This troubleshooting guide covers failure investigation techniques, common errors for the credential types in the Azure Identity library for .NET, and mitigation steps to resolve these errors.
- Handle Azure Identity exceptions
- Find relevant information in exception messages
- Enable and configure logging
- Troubleshoot DefaultAzureCredential authentication issues
- Troubleshoot EnvironmentCredential authentication issues
- Troubleshoot ClientSecretCredential authentication issues
- Troubleshoot ClientCertificateCredential authentication issues
- Troubleshoot ClientAssertionCredential authentication issues
- Troubleshoot UsernamePasswordCredential authentication issues
- Troubleshoot WorkloadIdentityCredential authentication issues
- Troubleshoot ManagedIdentityCredential authentication issues
- Troubleshoot VisualStudioCodeCredential authentication issues
- Troubleshoot VisualStudioCredential authentication issues
- Troubleshoot AzureDeveloperCliCredential authentication issues
- Troubleshoot AzureCliCredential authentication issues
- Troubleshoot AzurePowerShellCredential authentication issues
- Troubleshoot multi-tenant authentication issues
- Troubleshoot Web Account Manager (WAM) brokered authentication issues
- Troubleshoot AzurePipelinesCredential authentication issues
- Get additional help
Exceptions arising from authentication errors can be raised on any service client method that makes a request to the service. This is because the token is requested from the credential on:
- The first call to the service.
- Any subsequent requests to the service that need to refresh the token.
To distinguish these failures from failures in the service client, Azure Identity classes raise the AuthenticationFailedException with details describing the source of the error in the exception message and possibly the error message. Depending on the application, these errors may or may not be recoverable.
using Azure.Identity;
using Azure.Security.KeyVault.Secrets;
// Create a secret client using the DefaultAzureCredential
var client = new SecretClient(new Uri("https://myvault.vault.azure.net/"), new DefaultAzureCredential());
try
{
KeyVaultSecret secret = await client.GetSecretAsync("secret1");
}
catch (AuthenticationFailedException e)
{
Console.WriteLine($"Authentication Failed. {e.Message}");
}The CredentialUnavailableException is a special exception type derived from AuthenticationFailedException. This exception type is used to indicate that the credential can't authenticate in the current environment, due to lack of required configuration or setup. This exception is also used as a signal to chained credential types, such as DefaultAzureCredential and ChainedTokenCredential, that the chained credential should continue to try other credential types later in the chain.
Calls to service clients resulting in RequestFailedException with a StatusCode of 401 or 403 often indicate the caller doesn't have sufficient permissions for the specified API. Check the service documentation to determine which RBAC roles are needed for the specific request, and ensure the authenticated user or service principal have been granted the appropriate roles on the resource.
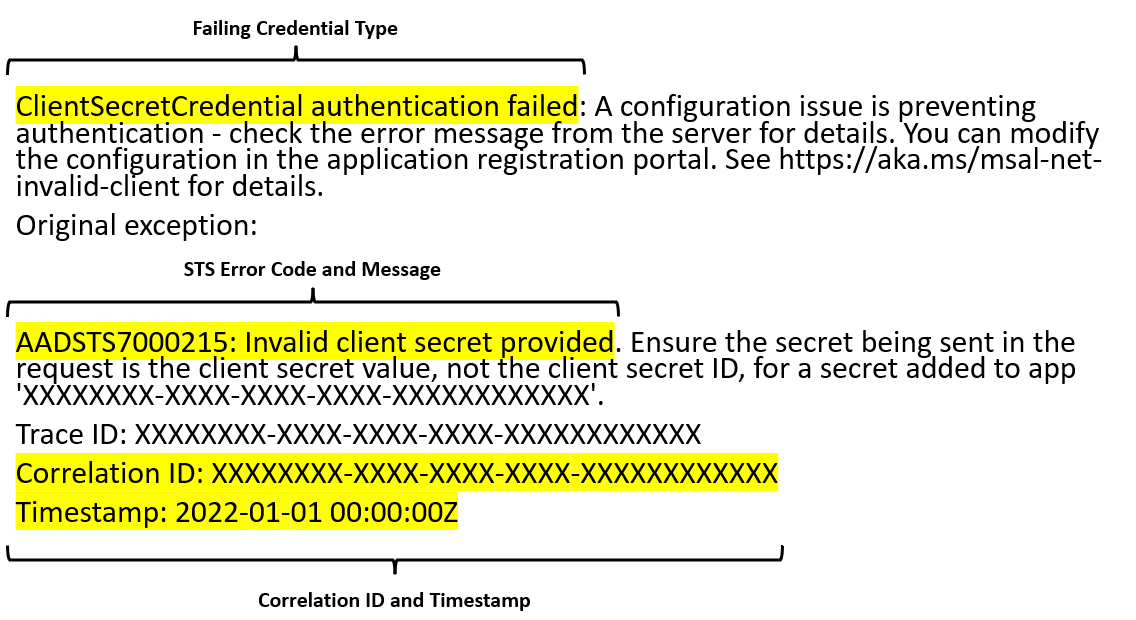
AuthenticationFailedException is thrown when unexpected errors occurred while a credential is authenticating. This can include errors received from requests to the Microsoft Entra STS and often contains information helpful to diagnosis. Consider the following AuthenticationFailedException message.
