ "serviceAccountCreateParams": {}
}
],
- "baseURL": "http://localhost:8080/api/v1/",
+ "baseURL": "http://localhost:8080/api/v2/",
"iss": "http://localhost:8080"
},
"storage": {
diff --git a/config.test.json b/config.test.json
index 407a213..c241f92 100644
--- a/config.test.json
+++ b/config.test.json
@@ -9,15 +9,15 @@
"refillRate": 0
},
"server": {
- "adminConfig": [
+ "adminCreateParams": [
{
"apiKey": "40084740-0bc3-455d-b298-e23a31561580",
"aud": "ad9e9d84-92ea-4f07-bac9-5d898d59c83b",
"uuid": "1e079d6d-a8b9-4065-aa8d-86906accd211",
- "serviceAccountCreateArgs": {}
+ "serviceAccountCreateParams": {}
}
],
- "baseURL": "http://localtest/api/v1/",
+ "baseURL": "http://localtest/api/v2/",
"iss": "testIssuer",
"jwks": {
"ignoreDefault": false
diff --git a/config/config.go b/config/config.go
index 85249c1..9f5049b 100644
--- a/config/config.go
+++ b/config/config.go
@@ -24,7 +24,7 @@ type LogLevel string
// Config is the configuration for the magiclinksdev server.
type Config struct {
- AdminConfig []model.AdminCreateArgs `json:"adminConfig"`
+ AdminCreateParams []model.AdminCreateParams `json:"adminCreateParams"`
BaseURL *jt.JSONType[*url.URL] `json:"baseURL"`
Iss string `json:"iss"`
JWKS JWKS `json:"jwks"`
diff --git a/constants.go b/constants.go
index c2e4d49..0902b6a 100644
--- a/constants.go
+++ b/constants.go
@@ -1,8 +1,15 @@
package magiclinksdev
+import (
+ "errors"
+ "time"
+)
+
const (
// ContentTypeJSON is the content type for JSON.
ContentTypeJSON = "application/json"
+ // DefaultOTPLength is the default length for OTPs.
+ DefaultOTPLength = 6
// DefaultRelativePathRedirect is the default relative path for redirecting.
DefaultRelativePathRedirect = "redirect"
// HeaderContentType is the content type header.
@@ -15,6 +22,8 @@ const (
LogRequestBody = "requestBody"
// LogResponseBody is key for logging the response body.
LogResponseBody = "responseBody"
+ // Over250Years is the maximum duration for this project. Restriction derived from Golang's time.Duration.
+ Over250Years = 250 * 366 * 24 * time.Hour
// ResponseInternalServerError is the response for internal server errors.
ResponseInternalServerError = "Internal server error."
// ResponseTooManyRequests is the response for too many requests.
@@ -23,6 +32,10 @@ const (
ResponseUnauthorized = "Unauthorized."
)
+var (
+ ErrParams = errors.New("invalid parameters")
+)
+
func Ptr[T any](v T) *T {
return &v
}
diff --git a/email/html.gohtml b/email/html.gohtml
deleted file mode 100644
index 5cce72b..0000000
--- a/email/html.gohtml
+++ /dev/null
@@ -1,166 +0,0 @@
-{{- /*gotype: github.com/MicahParks/magiclinksdev/email.TemplateData*/ -}}
-
-
-
-
-
-
-
-
-
- {{.Meta.MSOHead}}
-