This error contains several pieces of information:
-
Failing Credential Type: The type of credential that failed to authenticate. This can be helpful when diagnosing issues with chained credential types such as
DefaultAzureCredentialorChainedTokenCredential. -
STS Error Code and Message: The error code and message returned from the Microsoft Entra STS. This can give insight into the specific reason the request failed. For instance, in this specific case because the provided client secret is incorrect. More information on STS error codes can be found here.
-
Correlation ID and Timestamp: The correlation ID and call Timestamp used to identify the request in server-side logs. This information can be useful to support engineers when diagnosing unexpected STS failures.
The Azure Identity library provides the same logging capabilities as the rest of the Azure SDK.
The simplest way to see the logs to help debug authentication issues is to enable the console logger.
// Set up a listener to monitor logged events.
using AzureEventSourceListener listener = AzureEventSourceListener.CreateConsoleLogger();All credentials can be configured with diagnostic options, in the same way as other clients in the SDK.
DefaultAzureCredentialOptions options = new
{
Diagnostics =
{
LoggedHeaderNames = { "x-ms-request-id" },
LoggedQueryParameters = { "api-version" },
IsLoggingContentEnabled = true
}
};CAUTION: Requests and responses in the Azure Identity library contain sensitive information. Precaution must be taken to protect logs when customizing the output to avoid compromising account security.
When troubleshooting authentication issues, you may also want to enable logging of sensitive information. To enable this type of logging, set the IsLoggingContentEnabled property to true. To only log details about the account that was used to attempt authentication and authorization, set the IsAccountIdentifierLoggingEnabled property to true:
DefaultAzureCredentialOptions options = new
{
Diagnostics =
{
LoggedHeaderNames = { "x-ms-request-id" },
LoggedQueryParameters = { "api-version" },
IsAccountIdentifierLoggingEnabled = true
}
};| Error | Description | Mitigation |
|---|---|---|
CredentialUnavailableException raised with message. "DefaultAzureCredential failed to retrieve a token from the included credentials." |
All credentials in the DefaultAzureCredential chain failed to retrieve a token, each throwing a CredentialUnavailableException. |
|
RequestFailedException raised from the client with a status code of 401 or 403 |
Authentication succeeded but the authorizing Azure service responded with a 401 (Authenticate) or 403 (Forbidden) status code. This error can often be caused by the DefaultAzureCredential authenticating an account other than the intended or that the intended account doesn't have the correct permissions or roles assigned. |
|
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| Environment variables aren't fully configured. | A valid combination of environment variables wasn't set. | Ensure the appropriate environment variables are set prior to application startup for the intended authentication method.
|
| Password protection for PEM encoded certificates is not supported. | AZURE_CLIENT_CERTIFICATE_PASSWORD was set when using a PEM encoded certificate. |
Re-encode the client certificate to a password protected PFX (PKCS12) certificate, or a PEM certificate without password protection. |
AuthenticationFailedException
| Error Code | Issue | Mitigation |
|---|---|---|
| AADSTS7000215 | An invalid client secret was provided. | Ensure the clientSecret provided when constructing the credential is valid. If unsure, create a new client secret using the Azure portal. Details on creating a new client secret can be found here. |
| AADSTS7000222 | An expired client secret was provided. | Create a new client secret using the Azure portal. Details on creating a new client secret can be found here. |
| AADSTS700016 | The specified application wasn't found in the specified tenant. | Ensure the specified clientId and tenantId are correct for your application registration. For multi-tenant apps, ensure the application has been added to the desired tenant by a tenant admin. To add a new application in the desired tenant, follow the instructions here. |
AuthenticationFailedException
| Error Code | Description | Mitigation |
|---|---|---|
| AADSTS700027 | Client assertion contains an invalid signature. | Ensure the specified certificate has been uploaded to the Microsoft Entra application registration. Instructions for uploading certificates to the application registration can be found here. |
| AADSTS700016 | The specified application wasn't found in the specified tenant. | Ensure the specified clientId and tenantId are correct for your application registration. For multi-tenant apps, ensure the application has been added to the desired tenant by a tenant admin. To add a new application in the desired tenant, follow the instructions here. |
AuthenticationFailedException
| Error Code | Description | Mitigation |
|---|---|---|
| AADSTS700021 | Client assertion application identifier doesn't match 'client_id' parameter. Review the documentation at Microsoft Identity platform application authentication certificate credentials. | Ensure the JWT assertion created has the correct values specified for the sub and issuer value of the payload, both of these should have the value be equal to clientId. Refer to the documentation for client assertion format. |
| AADSTS700023 | Client assertion audience claim doesn't match Realm issuer. Review the documentation at Microsoft Identity platform application authentication certificate credentials. | Ensure the audience aud field in the JWT assertion created has the correct value for the audience specified in the payload. This should be set to https://login.microsoftonline.com/{tenantId}/v2. |
| AADSTS50027 | JWT token is invalid or malformed. | Ensure the JWT assertion token is in the valid format. Refer to the documentation for client assertion format. |
AuthenticationFailedException
| Error Code | Issue | Mitigation |
|---|---|---|
| AADSTS50126 | The provided username or password is invalid | Ensure the username and password provided when constructing the credential are valid. |
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
CredentialUnavailableException raised with message. "WorkloadIdentityCredential authentication unavailable. The workload options are not fully configured." |
The WorkloadIdentityCredential requires ClientId, TenantId and TokenFilePath to authenticate with Microsoft Entra ID. |
|
| The workload options are not fully configured. | The workload identity configuration wasn't provided in environment variables or through WorkloadIdentityCredentialOptions. |
Ensure the appropriate environment variables are set prior to application startup or are specified in code.
|
The ManagedIdentityCredential is designed to work on various Azure hosts that provide managed identity. Configuring the managed identity and troubleshooting failures varies from hosts. The following table lists the Azure hosts that can be assigned a managed identity and are supported by the ManagedIdentityCredential.
| Host Environment | ||
|---|---|---|
| Azure App Service and Azure Functions | Configuration | Troubleshooting |
| Azure Arc | Configuration | |
| Azure Kubernetes Service | Configuration | Troubleshooting |
| Azure Service Fabric | Configuration | |
| Azure Virtual Machines and Scale Sets | Configuration | Troubleshooting |
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| The requested identity hasn't been assigned to this resource. | The IMDS endpoint responded with a status code of 400, indicating the requested identity isn't assigned to the VM. | If using a user assigned identity, ensure the specified clientId is correct.If using a system assigned identity, make sure it has been enabled properly. Instructions to enable the system assigned identity on an Azure VM can be found here. |
| The request failed due to a gateway error. | The request to the IMDS endpoint failed due to a gateway error, 502 or 504 status code. | IMDS doesn't support calls via proxy or gateway. Disable proxies or gateways running on the VM for calls to the IMDS endpoint http://169.254.169.254/ |
| No response received from the managed identity endpoint. | No response was received for the request to IMDS or the request timed out. |
|
| Multiple attempts failed to obtain a token from the managed identity endpoint. | Retries to retrieve a token from the IMDS endpoint have been exhausted. |
|
If you have access to the VM, you can verify the managed identity endpoint is available via the command line using curl.
curl 'http://169.254.169.254/metadata/identity/oauth2/token?resource=https://management.core.windows.net&api-version=2018-02-01' -H "Metadata: true"Note that output of this command will contain a valid access token, and SHOULD NOT BE SHARED to avoid compromising account security.
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| ManagedIdentityCredential authentication unavailable. | The environment variables configured by the App Services host weren't present. |
|
If you have access to SSH into the App Service, you can verify managed identity is available in the environment. First ensure the environment variables MSI_ENDPOINT and MSI_SECRET have been set in the environment. Then you can verify the managed identity endpoint is available using curl.
curl 'http://169.254.169.254/metadata/identity/oauth2/token?resource=https://management.core.windows.net&api-version=2018-02-01' -H "Metadata: true"Note that the output of this command will contain a valid access token, and SHOULD NOT BE SHARED to avoid compromising account security.
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| No Managed Identity endpoint found | The application attempted to authenticate before an identity was assigned to its pod | Verify the pod is labeled correctly. This error also occurs when a correctly labeled pod authenticates before the identity is ready. To prevent initialization races, configure NMI to set the Retry-After header in its responses (see Pod Identity documentation). |
It's a known issue that
VisualStudioCodeCredentialdoesn't work with Azure Account extension versions newer than 0.9.11. A long-term fix to this problem is in progress. In the meantime, consider authenticating via the Azure CLI.
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| Failed To Read VS Code CredentialsORAuthenticate via Azure Tools plugin in VS Code | No Azure account information was found in the VS Code configuration. |
|
| MSAL Interaction Required Error | The VisualStudioCodeCredential was able to read the cached credentials from the cache but the cached token is likely expired. |
Log into the Azure Account extension via View > Command Palette to execute the Azure: Sign In command in the VS Code IDE. |
| ADFS tenant not supported | ADFS tenants aren't currently supported by Visual Studio Azure Service Authentication. |
Use credentials from a supported cloud when authenticating with Visual Studio. The supported clouds are:
|
| AADSTS50020 | User account '{EmailHidden}' from identity provider 'live.com' doesn't exist in tenant 'Microsoft Services' and cannot access the application '04f0c124-f2bc-4f59-8241-bf6df9866bbd'(VS with native MSA) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Microsoft Entra user account. | Specify a TenantId value that corresponds to the resource to which you're authenticating in the VisualStudioCredentialOptions (or the DefaultAzureCredentialOptions if you're using DefaultAzureCredential). |
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| Failed To Read CredentialsORAuthenticate via Azure Service Authentication | The VisualStudioCredential failed to retrieve a token from the Visual Studio authentication utility Microsoft.Asal.TokenService.exe. |
|
| ADFS tenant not supported | ADFS tenants aren't currently supported by Visual Studio Azure Service Authentication. |
Use credentials from a supported cloud when authenticating with Visual Studio. The supported clouds are:
|
| AADSTS65001: The user or administrator has not consented to use the application with ID '04f0c124-f2bc-4f59-8241-bf6df9866bbd' named 'Visual Studio'. | The user needs to add Visual Studio as an authorized application to their Azure resource. | Follow the instructions at Pre-authorize your client application. |
| AADSTS65002: Consent between first party application '04f0c124-f2bc-4f59-8241-bf6df9866bbd' and first party resource '' must be configured via preauthorization - applications owned and operated by Microsoft must get approval from the API owner before requesting tokens for that API. | The client application used by Visual Studio is not yet pre-authorized for the Azure resource mentioned in the error. | Follow the instructions under the Pre-authorization issues section of this document. |
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| Azure CLI not installed | The Azure CLI isn't installed or couldn't be found. |
|
| Please run 'az login' to set up account | No account is currently logged into the Azure CLI, or the login has expired. |
|
You can manually verify that the Azure CLI is properly authenticated and can obtain tokens. First, use the account command to verify the account that is currently logged in to the Azure CLI.
az account showOnce you've verified the Azure CLI is using the correct account, you can validate that it's able to obtain tokens for this account.
az account get-access-token --output json --resource https://management.core.windows.netNote that output of this command will contain a valid access token, and SHOULD NOT BE SHARED to avoid compromising account security.
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| Azure Developer CLI not installed | The Azure Developer CLI isn't installed or couldn't be found. |
|
| Please run 'azd login' to set up account | No account is currently logged into the Azure Developer CLI, or the login has expired. |
|
You can manually verify that the Azure Developer CLI is properly authenticated and can obtain tokens. First, use the config command to verify the account that is currently logged in to the Azure Developer CLI.
azd config listOnce you've verified the Azure Developer CLI is using correct account, you can validate that it's able to obtain tokens for this account.
azd auth token --output json --scope https://management.core.windows.net/.defaultNote that output of this command will contain a valid access token, and SHOULD NOT BE SHARED to avoid compromising account security.
CredentialUnavailableException
| Error Message | Description | Mitigation |
|---|---|---|
| PowerShell isn't installed. | No local installation of PowerShell was found. | Ensure that PowerShell is properly installed on the machine. Instructions for installing PowerShell can be found here. |
| Az.Account module >= 2.2.0 isn't installed. | The Az.Account module needed for authentication in Azure PowerShell isn't installed. | Install the latest Az.Account module. Installation instructions can be found here. |
| Please run 'Connect-AzAccount' to set up account. | No account is currently logged into Azure PowerShell. |
|
You can manually verify that Azure PowerShell is properly authenticated, and can obtain tokens. First, use the Get-AzContext command to verify the account that is currently logged in to the Azure CLI.
PS C:\> Get-AzContext
Name Account SubscriptionName Environment TenantId
---- ------- ---------------- ----------- --------
Subscription1 (xxxxxxxx-xxxx-xxxx-xxx... test@outlook.com Subscription1 AzureCloud xxxxxxxx-x...
Once you've verified Azure PowerShell is using correct account, validate that it's able to obtain tokens for this account:
Get-AzAccessToken -ResourceUrl "https://management.core.windows.net"Note that output of this command will contain a valid access token, and SHOULD NOT BE SHARED to avoid compromising account security.
AuthenticationFailedException
| Error Message | Description | Mitigation |
|---|---|---|
| The current credential is not configured to acquire tokens for tenant | The application must configure the credential to allow acquiring tokens from the requested tenant. | Add the requested tenant ID it to the AdditionallyAllowedTenants on the credential options, or add "*" to AdditionallyAllowedTenants to allow acquiring tokens for any tenant.This exception was added as part of functional a breaking change to multi tenant authentication in version 1.7.0. Users experiencing this error after upgrading can find details on the change and migration in BREAKING_CHANGES.md. |
| Error Message | Description | Mitigation |
|---|---|---|
| The current credential is not configured to acquire tokens for tenant | The application must configure the credential to allow token acquisition from the requested tenant. |
Make one of the following changes in your app:
This exception was added as part of a breaking change to multi-tenant authentication in version |
| Error Message | Description | Mitigation |
|---|---|---|
| AADSTS50011 | The application is missing the expected redirect URI. | Ensure that one of redirect URIs registered for the Microsoft Entra application matches the following URI pattern: ms-appx-web://Microsoft.AAD.BrokerPlugin/{client_id} |
When using InteractiveBrowserCredential, by default, only the Microsoft Entra account is listed:
If you choose "Use another account" and type in an MSA outlook.com account, it fails:
Since version 1.0.0-beta.4 of Azure.Identity.Broker, you can set the IsLegacyMsaPassthroughEnabled property on InteractiveBrowserCredentialBrokerOptions or SharedTokenCacheCredentialBrokerOptions to true. MSA outlook.com accounts that are logged in to Windows are automatically listed:
You may also log in another MSA account by selecting "Microsoft account":
| Error Message | Description | Mitigation |
|---|---|---|
AADSTS900023: Specified tenant identifier <some tenant ID> is neither a valid DNS name, nor a valid external domain. |
The tenant ID passed to the credential is invalid. | Verify the tenant ID is valid. If the service connection was configured via a user-assigned managed identity, the tenant will be the one in which managed identity was registered. If the service connection is configured via a service principal, the tenant should be the one in which the Service Principal is registered. |
No service connection found with identifier <GUID> |
The service connection ID provided is incorrect. | Verify the serviceConnectionId provided. This parameter refers to the resourceId of the Azure Service Connection. It can also be found in the query string of the respective Service Connection's configuration page in Azure DevOps. More information about service connections can be found here |
| AzurePipelinesCredential: Authentication Failed. OIDC token not found in response. Status Code: 401 (Unauthorized). | The system access token seems to be malformed when passed in as a parameter to the credential. | System.AccessToken is a required system variable in the Azure Pipelines task and should be provided in the pipeline task, as mentioned in the docs. Verify that the system access token value provided is the predefined variable in Azure Pipelines and isn't malformed. |
AzurePipelinesCredential: Authentication Failed. oidcToken field not detected in the response. Response = {"$id":"1","innerException":null,"message":"<ACTUAL ERROR MESSAGE>","typeName":"Microsoft.VisualStudio.Services.WebApi.VssInvalidPreviewVersionException, Microsoft.VisualStudio.Services.WebApi","typeKey":"VssInvalidPreviewVersionException","errorCode":0} |
When the OIDC token request fails, the OIDC token api throws an error. More details about the specific error are specified in the "message" field of the Response as shown above. | Mitigation will usually depend on the scenario based on what error message is being thrown. Make sure you use the recommended Azure Pipelines task. |
| CredentialUnavailableError: AzurePipelinesCredential is not available: Ensure that you're running this task in an Azure Pipeline so that following missing system variable(s) can be defined: SYSTEM_OIDCREQUESTURI is not set. | This code is not running inside of the Azure Pipelines Environment. You may be running this code locally or on some other environment. | This credential is only designed to run from inside the Azure Pipelines environment for the federated identity to work. |
| AuthenticationRequiredError: unauthorized_client: 700016 - AADSTS700016: Application with identifier 'clientId' was not found in the directory 'Microsoft'. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You may have sent your authentication request to the wrong tenant. | The clientId provided is invalid. |
Verify the client ID argument is valid. If the service connection's federated identity was registered via a user-assigned managed identity, the client ID of the managed identity should be provided. If the service connection's federated identity is registered via a Service Principal, the Application (client) ID from your app registration should be provided. |
Additional information on ways to reach out for support can be found in the SUPPORT.md at the root of the repo.